Modern software development relies on a complex network of components, tools, and people, known as the software supply chain. If not properly protected, this intricate web can introduce exploitable security vulnerabilities that lead to breaches and the distribution of compromised software.
In this article, we’ll explore the concept of software supply chain security, its importance, and best practices for keeping your software development process safe.
Key highlights:
- Software supply chain security protects the entire development lifecycle—code, dependencies, build systems, and delivery pipelines—against tampering and compromise.
- Application security and supply chain security are distinct but interrelated, working together to safeguard software from development through deployment.
- Effective protection requires layered tools and practices, including SAST, SCA, IaC scanning, CI/CD security, and ASPM to unify visibility and control.
Cycode’s AI-powered AppSec platform helps enterprises streamline the process of maintaining software supply chain best practices.
What Is a Software Supply Chain?
A software supply chain is all the code, components, libraries, dependencies, tools, processes, and people involved in developing, building, and publishing a software artifact.
Importantly, software is no longer based on code written entirely in-house. It consists of an intricate network of people, components, and tools. This includes:
- Developers and DevOps
- Third-party vendors, components, and tools
- Open source projects
For something like a car, a supply chain includes things such as:
- Major in-house produced components like engines and transmissions
- Third-party components like door handles, brake lights, and wiper blades
- The manufacturing facilities, machinery, and tooling used to assemble the car
- The workers working in the production facility
What Is an Example of a Software Supply Chain Attack?
The most well-known software supply chain attack is the 2020 SolarWinds breach. Discovered in December of that year, it stands out due to its unprecedented scale, sophistication, and the high-profile nature of its victims.
Here’s what happened:
Attackers infiltrated SolarWinds’ build system and injected a backdoor named Sunburst into the Orion software updates released between March and June 2020. When customers, including government agencies and numerous Fortune 500 companies (including Microsoft and Cisco), installed these updates, they unknowingly introduced the vulnerability into their environment, granting potential access to their networks.
The sophisticated nature of the attack lay in its ability to remain undetected for months, as the malicious code was carefully designed to blend in with legitimate traffic and to evade traditional security defenses. Once the backdoor was installed, the attackers could execute commands, transfer files, and move laterally within affected networks, conducting reconnaissance and potentially exfiltrating sensitive data.
The SolarWinds attack emphasized the critical need for improved security measures and vigilance in the modern software supply chain lifecycle and brought to light the importance of implementing rigorous code audits, enhancing build environment security, and adopting advanced monitoring techniques to detect anomalous behaviors.
It also spurred a reevaluation of third-party risk management practices, pushing organizations to scrutinize their software dependencies more closely and to adopt zero-trust principles to mitigate the potential impact of similar supply chain attacks in the future.
Explore more key AppSec takeaways from the SolarWinds attack.
What Is Software Supply Chain Security?
Software supply chain security involves safeguarding the entire software development and deployment process against potential threats and vulnerabilities.
Too often, organizations think only about securing third-party or open-source dependencies in their code. This approach is too narrow in scope. To truly secure the software supply chain, teams must implement a multi-faceted approach that mitigates risks from code to cloud, including all the DevOps tools and infrastructure that make up the SDLC.
How Software Supply Chain Lifecycle Security Compares to AppSec
Software supply chain lifecycle security ensures the integrity, security, and trustworthiness of the entire software development lifecycle (SDLC), from the initial coding phase to deployment and beyond. It addresses risks related to third-party components, build environments, code repositories, and software distribution channels.
The emphasis is on preventing and detecting tampering, unauthorized access, and vulnerabilities in the components and processes used to create and deliver software. This includes:
- Securing build systems
- Vetting third-party dependencies
- Protecting code signing mechanisms
Application security, on the other hand, is concerned with securing the software itself once it’s deployed and in use. It involves identifying, mitigating, and preventing vulnerabilities within the application’s codebase and runtime environment.
Key application security practices include:
- Code reviews
- Application security testing
- Security patches
- Runtime protection measures
While it focuses on the final product, it also encompasses secure coding practices to prevent vulnerabilities from being introduced during development.
The overlap between the two areas lies in the shared goal of ensuring software security. Both domains aim to protect against threats and vulnerabilities, albeit at different stages and with different focuses. For example, secure coding practices are part of both a software supply chain security framework and application security. In the case of the former, the goal is to prevent vulnerabilities early, while for the latter, it’s to ensure the code itself is robust and secure.
