We’ve had a busy month in terms of software supply-chain incidents. In this article, we will discuss prominent recent attacks, explain the attack chain, and elaborate on the results of our findings; compromised, malicious packages are the common element within these incidents. The incidents in question include:
- Malicious
rustdecimalpackage in crates.io - Compromised
ctxpackage in PyPI, and maliciousphpasspackage in packagist - Malicious
pymafkapackage in PyPI
These attacks targetted three different package managers – PyPI, packagist, and crates.io, used three distinct attack vectors, three distinct malicious payloads, and two pen-testing frameworks. However, the result is the same – compromising the machine through the software supply chain.
CrateDepression – rustdecimal package
Attack Type
This attack involves a TypoSquatting attack – creating new packages and mimicking the naming of other popular packages, hoping that users or developers will accidentally download these malicious packages instead of legitimate ones. In addition, this attack allows attackers to insert a well-hidden code into a repository by changing the legitimate dependency with a malicious one.
Discovery
The initial discovery was made on 02/05/22 through an issue in the official rust_decimal package. A few days after the discovery, the Rust Security Response WG removed the malicious crate and issued an advisory explaining the nature of the attack.
Malicious behavior, incentives, and results
The malicious crate (rust eco-system equivalent of package) was named rustdecimal like the popular rust_decimal crate that implements many decimal functionalities.
The crate contained identical source code and functionality as the legitimate rust_decimal crate, except for the Decimal::new function. It checked whether the GITLAB_CI environment variable was set, and if so, it downloaded an additional payload that could compromise the environment completely.
The GITLAB_CI environment variable is defined as part of a Gitlab Runner platform; thus, the attack only targets Gitlab build pipelines. This behavior could indicate two plausible explanations for the attacker’s nature – either a red team that knows its organization or a sophisticated attacker.
We don’t have the precise answer to the “attacker’s” origin. Still, we may rely on Sentinel One researchers’ paper which further establishes the suspicions that the attack may be a sophisticated group that used its abilities to alter the target repository and insert subtle code. According to that report, the resulting binary from that attack is a Mythic post-exploitation framework that takes control of the environment.
The security team of crates.io reported that rust developers downloaded the malicious crate 500 times. We don’t have a precise answer whether this was enough for the attacker or if the quick response denied a possible attack.
Indications of compromise through the Cycode platform
Package name: rustdecimal
Versions: any version
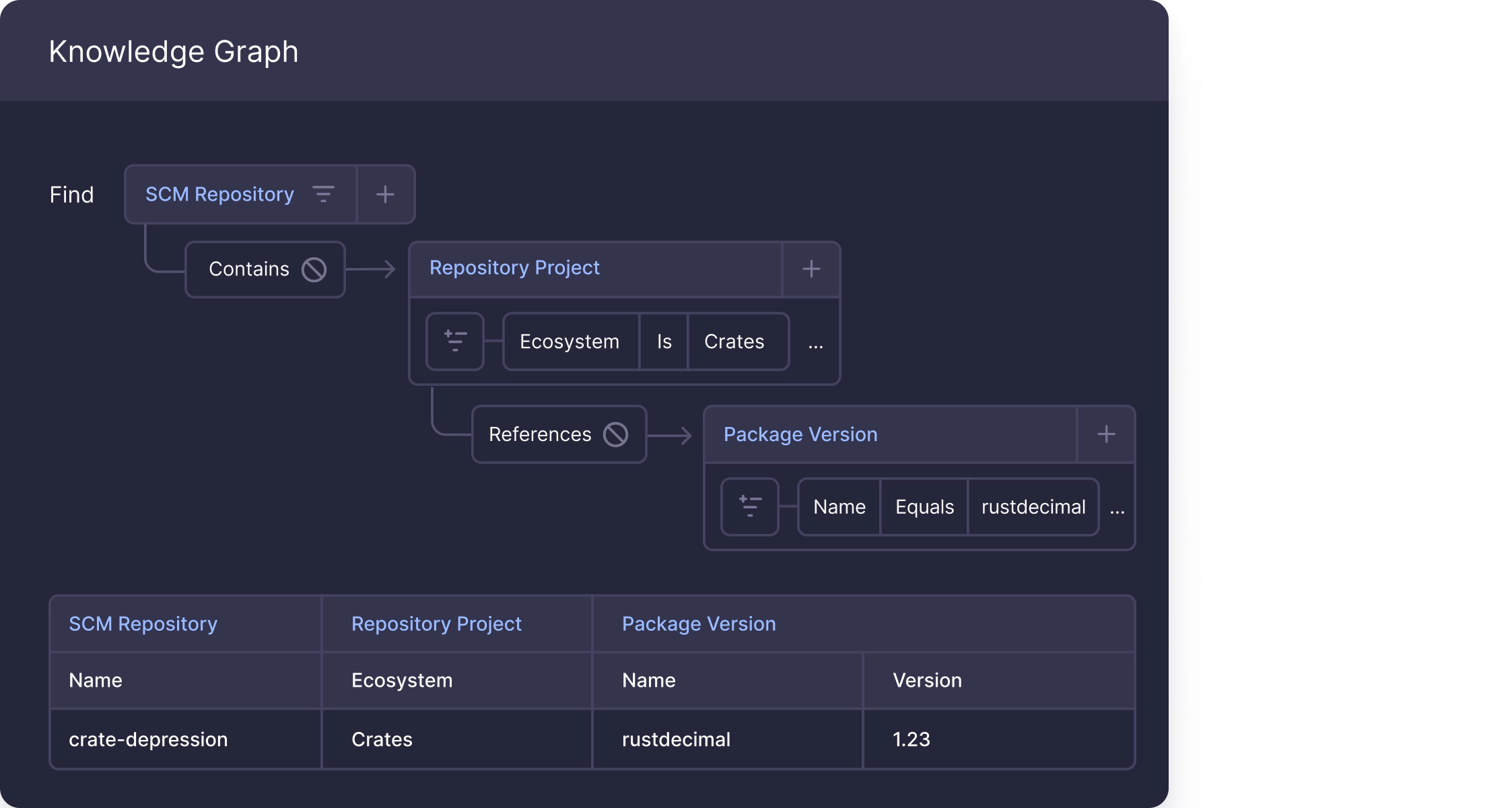
We recently released a security advisory explaining this threat and have since added a threat alert to our platform’s Threat Advisory dashboard.
ctx and phpass packages
Attack Type
