ASPM That Your Security & Dev Teams Can Depend On.
Real-time risk posture from code to cloud has never been so simple. Finally, you can deliver the visibility, prioritization, and remediation that your security and development teams are waiting for.
{ The Complete ASPM }
The Only AppSec Platform
You'll Ever Need
Cycode ASPM is the only complete AppSec platform that lets you select and connect the scanners that fit your AppSec program.
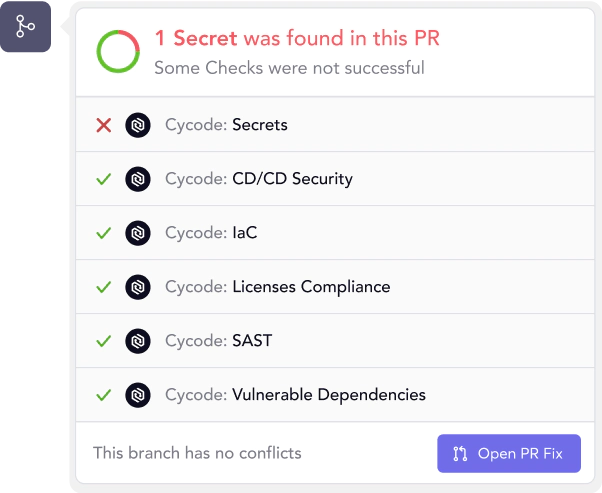
Pipeline Security Secrets, CI/CD, Code Leakage, Build Hardening.
Application Security SAST, SCA, IaC, Containers.
Application Risk Visibility, prioritization, & remediation along with any 3rd party Security tool integrations via ConnectorX.
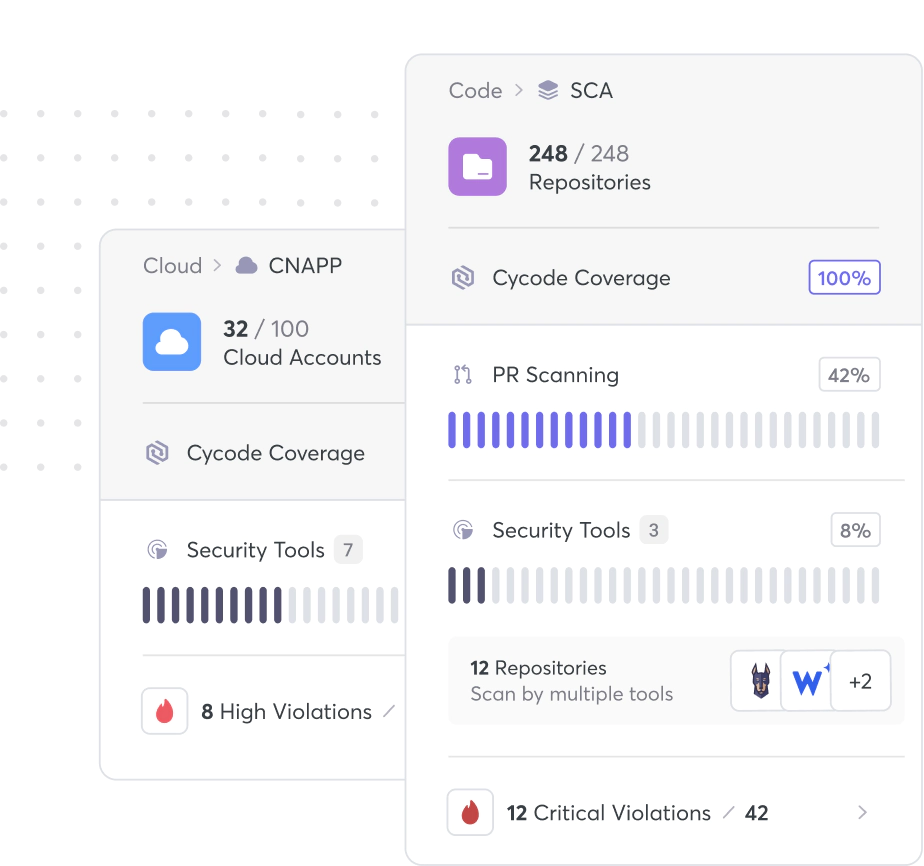
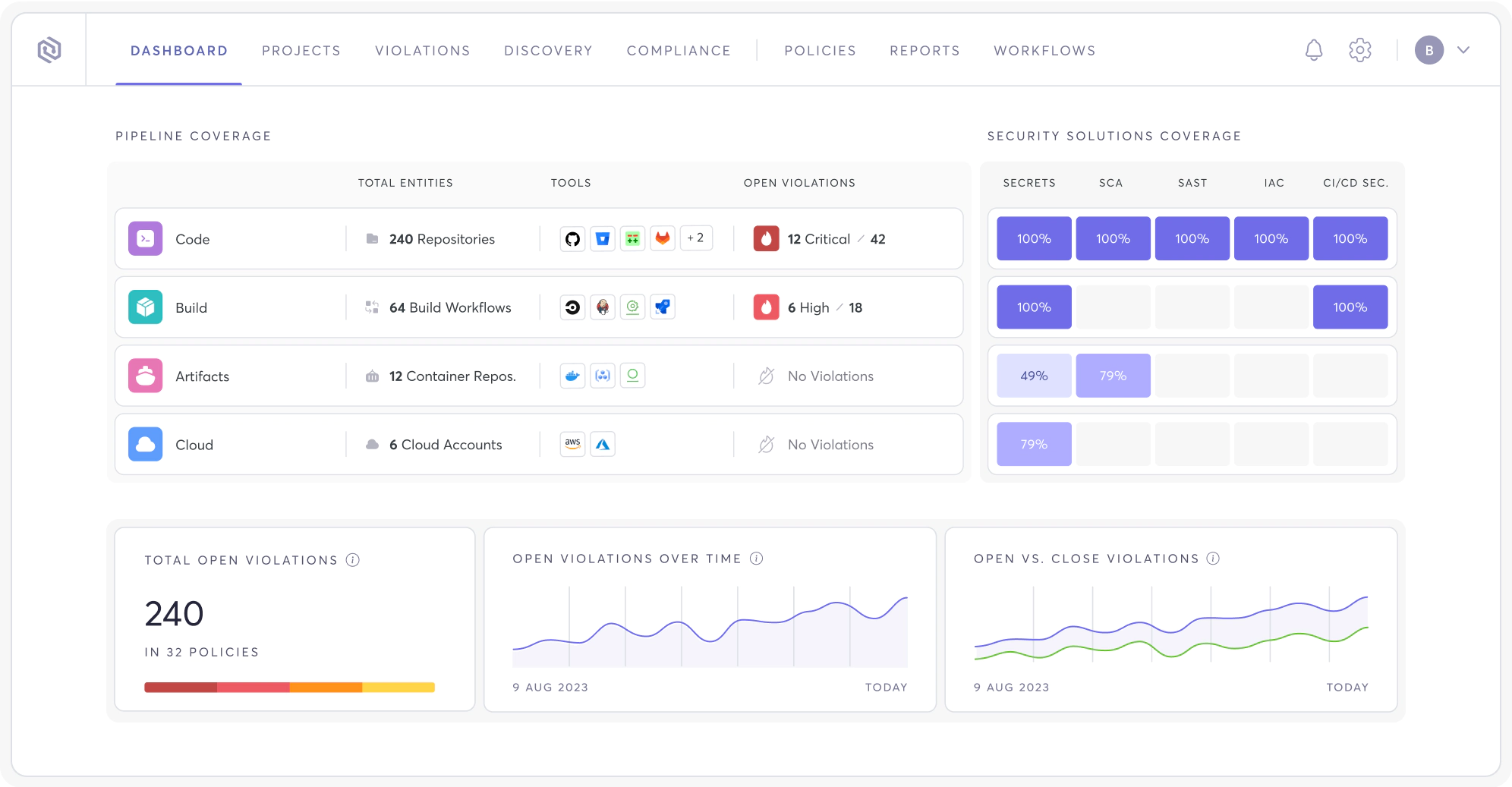
Visibility into Real-Time Risk Posture, Always on Tap
Don’t settle for the status quo. Easily connect into any of your security tools, infrastructure, languages, and more, so Cycode’s visibility and discoverability can do the rest.
Visibility in just 1-Click, and under 5 minutes.
Leverage Cycode native scanners from code to cloud.
Plug into any security tool & bring in all your vulnerabilities through ConnectorX.
Ruthless Prioritization from Code to Cloud
Harness the power to identify and remediate the most critical 1% of vulnerabilities.
Prioritize vulnerabilities based on business risk, exploitability, and severity.
Tie vulnerabilities from code to cloud back to their owners.
Reduce the noise for your developers by up to 90%.
Remediation at the Speed of DevOps
Let your developers fix vulnerabilities through their native environments and workflows.