The table below highlights some of the key differences between supply chain and application security, illustrating how they complement each other while addressing distinct parts of the software lifecycle.
| Software Supply Chain Security | Application Security | |
| Focus | Integrity and security of the entire development lifecycle | Security of the deployed application |
| Key Concerns | Third-party dependencies, build systems, and code repositories | Vulnerabilities in application code and the runtime environment |
| Activities | Securing build environments, code signing, and dependency management | Code reviews, application security testing, and patch management |
| Stage of Application | Development and delivery processes | Post-deployment and runtime |
| Primary Goal | Preventing tampering and unauthorized access | Mitigating and preventing vulnerabilities in the application |
What Are Software Supply Chain Vulnerabilities?
A software supply chain vulnerability refers to weaknesses or flaws within the processes, tools, or dependencies used in developing, integrating, and delivering software.
The interconnected nature of the supply chain makes it susceptible to a wide range of vulnerabilities that can be exploited by malicious actors and lead to a breach, which could, in turn, lead to the distribution of compromised software to downstream customers. The result? Further security incidents, data loss, and other serious consequences for both end-users and organizations.
Importantly, vulnerabilities can arise at every stage of the SDLC, and the reliance on external vendors and contractors for software development increases the potential for an attack. That means the software supply chain is more vulnerable than you might think.
Common software industry supply chain risks include:
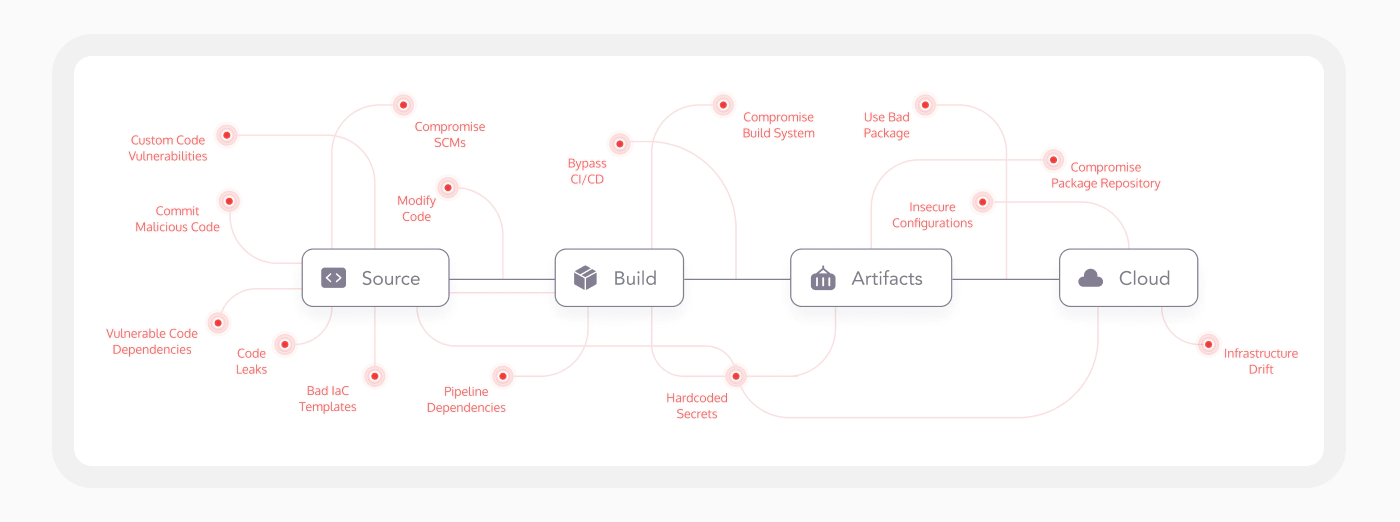
| Types of Software Industry Supply Chain Risks | How the Risks Impact Enterprises |
| Insecure Proprietary Code | Proprietary code that lacks adequate security measures can contain vulnerabilities that attackers exploit to gain unauthorized access or cause disruptions. |
| Compromised Source Control Systems | When source control systems are breached, attackers can modify, steal, or insert malicious code into the software being developed. |
| Code Tampering | Unauthorized changes to the codebase, such as the injection of malicious code, can introduce backdoors or other security threats into the software. |
| Compromised Build Systems | Attackers who infiltrate build systems can alter the software at the compilation stage, embedding malicious elements that are distributed through legitimate software updates. |
| Commercial Software or Open-Source Code Vulnerabilities | Dependencies on third-party or open-source software can introduce vulnerabilities if these components are not properly vetted and updated. |
| Undermined Code Signing | If the code signing process is compromised, attackers can distribute malicious software that appears to be legitimate and trusted. |
| IaC Misconfigurations | Infrastructure as Code (IaC) configuration errors can lead to insecure deployment environments, exposing applications to potential exploits. |
| Vulnerabilities or Misconfigurations in Running Software | Once deployed, software with vulnerabilities or misconfigurations can be exploited by attackers to gain access or disrupt services. |
Why Are Cyber Supply Chain Attacks Trending?