This attack involved a RepoJacking (or ChainJacking) attack – whenever a git repository user requests to change its name, the previous name becomes available to catch. Several frameworks, such as Go, PHP, and Swift, allow the installation of packages directly through the repository alias. Thus, such frameworks could install malicious packages containing the previous name.
This attack also involved a Domain Takeover attack – repository and package registries may be tied to email addresses on custom domains. For old packages, these domains may be no longer valid. A malicious actor could register that domain, request a password reset procedure, and take over that account when this happens.
Discovery
The first lead was a Reddit thread posted on 24/05/22 claiming that the ctx package on Python had been hacked. The ctx is a simple package that allows you to access dictionary items using dot notation.
Malicious Behavior, incentives, and results
Quickly after the report on Reddit, the ethical hacker s0md3v published the flow of that attack on Twitter, including an additional package that was compromised – phpass.
The inserted code was quite simple – it collects all your environment variables and sends them to a hard-coded server URL. The attacker’s idea was to harvest sensitive information, such as AWS credentials, which could’ve been saved as environment variables.
The next day, Yunus Aydin, who goes by “SockPuppet,” approached s0md3v, claiming he is a security researcher, and attacked the packages to demonstrate the possible impact of a bug bounty submitted to Github. He also said that Github flagged his report as a “duplicate”.
That “security researcher” also posted a blog describing his methods for that attack. By studying it, we learned that while the malicious code for ctx and phpass was similar, the takeover method was different. For the ctx package, he noticed that owner’s email for that package had an unregistered domain, so a domain takeover attack was possible. For the phpass package, he noticed that the original username for that package, hautelook/phpass was available, so a RepoJacking attack was possible.
About the RepoJacking technique – A few years ago, Github created a mechanism for popular repository namespace retirement to mitigate this threat. Yunus found that this could be bypassed. While it is prohibited to create the desired repository name after changing your username to the popular one, you could change your username to a random one, create the desired repository name, and then change the username to the one selected.
Both packages had over 3 million downloads over their lifetimes. Even though Yunus claims to be a security researcher, we should highly doubt that due to the invasive nature of the added code that exfiltrates sensitive information such as AWS credentials and the motivation to push the malicious packages through this Reddit thread.
Eventually, all the malicious packages were removed.
Threat Remediation through the Cycode platform
Package name: ctx
Versions: 0.1.2/0.2.*
We highly recommend identifying what projects use the ctx package and to understand whether it had new installs between 2022-05-14 to 2022-05-24. More information can be found at this official PyPI security advisory.
