AWS S3 Buckets are a key component of Amazon’s simple storage service. They hold the data stored within the service and allow its users to store, retrieve, access, and back up any amount of data. All data must be stored within these buckets, making S3 bucket security important to securing an organization’s data. AWS S3 misconfigurations account for 16% of cloud security breaches. To avoid suffering a breach because of an AWS S3 bucket misconfiguration, it is imperative to implement best practices.
AWS S3 Misconfiguration: Risks and Warnings
The risk of breach related to misconfigured AWS S3 buckets is evident in the cases of recent breaches:
- An Amazon S3 bucket owned by a logistics company was left accessible without authorization controls in place. This exposed sensitive data relating to shipments and the company’s clients, including several Fortune 500 companies.
- A misconfigured S3 bucket leaked around 1.5 million files of airline employee PII, including photos of ID cards featuring full names, occupations, and national ID numbers, as well as other miscellaneous photos of employees, planes, luggage, and more.
The common denominator between these breaches is misconfigured AWS S3 buckets. Though AWS made it so that S3 buckets are private by default, exposure due to tampering, adverse actions by developers, and buckets created before private were the default are common.
Departure from known safe states introduces risk to a system. This departure can take many forms, including unintended configuration drift. To prevent degrading its security posture, organizations should take steps to prevent AWS S3 bucket misconfigurations.
How to Prevent AWS S3 Bucket Misconfigurations
The most reliable way to catch IaC misconfigurations that lead to AWS S3 bucket leaks is through vigilant oversight and strong governance. This includes:
- Encrypting all data stored in S3 buckets
- Adhering to the principle of least privilege and issuing minimal bucket access.
- Controlling access with access control lists
- Logging access
This advice is not just good for preventing AWS S3 misconfigurations but is also sound advice for conforming to broader guidelines such as Google SLSA. Several solutions exist, each with a different breadth of functionality.
AWS Config
AWS Config is a service that enables its users to assess, audit, and evaluate the configurations of AWS resources in their accounts. This includes how the resources are related to one another and how they have been configured, depicting how the configurations and relationships changed over time.
When AWS Config evaluates resources, it invokes an AWS Lambda function that returns the evaluated resources’ compliance status. If a resource violates the conditions of a rule, AWS Config flags the resource and the rule as noncompliant.
The supported resources include AWS S3 buckets, though organizations should be aware of AWS Config’s service coverage, particularly in terms of what resources are supported
Cloud Custodian
Cloud Custodian is an open-source, stateless rules engine that manages AWS environments. This tool functions as a compliance governance tool to enforce environmental rules against security and compliance standards. Rather than using a collection of compliance scripts, organizations can use this tool to detect and respond to misconfigurations.
The first step to using Cloud Custodian is writing a YAML file containing the desired policies. Cloud Custodian utilizes policies to specify the required resource types, filters to define the specific resources needed, and actions to take on the filtered set of resources. The template for these policies, named custodian.yml, may be defined as follows:
policies: - name: cycode-example-policy resource: aws.ec2 filters: - "tag:Custodian": ec2-example-filter
This template includes:
- The name of the policy
- The resource types these policies apply to
- The filters list
Cloud Custodian can be run locally or through docker. More details may be found within the Cloud Custodian documentation.
Cycode Platform
We recommend the Cycode platform because of its ability to catch misconfigurations and enforce AWS best practices broadly. Misconfiguration scans are performed with each commit, integrating into the developer workflow and allowing teams to prevent misconfigurations before they happen.
This platform allows manual checks for AWS S3 misconfigurations. There are two main sections where these checks may occur: within Policies and Violations.