The Verizon 2025 Data Breach Investigations Report (DBIR) highlights a significant increase in cyber supply chain attacks, with third-party involvement in breaches doubling year-over-year to account for 30% of all breaches. Likewise, the European Union Cybersecurity Agency (ENISA) has reported a 4× increase in the number of organized software supply chain attacks since early 2020. Together, these trends underscore the growing importance of securing every stage of the software lifecycle—from development and build systems to deployment pipelines and third-party components.
Since easy access is what they’re after, developers have become high-value targets. They often have over-provisioned access to their organization’s environment, and hold the keys (er, credentials) to important systems and resources.
Once compromised, developer accounts can be leveraged to insert malicious code into applications, leak source code, steal data, install backdoors, and facilitate lateral movement within the environment. Even basic security issues, like the absence of multi-factor authentication, further exacerbate the risk.
Remember: it only takes one successful exploit of one of these vectors to give bad actors access to other tools as well as the production runtime environment and all its data.
Types of Software Supply Chain Attacks
While the SolarWinds breach is the most famous example, modern software supply chain attacks come in many forms. Attackers constantly look for the path of least resistance, often targeting the “plumbing” of your development environment rather than the hardened production application. By understanding these common attack vectors, security teams can better identify software supply chain vulnerabilities before they are exploited.
Below are the primary methods threat actors use to compromise the integrity of the software industry’s supply chain.
1. Dependency Confusion Attacks
Dependency confusion occurs when an attacker uploads a malicious package to a public repository (like npm or PyPI) using the same name as an internal, private package used by a company. Because many package managers default to pulling the latest version from public registries, the build system unknowingly downloads the attacker’s “update” instead of the secure internal version.
This method is particularly dangerous because it bypasses traditional perimeter defenses by piggybacking on legitimate automated processes. Once the malicious package is integrated, it can execute code during the build or at runtime.
- Consequences:
- Execution of arbitrary code on developer machines or build servers.
- Exfiltration of environment variables and sensitive API keys.
- Unintentional distribution of malware to end-users via “poisoned” updates.
2. Typosquatting and Malicious Package Injections
In a typosquatting attack, hackers publish packages with names very similar to popular open source libraries, such as “requestz” instead of “requests.” They rely on developers making a simple keyboard error during installation. Once installed, these libraries function just enough to avoid immediate detection while running malicious background scripts.
Beyond typos, attackers also gain maintainer access to legitimate, widely-used packages through social engineering or credential theft. They then inject malicious code into a trusted update, instantly compromising thousands of downstream organizations that rely on that dependency.
- Consequences:
- Backdoors planted deep within proprietary software.
- Credential harvesting from users of the compromised software.
- Long-term persistence within a victim’s infrastructure.
3. Compromised Build Systems and CI/CD Pipelines
The CI/CD pipeline is the heartbeat of modern DevOps, making it a prime target for securing the software supply chain. If an attacker gains access to your build server (like Jenkins or GitHub Actions), they can modify the source code after it has been reviewed but before it is compiled. This allows them to insert malicious logic that never appears in the original git repository.
Because these changes happen “under the hood” during automation, they are incredibly difficult to spot with standard manual code reviews. A compromised pipeline turns your own trusted delivery mechanism into a weaponized distribution channel.
- Consequences:
- Injection of malicious binaries into production-ready artifacts.
- Loss of integrity in the automated testing and deployment process.
- Potential for large-scale breaches similar to the SolarWinds event.
4. Source Code Repository and Developer Account Takeovers
Developers often have broad access to an organization’s most sensitive assets. If a developer’s account is compromised through phishing or leaked session tokens, an attacker can push malicious commits directly into the master branch. They can also disable security controls like branch protection rules or mandatory peer reviews.
Securing these entry points is a core part of software supply chain management. Without strict identity controls, the source code repository becomes a playground for attackers to study your logic, find vulnerabilities, and plant time bombs in the code.