Package name: phpass
Versions: Latest
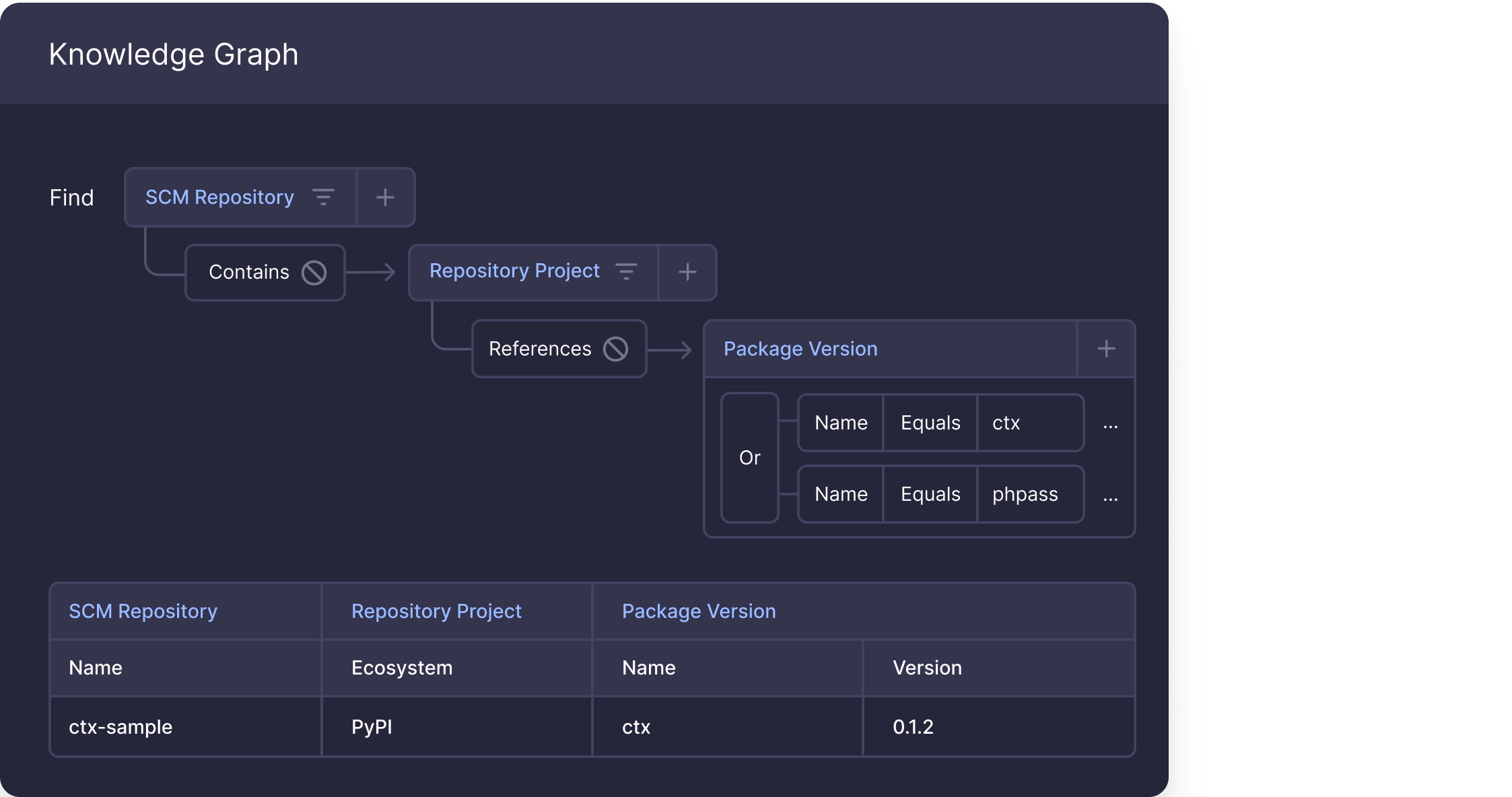
Similar to ctx, we suggest identifying if any installs to the package were made during that time.