Correlate and deduplicate critical alerts.
Leverage bulk vulnerability remediation across multiple instances.
Give devs the power they need through dev friendly workflows.
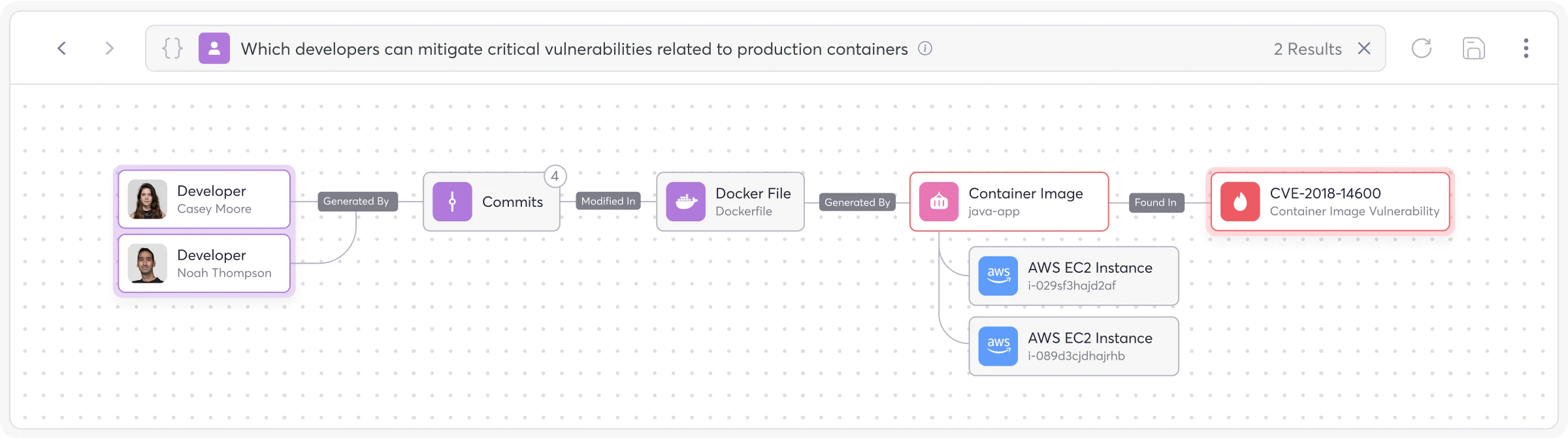
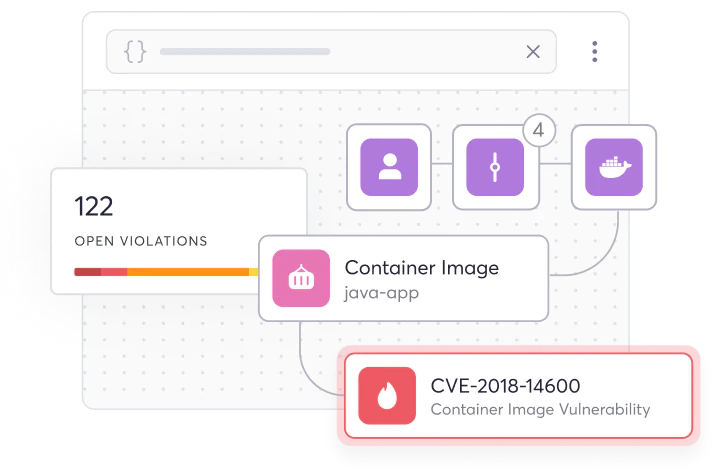
Harness the Power of the
Risk Intelligence Graph (RIG)
Gain vulnerability traceability from code to cloud for total visibility of your SDLC, including application code, tool configurations, cloud infrastructure, ownership, and more.
{ Controlled Shift Left }
Break Down Security-Developer
Silos with Controlled Shift Left
Embed security in the design and coding stages, fixing vulnerabilities earlier in the SDLC.
Promote Collaboration between security and dev teams.
Lower the Cost of Remediation by fixing
defects early in the SDLC.