- Consequences:
- Theft of proprietary intellectual property and “crown jewel” source code.
- Unauthorized changes to critical application logic.
- Lateral movement from development environments into production clouds.
5. Code Signing Certificate Compromise
Code signing acts as a digital “seal of authenticity” for software. If an attacker steals a company’s private signing keys, they can sign their own malware and make it appear as if it was officially produced and verified by your organization. This bypasses operating system warnings that usually block untrusted software.
This is a devastating blow to brand trust. When a signed update carries a virus, the user’s computer trusts it implicitly because the signature matches the legitimate software supply chain security vendors they expect to hear from.
- Consequences:
- Malware appearing as legitimate, “trusted” software updates.
- Total loss of customer trust and brand reputation.
- Difficulty in revoking certificates without breaking existing deployments.
6. Malicious or Vulnerable Third-Party Components
Modern apps are built like LEGO sets, using dozens of third-party libraries. If any of these components have known vulnerabilities—or were intentionally created with malicious intent—they create a weak link in your security chain. Attackers scan public databases for these “low-hanging fruit” vulnerabilities to gain an easy foothold.
Effective software supply chain security tools must constantly monitor these components. Using an outdated or unvetted library is essentially inviting an attacker to exploit a known flaw that your team didn’t even write.
- Consequences:
- Exposure to “N-day” vulnerabilities that are publicly documented.
- Increased attack surface through bloated or unnecessary dependencies.
- Compliance failures regarding data protection and software integrity.
7. Tampered Infrastructure as Code and Configuration Files
As companies move toward “Code-to-Cloud” models, infrastructure is now defined in files like Terraform or Kubernetes manifests. If an attacker tampers with these files, they can silently open firewall ports, disable encryption, or grant themselves administrative permissions in the cloud environment.
Securing these configurations is just as vital as securing the application code itself. A single misconfigured line in an IaC template can expose an entire database to the public internet, regardless of how secure the actual software code is.
- Consequences:
- Insecure cloud environments with “open doors” for attackers.
- Data breaches caused by misconfigured storage buckets or databases.
- Difficulty in detecting configuration drift from established security baselines.
Key Components of Supply Chain Management in Software Industry Processes
When it comes to answering the important question, “How can I effectively secure my software supply chain?” there are a lot of components to manage, with the average team using 49+ tools, including supply chain security software like Static Application Security Testing (SAST) and Software Composition Analysis (SCA).
It’s no wonder our 2025 State of ASPM report shows 61% of security teams have already started consolidating their tool stacks, and 88% say they would consolidate further in the next 12 months if given the chance.
Key components include:
Visibility and Governance
Gaining visibility and enforcing consistent supply chain governance and security policies — such as least privilege, hardening authentication, and implementing branch protection rules — across all your teams, DevOps tools, and infrastructure.
Secure Coding and Review Practices
Enforcing secure coding standards and conducting thorough code reviews during the development phase minimizes vulnerabilities and reduces the risk of introducing exploitable weaknesses.
Code Tampering Prevention
Establishing safeguards in pipelines and the development process to ensure only authorized code and components are used in your applications.
CI/CD Security
Implementing secure CI/CD practices to automate code integration, testing, and deployment. This includes using secure CI/CD tools, validating code changes, and ensuring that only verified and secure code is deployed.
IaC Security
Scanning IaC templates to ensure they are free from misconfiguration issues before they are deployed, and mistakes are amplified across numerous cloud environments.
Identity and Access Management
Implementing strong identity and access management controls to ensure that only authorized individuals have access to critical systems and code repositories. This includes using multi-factor authentication and least privilege principles.
Hardcoded Secrets Detection
Detecting and remediating any existing hardcoded secrets across many locations and using developer workflow integrations to prevent new hardcoded secrets from being introduced.
Source Code Leakage
Identifying suspicious behavior to prevent leaks and detecting proprietary code exposure so that any leaks are quickly contained.
Dependency Management
Assessing and managing third-party dependencies mitigates the risk of using vulnerable or compromised libraries. Likewise, regularly updating dependencies and monitoring for security advisories are crucial.
Container Security
Securing containerization processes and implementing best practices for creating, deploying, and maintaining containers securely. This involves regular security scans and addressing vulnerabilities in containerized environments.
Monitoring and Logging
Implementing comprehensive monitoring and logging practices to detect and respond to security incidents promptly. This includes monitoring for unusual activities, analyzing logs, and setting up alerts for potential security threats.