Policies
The Cycode platform includes policies that can take the place of the many compliance scripts used by organizations to detect and address S3 bucket misconfigurations. Cycode currently offers over 30 Cloud and IaC policies related to AWS S3 governance and misconfiguration prevention: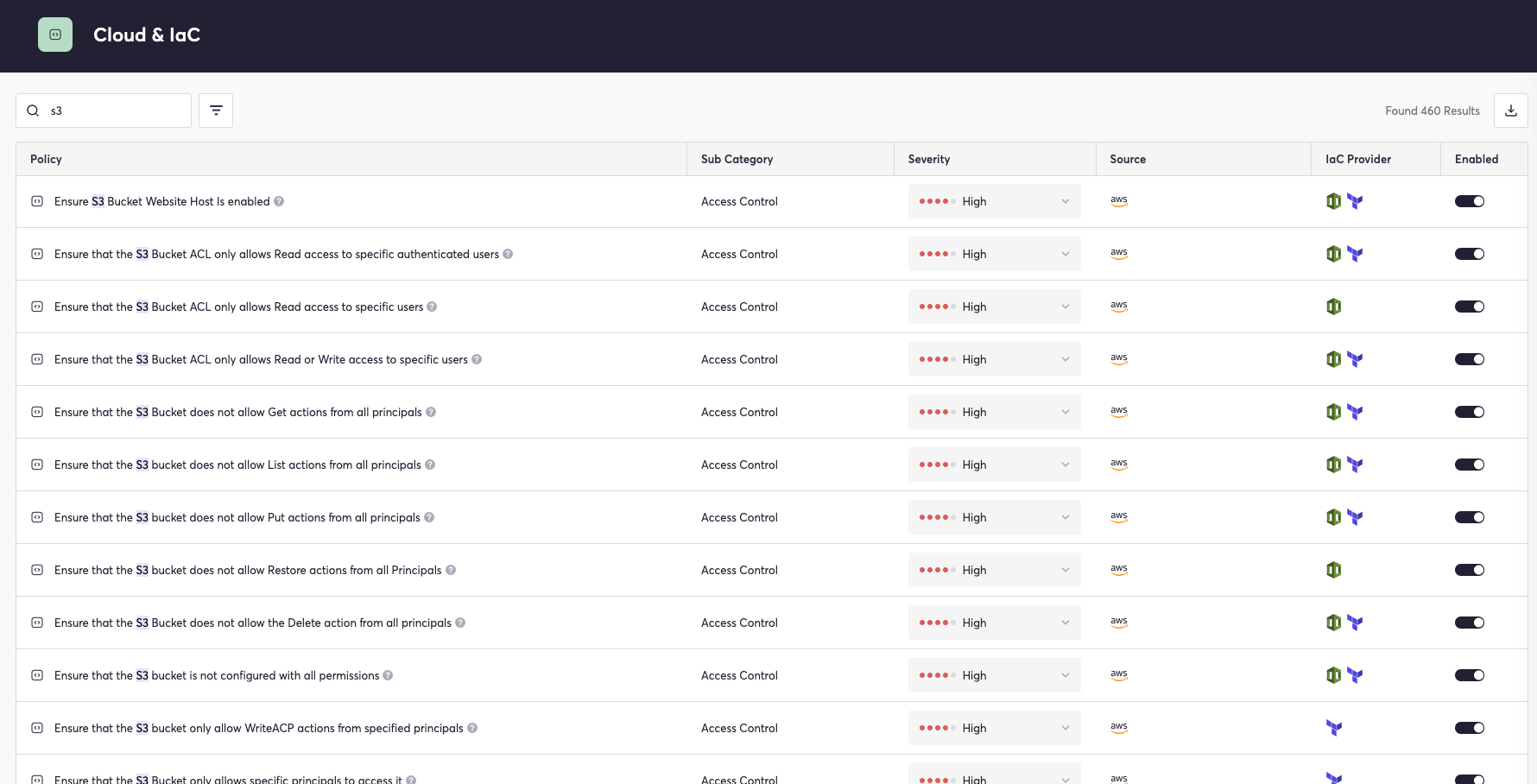
These policies help ensure secure settings for AWS S3 buckets to prevent code leaks, enforce best practices regarding access, and maximize security configurations for IaC providers including Terraform, CloudFormation, and more.