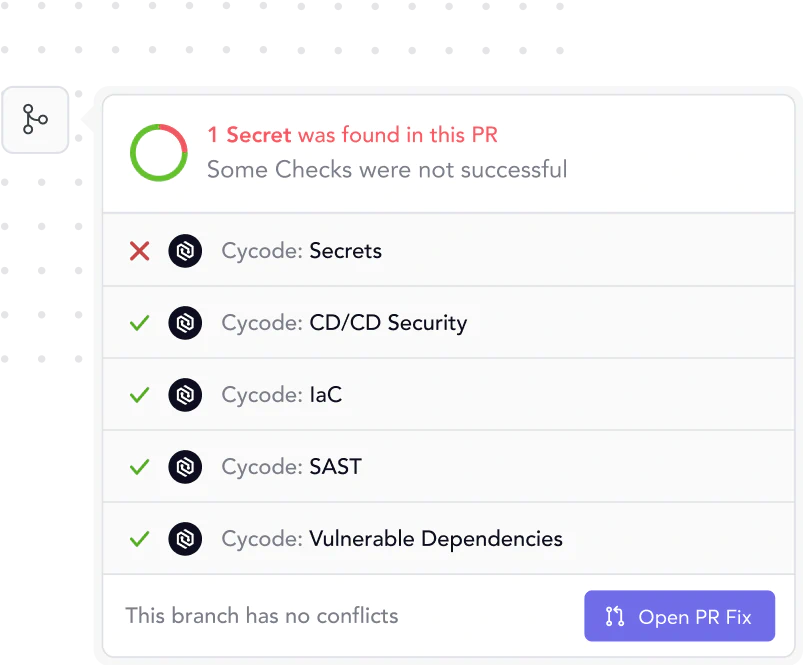
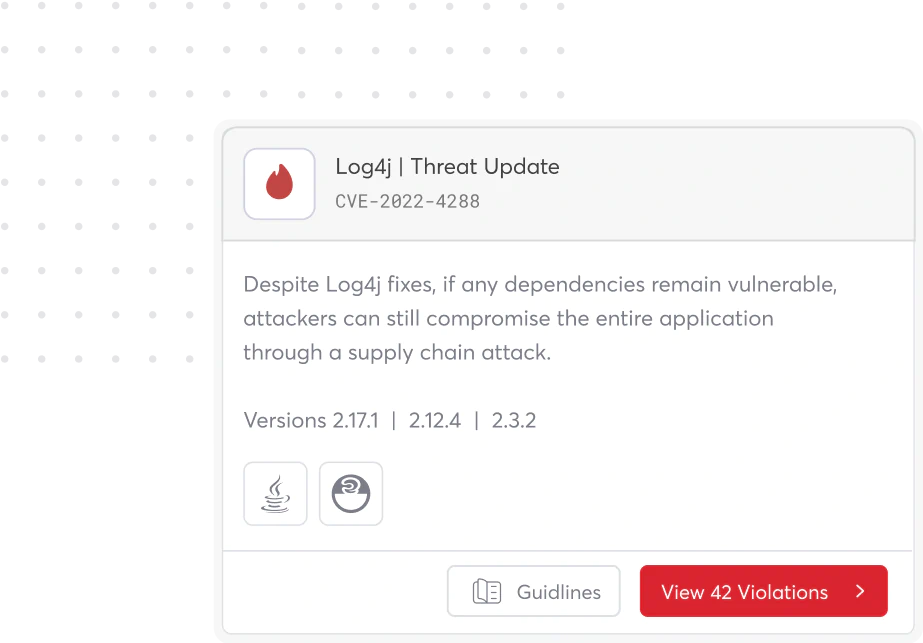
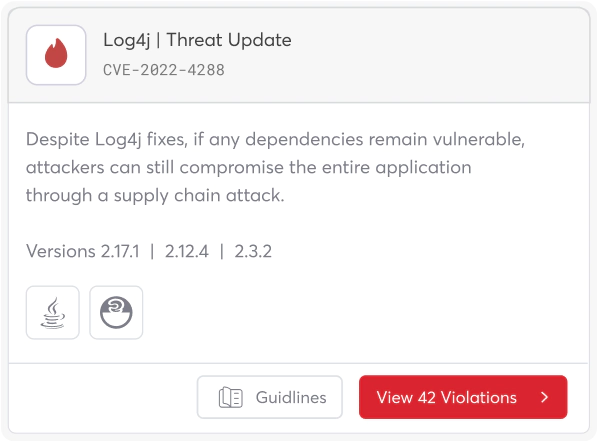
{ Threat Intelligence }
Stop Critical Attacks
Before You’re a Headline
The Cycode Research Team identifies and neutralizes emerging threats before your business is exposed.
Immediate intelligence on zero-day threats.
Detailed readmission advice to fix vulnerabilities
before they can be exploited.