Why Software Supply Chain Management Is Important
The repercussions of a software supply chain breach are far-reaching. Exploiting just one weakness opens the door for threat actors to steal sensitive data, disrupt businesses, and take control of systems. Worse still, software supply chain weaknesses allow threat actors to spread attacks to downstream customers.
When this happens, the consequences can be significant and long-term.
Unfortunately, agile development practices and the demand for rapid deployment can sometimes be at odds with releasing secure code. So how can organizations maintain agility while improving the security of their software supply chains?
Building a Program for Securing the Software Supply Chain: Key Steps
Building a robust strategy for securing the software supply chain requires moving beyond reactive scanning. It demands a holistic program that integrates security into the very fabric of the development lifecycle. For many enterprises, the challenge isn’t just finding a tool, but creating a repeatable process that balances speed with safety.
By following these key steps, your organization can move toward a mature software supply chain management posture that protects both your proprietary IP and your downstream customers.
1. Map Your Software Supply Chain and Identify Exposure Points
Before you can secure your environment, you must understand its full scope. Mapping involves documenting every asset, from the code repositories and CI/CD pipelines to the third-party libraries and developer identities that interact with your systems. In the modern era, this also means accounting for software supply chain and LLM risks, as AI-generated code and large language models introduce new vectors for prompt injection and insecure output.
This mapping process identifies where your “crown jewels” reside and where they are most vulnerable to compromise. By visualizing the flow of code from a developer’s workstation to the production cloud, you can pinpoint high-risk “choke points” where a single failure could lead to a massive breach.
- Key Actions:
- Create a comprehensive inventory of all DevOps tools and service accounts.
- Audit all third-party and open-source dependencies currently in use.
- Identify “shadow IT” tools or unmanaged repositories that fall outside official security oversight.
2. Select and Align With a Supply Chain Security Framework
Standardization is the bedrock of a successful security program. Adopting an established software supply chain security framework—such as SLSA (Supply-chain Levels for Software Artifacts) or NIST’s Secure Software Development Framework (SSDF)—provides a roadmap for maturity. These frameworks help you move away from guesswork and toward a structured approach based on industry-proven best practices.
Alignment with a framework also simplifies communication with stakeholders and auditors. It allows you to set clear benchmarks for “what good looks like,” ensuring that every team is working toward the same level of artifact integrity and build security.
- Key Actions:
- Choose a framework that fits your industry (e.g., SLSA for build integrity or NIST for federal compliance).
- Perform a gap analysis to see where your current processes fall short of framework requirements.
- Use framework tiers to set incremental goals for security maturity.
3. Define Governance, Ownership, and Security Requirements
A common pitfall in software supply chain security is the “responsibility gap,” where security and development teams each assume the other is handling a specific risk. To solve this, you must clearly define who owns which part of the supply chain. Governance policies should dictate strict requirements for code reviews, authentication standards like MFA, and the vetting process for new third-party vendors.
Once ownership is established, these requirements must be documented as non-negotiable standards. Whether it is a mandate for signed commits or a policy against hardcoded secrets, clear governance ensures that security is a prerequisite for delivery, not an optional afterthought.
- Key Actions:
- Establish a “Security Champions” program to bridge the gap between Sec and Dev teams.
- Document clear policies for secrets management and access control.
- Define the criteria for “breaking the build” when critical vulnerabilities are detected.
4. Standardize and Automate Security Controls
Manual checks cannot keep up with the pace of modern DevOps. To achieve a secure software supply chain, you must automate your security controls. This includes integrating SAST, SCA, and IaC scanning directly into the CI/CD pipeline. Automation ensures that every piece of code is checked for vulnerabilities, misconfigurations, and leaked secrets before it ever reaches a production environment.
Standardization ensures that these tools are applied consistently across the entire organization, preventing “security silos” where one team is highly protected while another is neglected. By using an ASPM platform, you can orchestrate these various tools from a single pane of glass, reducing noise and providing developers with the context they need to fix issues quickly.
- Key Actions:
- Automate the generation of a Software Bill of Materials (SBOM) for every release.
- Implement automated “guardrails” that block high-risk dependencies from being merged.
- Use template-based infrastructure to ensure all cloud environments are born secure.
5. Monitor, Measure, and Improve the Program Over Time
A security program is never “finished.” Continuous monitoring is required to detect anomalous behavior, such as a sudden change in a trusted dependency or unauthorized access to a build server. Beyond technical monitoring, you must measure the effectiveness of your program using metrics like Mean Time to Remediate (MTTR) and the percentage of vulnerabilities caught before production.