In addition, Cycode includes policies to scan for credentials that could lead to compromised AWS resources, such as AWS secret access keys and AWS account IDs.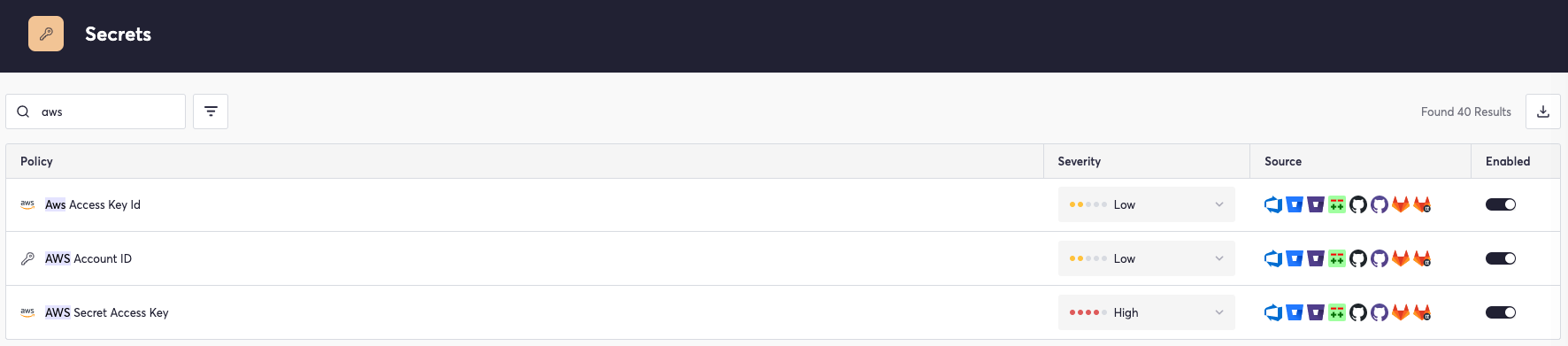
Custom policies may be created for specific scenarios utilizing the power of Cycode’s knowledge graph, meaning that this platform is adaptable and can be customized through a no-code interface. This enables security teams to fit the tool to their specific needs without the overhead of writing policy YAML files.
Violations
Cycode’s Violations section centralizes alerts related to Policies. When filtered by the term S3, this page displays existing policy violations related to AWS S3 misconfigurations:
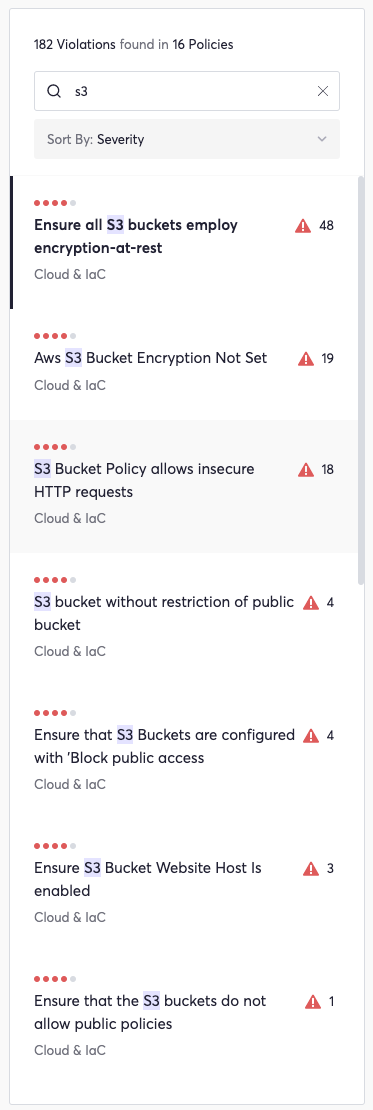
Clicking into a listed violation brings up details including date, location, resource, source, and assignee.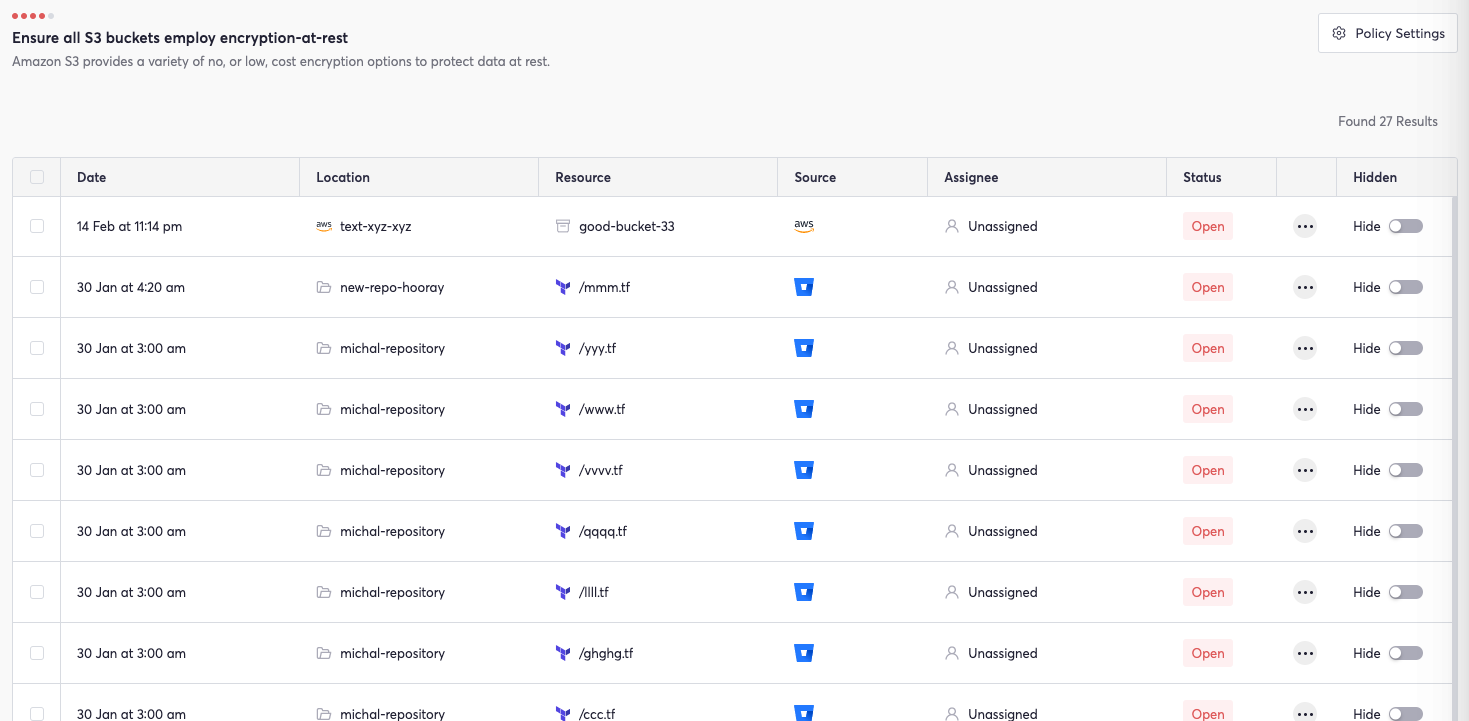
Each entry also includes the status of the misconfiguration, a toggle switch to hide the issue, and more options. This functionality supports creating a Jira or Asana ticket by way of a single click, accelerating remediation, and ensuring seamless tracking of security vulnerabilities.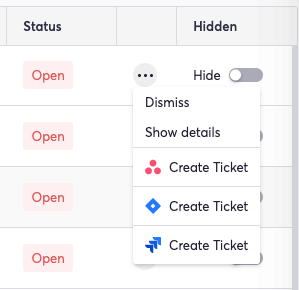
Clicking show details gives deeper violation info, including the affected files and remediation guidelines. The remediation guidelines are outlined in detail in the example violation, which entails a lack of encryption.