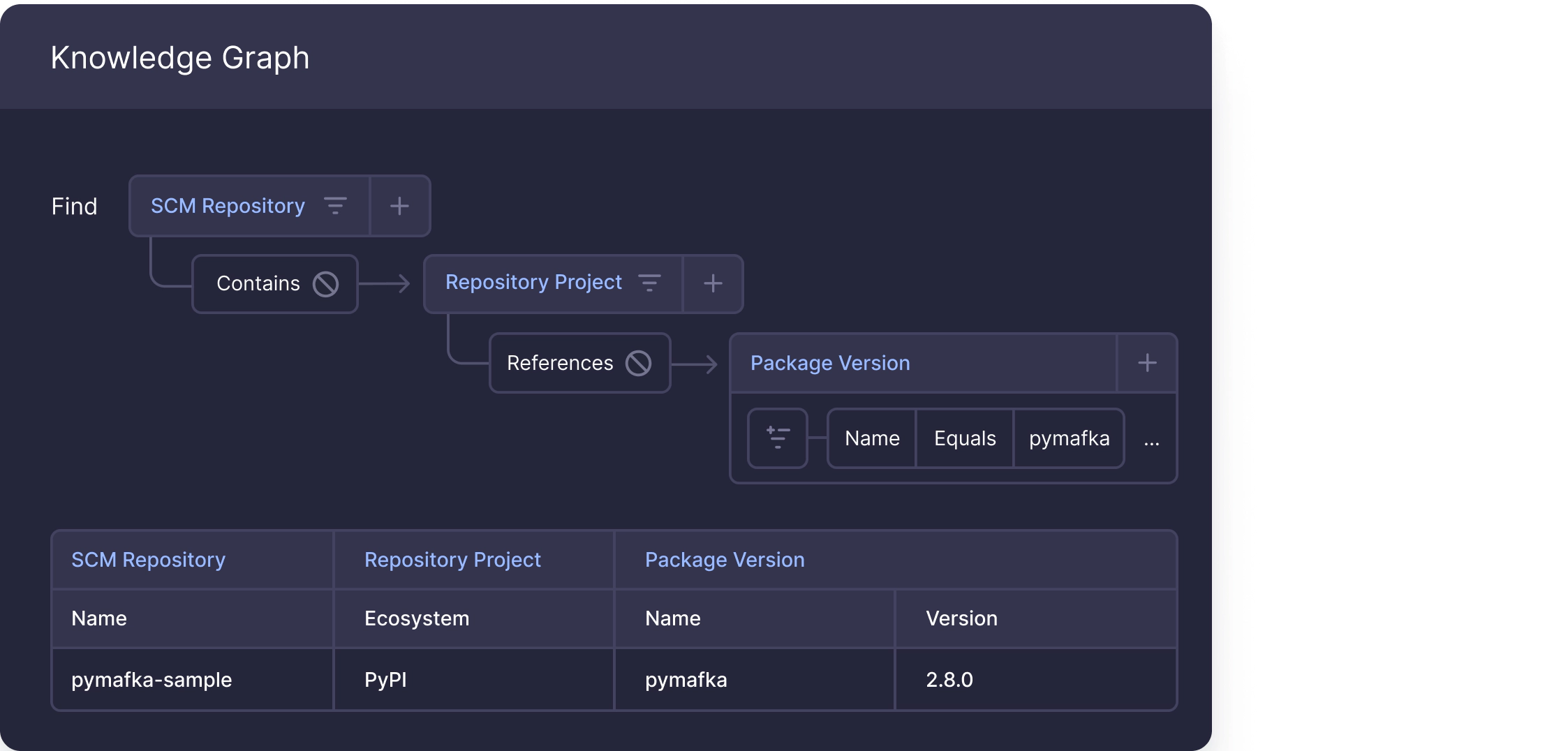
PyMafka
Attack Type
This attack involves a TypoSquatting attack – we explained the nature of the attack previously.
Discovery
Sonatype research team discovered and published on 20/05/22 about a malicious python package named pymafka in the PyPI registry. That package name is similar to the legitimate and popular package PyKafka.
Malicious Behavior, incentives, and results
Using the setup.py install script, this package downloads and installs an additional payload depending on the operating system. This payload is a Cobalt Strike beacon, a popular pen-testing tool used by real-world attacks, including the SolarWinds hack. This tool contains a handful of abilities to help the adversary perform his moves silently and efficiently.
The source of this attack isn’t clear yet, but the two most prominent options are either a motivational red-team or a sophisticated attacker. It includes several advanced techniques like using different Cobalt Strike executables for several operating systems and various packing and obfuscation methods.
The package was removed from the PyPI registry. It has been downloaded 300 times.
Threat Remediation through the Cycode platform
Package name: pymafka
Versions: any version
Conclusion
This recent burst of software supply-chain attacks further enhances the need for organizations to have proper tooling to identify and mitigate such attacks. In addition, the variety of attack vectors and methods of compromise demonstrates the need for a robust system that can help address these emerging threats in a rapid fashion. This is exactly what we’ve built with the knowledge graph in Cycode. The platform provides the complete tooling for both mitigating and identifying:
- Cycode platform helps audit privileges and excessive access to repositories and package registries. It helps organizations adhere to the principles of least privilege without requiring additional work from the DevOps team and deny the above attacks.
- Powered by its knowledge graph, Cycode’s advanced detection capabilities correlate event data and user activity across the SDLC to create contextual insights and automate remediation. It includes the recent attacks.
Want To Learn More?
A great place to start is with a free assessment of the security of your DevOps pipeline.