These insights allow you to iterate on your strategy. If certain types of software supply chain vulnerabilities keep appearing, you can adjust your training or update your automated policies to address the root cause. This cycle of measurement and improvement ensures your defenses evolve as fast as the threat landscape.
- Key Actions:
- Conduct regular “red team” exercises focused on supply chain attack vectors.
- Track and report on security debt to maintain visibility for leadership.
- Regularly review and update your third-party risk assessments based on new exploit trends.
Tools for Protecting Software Supply Chain Security
Several types of software supply chain security solutions are essential for strengthening your posture, each addressing different aspects of the software development and delivery process.
The main types of tools for software supply chain security include:
Static Application Security Testing (SAST)
SAST tools analyze source code or binaries for security vulnerabilities without executing the code. They identify issues such as SQL injection, cross-site scripting, and buffer overflows during the development phase.
By catching vulnerabilities early in the development process, SAST tools ensure that insecure code does not enter the supply chain, reducing the risk of downstream exploitation.
Software Composition Analysis (SCA)
SCA tools scan software for third-party components, identify open-source and commercial libraries, and check for known vulnerabilities and license compliance.
These tools provide visibility into third-party dependencies, allowing organizations to detect and remediate vulnerabilities in these components, thereby securing the software from external supply chain threats.
Continuous Integration/Continuous Deployment (CI/CD) Security Tools
These tools integrate security testing into the CI/CD pipeline, automating security checks at various stages of the development and deployment process.
By embedding security into the CI/CD workflow, these tools ensure that security checks are consistently applied, preventing vulnerabilities from being introduced during the build and deployment stages.
Infrastructure as Code (IaC) Security Tools
IaC security tools analyze and enforce security policies on infrastructure code, such as Terraform, CloudFormation, and Ansible scripts, ensuring secure configurations.
By securing the infrastructure configurations, these tools prevent misconfigurations that could lead to vulnerabilities, thus protecting the deployment environment as part of the software supply chain.
Complete ASPM Solutions
Complete Application Security Posture Management (ASPM) platforms like Cycode pull all of these tools together (either via native skills or third-party integration) into a single interface, providing a comprehensive view of an organization’s application security posture.
This allows for centralized monitoring, management, and reporting of security risks across the software supply chain.
Selecting the Right Software Supply Chain Security Solutions for Your Enterprise
Selecting the right software supply chain security vendors is a high-stakes decision that impacts your organization’s risk posture and developer productivity. With the market crowded by point solutions, enterprises must look for platforms that offer more than just a list of vulnerabilities. The ideal solution should provide a clear path from detection to remediation across the entire development ecosystem.
Here is how to evaluate and select the right tools for a modern, secure software supply chain.
Evaluate Coverage Across the Entire SDLC
A truly effective solution must secure the software supply chain from “code to cloud.” This means the tool shouldn’t just look at your open-source dependencies (SCA) or your custom code (SAST); it must also secure the infrastructure that builds and deploys that code. High-quality software supply chain security solutions provide visibility into CI/CD pipelines, build systems, and container registries to ensure no stage of the lifecycle is left unprotected.
If a vendor only covers one or two stages of the SDLC, you are forced to manage “security silos,” which leads to blind spots and fragmented data. Comprehensive coverage ensures that whether an attacker targets a developer’s IDE or a production Kubernetes cluster, your security platform is there to detect and block the threat.
- Key Requirements:
- Native support for SAST, SCA, Secrets Scanning, and IaC security.
- Integration with build tools like Jenkins, GitHub Actions, and GitLab CI.
- Protection for containerized environments and artifact repositories.
Prioritize Tools That Integrate Seamlessly with Developer Workflows
The best security tool is the one that developers actually use. To avoid friction, look for software supply chain security vendors that offer a “controlled shift left” approach. This means providing security feedback directly within the tools developers already live in, such as their IDEs or Pull Requests. When a tool provides a fix suggestion at the moment a developer is writing code, the cost and time of remediation drop significantly.
Avoid solutions that require developers to log into a separate dashboard to view their “security homework.” Integration should be invisible and automated, allowing for security guardrails that guide developers toward safer coding practices without slowing down their release velocity.
- Key Requirements:
- IDE plugins for real-time vulnerability feedback.
- Automated PR comments with actionable remediation guidance.
- Bi-directional synchronization with ticketing systems like Jira.
