Checkmarx Alternative For Application Security Testing
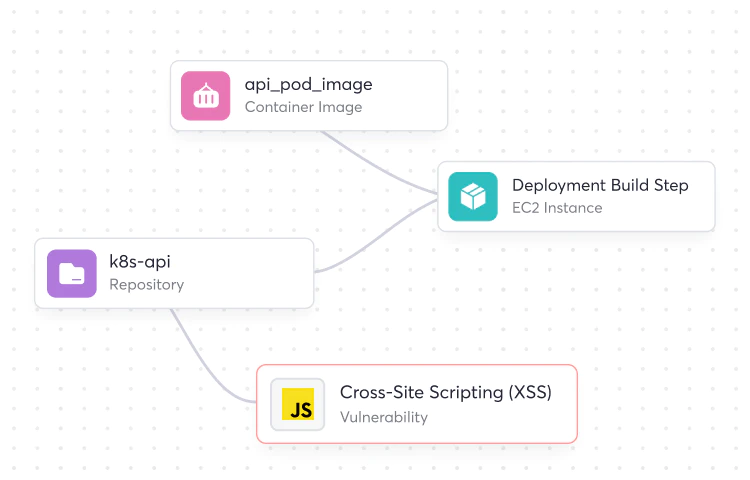
Securing applications and the software supply chain requires understanding the relationships between applications, components, people, tools, pipelines, runtime environments, and risks. The Cycode platform, one of the top Checkmarx competitors, was purpose-built to fill the visibility gaps that have historically frustrated application security programs
Book a Demo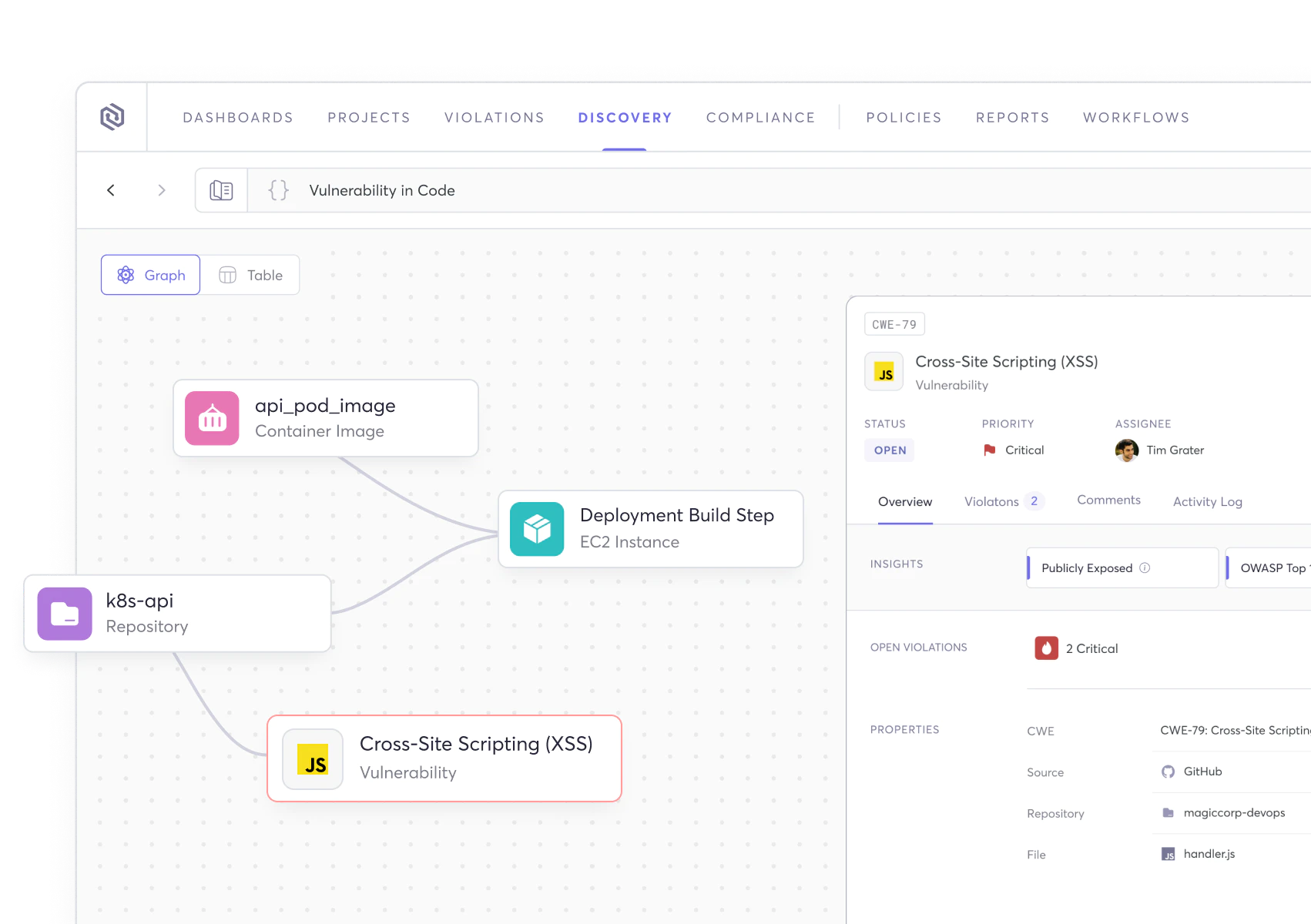
Protect Secrets
Identifies secrets across the entire SDLC - source code, build logs, Infrastructure as code, Kubernetes clusters, version histories, Docker images and productivity tools (e. g. Slack).
detect Leakage
Identifies leakage of private code and secrets in GitHub and GitLab public repositories and code snippets.
Harden SDLC Tools
Enforces secure configurations and best practices.
Secure Code
Identifies vulnerable application code with SAST.
Secure Code Dependencies
Identifies vulnerable code with SCA.
Secure Infrastructure as Code
Identifies IaC misconfigurations.
Protect CI/CD Pipelines
Next-gen SCA to protect against use of insecure tools, modules, dependencies in pipelines, prevent tampering.
Protect Cloud Deployment
Identifies misconfigured cloud resources and drift from IaC.
Protect Secrets
Identifies secrets across the entire SDLC - source code, build logs, Infrastructure as code, Kubernetes clusters, version histories, Docker images and productivity tools (e. g. Slack).
Partial - Limited ability to detect secrets only in code
detect Leakage
Identifies leakage of private code and secrets in GitHub and GitLab public repositories and code snippets.