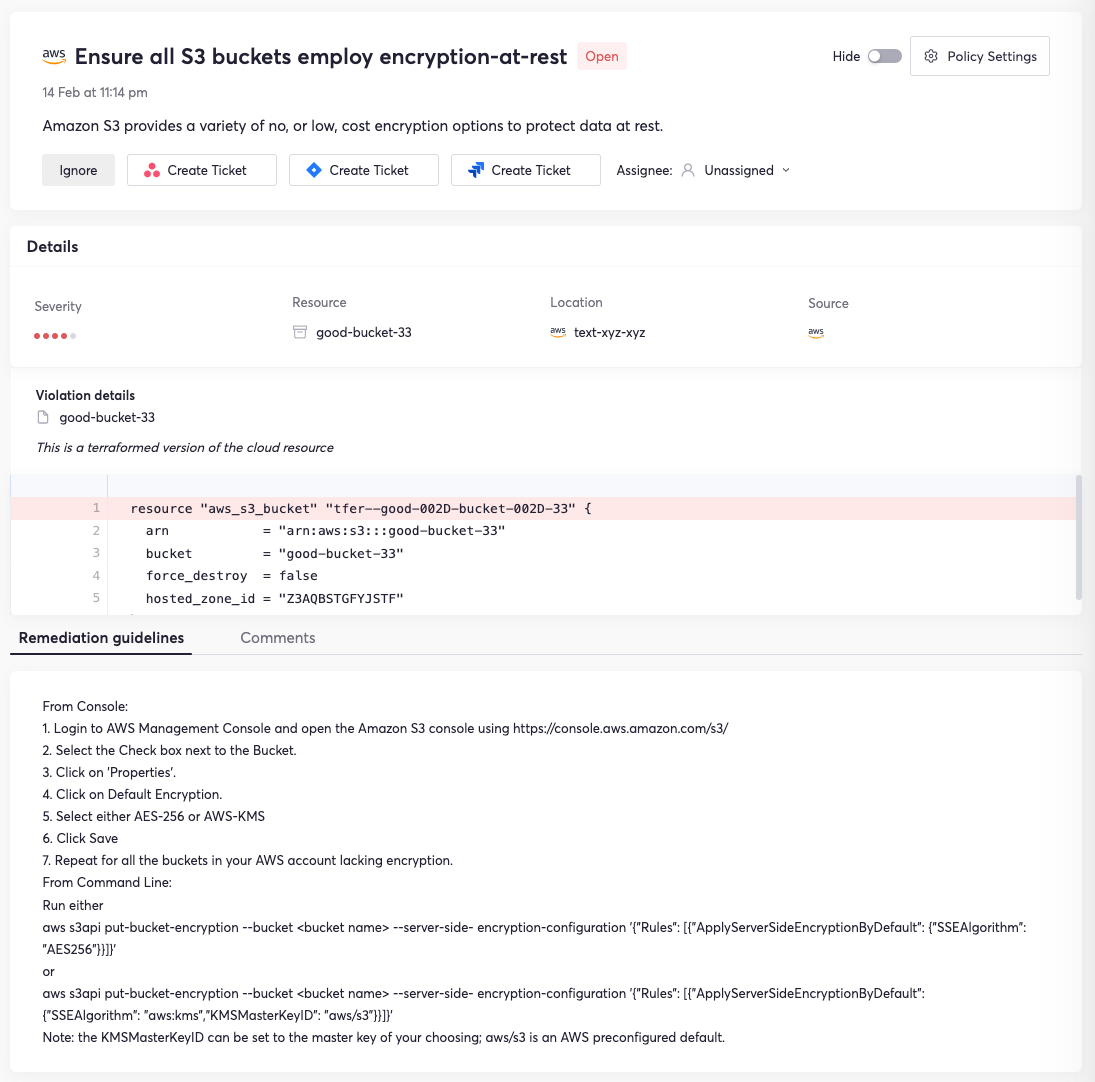 These features combine to create a comprehensive system to protect AWS S3 resources from vulnerabilities and misconfigurations.
These features combine to create a comprehensive system to protect AWS S3 resources from vulnerabilities and misconfigurations.
Beyond just AWS S3 bucket misconfiguration prevention, Cycode provides visibility, security, and integrity across all phases of the SDLC. Cycode hardens your SDLC’s security posture by implementing consistent governance; this reduces the risk of breaches with a series of scanning engines that look for issues like hardcoded secrets, misconfigurations, code leaks, and more.
Want To Learn More?
A great place to start is with a free assessment of the security of your DevOps pipeline.
About Cycode
Adhering to any compliance framework, be it SLSA, the NIST SSDF, or any other framework requires guidance. Cycode is a complete solution to ensuring software supply chain security. The platform provides visibility, safety, and integrity across all phases of the SDLC. Cycode integrates with DevOps tools and infrastructure providers, hardens their security postures by implementing consistent governance, and reduces the risk of breaches with a series of scanning engines that look for issues like hardcoded secrets, infrastructure as code misconfigurations, code leaks, and more. Cycode’s knowledge graph tracks code integrity, user activity, and events across the SDLC to prioritize risk, detect anomalies, and prevent code tampering.
Want to learn more?
Schedule a demo to learn more about how Cycode can help secure your software supply chains.