Assess Visibility, Context, and Risk Prioritization Capabilities
One of the biggest challenges in AppSec is “alert fatigue.” A tool that flags 1,000 vulnerabilities without telling you which ones are actually reachable or exploitable is a burden, not a benefit. Superior software supply chain security tools use “reachability analysis” to determine if a vulnerable library is actually being called by your application in production. This context allows security teams to focus on the 5% of risks that truly matter.
Context also includes understanding the business impact of a specific asset. A vulnerability in a public-facing payment gateway should always be prioritized over a similar flaw in an internal test tool. Ensure your chosen vendor can correlate data across your environment to provide a clear, risk-based priority list.
- Key Requirements:
- Reachability and exploitability analysis to filter out “noisy” alerts.
- Risk scoring based on business criticality and asset exposure.
- Visual mapping of the entire supply chain to see how components are connected.
Ensure Support for Industry Frameworks and Compliance Requirements
As global regulations tighten, your security platform must help you stay compliant with frameworks like SLSA (Supply-chain Levels for Software Artifacts) and NIST SSDF. The right software supply chain security vendors will automate the generation and management of a Software Bill of Materials (SBOM) in industry-standard formats like CycloneDX or SPDX. This is no longer just a best practice; it is increasingly a legal requirement for selling software to government and enterprise clients.
Beyond SBOMs, the tool should provide audit-ready reports that map your security controls to regulatory requirements like SOC 2, ISO 27001, or HIPAA. This automation saves your team hundreds of hours during audit cycles and provides a continuous view of your compliance status.
- Key Requirements:
- One-click generation of machine-readable SBOMs (CycloneDX/SPDX).
- Mapping of security findings to common regulatory and industry frameworks.
- Support for “Policy-as-Code” to enforce compliance guardrails automatically.
Look for Consolidation Opportunities Through ASPM Platforms
Many enterprises suffer from “tool sprawl,” managing dozens of disconnected security scanners. Moving toward an Application Security Posture Management (ASPM) platform allows you to consolidate these tools into a single source of truth. An ASPM like Cycode can ingest data from your existing scanners or replace them with native, high-performance engines, providing a unified view of your cyber supply chain.
Consolidation doesn’t just lower license costs; it improves security by correlating findings from different tools. For example, an ASPM can tell you that a secret leaked in a git repo (found by a secrets scanner) is currently being used to access a production database (found by an IaC scanner). This “big picture” visibility is impossible to achieve with disconnected point solutions.
- Key Requirements:
- Ability to ingest and normalize data from third-party security tools.
- Centralized policy management across the entire AppSec stack.
- Unified reporting and metrics to measure the health of the entire program.
Software Supply Chain Security Best Practices
Collaboration, culture, and a willingness to adopt modern tools and approaches are all essential to a secure supply chain. Based on discussions with dozens of security leaders at ASPM Nation, we recommend the following three software supply chain security best practices:
1. Use a Controlled Shift Left Approach to Vulnerabilities
Shift left refers to the practice of addressing security vulnerabilities earlier in the SDLC when they are easier and less costly to fix. The goal is to address issues sooner, before they become deeply embedded in the codebase.
The problem with shift left is that many developers feel that vulnerabilities have been simply thrown over the fence. They are not given the correct context or data to successfully remediate issues. This unfairly places the burden of security onto developers without giving them the tools to succeed. That’s where the concept of controlled shift left comes in.
Controlled shift left fosters collaboration between security and developer teams. While security teams remain laser-focused on reducing the impact of vulnerabilities, they’re acutely aware of the impact that fixing defects has on developers.
Under this model, security and development work together to find, roll out, and maintain solutions that provide actionable context so that developers can easily fix issues. Organizations benefit from a more resilient software supply chain without slowing developer velocity.
2. Build a Strong Security Culture within Your Organization
Security is a team sport, and that’s not just a rallying cry. Security teams can’t do it alone. Developers are key to creating and deploying secure code. Unfortunately, as our 2025 State of ASPM report shows, 68% of security professionals find implementing a culture of collaboration between security and developer teams challenging.
So how do you build a strong culture of security? Commitment must start at the top. Leadership must make security a priority and be responsible for rolling out clear policies and guidelines, offering consistent and engaging training on secure coding best practices, and encouraging ownership and accountability.
3. Adopt an Application Security Posture Management Solution
To protect your SDLC, the right software supply chain security tools are essential. But too many organizations rely on a hodge-podge of tooling that doesn’t even begin to cover a fraction of software supply chain attack vectors. Not only do these tools leave gaps, but the noise generated by alerts creates a new problem for security and developers: understanding what is really important in terms of risk.
Fortunately, there’s a solution: Application Security Posture Management (ASPM). ASPM is a purpose-built platform for developer security that can integrate with your existing tools or replace them altogether.
An ASPM platform provides visibility, prioritization, and remediation of vulnerabilities across the entire SDLC. Security and development teams gain the visibility, prioritization, and remediation required to reduce the risk of a software supply chain attack.
According to Roland Cloutier (Former Global CSO at TikTok, ByteDance, ADP, and EMC), “ASPM is going to change the way we think about developing code and significantly drive up our quality capabilities across our products.”
Future Trends in Software Supply Chain Security Tools
Security tools are rapidly evolving to meet new demands, but what technologies are forward-looking organizations beginning to adopt that go beyond traditional AppSec controls?
From AI-driven automation to cryptographic validation and global regulatory shifts, these innovations offer a glimpse into the future of software security.
AI-Powered Vulnerability Detection and Response
Artificial intelligence is transforming how organizations detect, prioritize, and respond to software supply chain risks. By analyzing large volumes of code and behavior patterns, AI-powered tools can flag anomalies, predict exploitability, and even recommend or automate remediations. These systems reduce noise, accelerate triage, and help security teams keep up with modern attack speeds.
Zero-Trust Architectures for Development Environments
Zero-trust principles—long established in network security—are now being extended into developer ecosystems. In a zero-trust development environment, every component, process, and user must be authenticated, authorized, and continuously validated. This limits lateral movement, mitigates insider risk, and ensures that only trusted actions are allowed throughout the build and deployment process.
Blockchain-Based Component Verification
Blockchain technology is emerging as a tool for ensuring the authenticity and integrity of software components. By logging each dependency or artifact on an immutable ledger, teams can verify provenance, detect tampering, and establish trust in third-party components.
While still early in adoption, this approach shows promise for high-assurance use cases like critical infrastructure or regulated industries.
Regulatory Evolution and Global Standards
Governments and international bodies are rapidly introducing new regulations and standards to address the rise in supply chain attacks.
From the U.S. Executive Order 14028 to the EU’s Cyber Resilience Act and frameworks like NIST SSDF and SLSA, organizations must now align with stricter guidelines for secure software development. Security platforms must adapt quickly to help ensure compliance across global markets.
Maintain a Secure Software Supply Chain with Cycode
Cycode is an AI-Native Application Security Platform that offers complete visibility, security, and coverage across the software supply chain. Get a clear view of your risk posture and consolidate your stack using native security scanners or plug into third-party security tools via our click-and-connect platform.
Created to help teams fix what matters, Cycode’s platform eliminates alert fatigue and simplifies prioritization and remediation by providing the deep context needed to identify reachability and real-world risk. By unifying security from code to cloud, Cycode ensures your developers aren’t buried in noise, but are instead empowered to resolve the most critical vulnerabilities impacting your business. Experience the industry’s only unified platform built to stop modern supply chain attacks without slowing down innovation.
Book a demo today and see why enterprises choose Cycode to help them manage software supply chain security.
Frequently Asked Questions
What Is Code Security?
By implementing code security, teams can significantly reduce the risk of data breaches and supply chain attacks. This is achieved through a mix of automated scanning and secure coding standards that help developers fix what matters early in the lifecycle. This reduces both the cost of fixing bugs and your overall technical debt.
How Can I Ensure Secure Configuration Management?
To automate this, organizations should use IaC scanning tools to catch misconfigurations (like open S3 buckets or dangerous IAM roles) before they are deployed. Consistent governance across all your DevOps tools is essential to prevent configuration drift. This ensures that your security settings remain hardened throughout the entire software lifecycle.
Why Is Cycode One of the Top Enterprise-Grade Software Supply Chain Security Companies?
Enterprises choose Cycode because we focus on developer productivity. By integrating directly into existing workflows and providing automated, high-fidelity remediation, we help teams solve the most critical risks without the noise of traditional tools. Our platform is built for the scale of global enterprises, providing the visibility and governance required to protect the entire code to cloud journey.
What Are the Top-Rated SCA Tools for Software Supply Chain Security?
Cycode’s native SCA capabilities stand out by providing code to cloud traceability. This means you can see not just that a library is vulnerable, but exactly where it is used, who introduced it, and whether it is actually exposed to the internet. This level of context is what separates enterprise grade supply chain security from basic dependency scanning.