None
Harden SDLC Tools
Enforces secure configurations and best practices.
None
Secure Code
Identifies vulnerable application code with SAST.
Secure Code Dependencies
Identifies vulnerable code with SCA.
Secure Infrastructure as Code
Identifies IaC misconfigurations.
Protect CI/CD Pipelines
Next-gen SCA to protect against use of insecure tools, modules, dependencies in pipelines, prevent tampering.
None
Protect Cloud Deployment
Identifies misconfigured cloud resources and drift from IaC.
Partial - Unable to scan in the cloud runtime, can't protect against drift
Secure SDLC Foundation
Cycode ensures tools are configured securely, roles are segmented and permissions audited, and security best practices are followed throughout the application lifecycle.
Pipeline Integrity
Cycode protects code and container dependencies, as well as pipeline dependencies such as open source build tools, pipeline actions and plugins, and infrastructure modules.
contextual Insights
Cycode monitors the entire SDLC and reports findings with full context so you can avoid manual investigation and prioritize the most important findings.
Unparalleled Platform
Cycode delivers a seamless user experience with comprehensive reporting dashboards for security pros and deep integrations with developer workflows to shift security left without context switching.
Risk Based Prioritization
With visibility from code to cloud, Cycode eliminates silos to understand your application, dependencies, CI/CD pipelines, and runtime environments.
Instant Value
Integrate your DevOps tools in less than 1 minute to deliver immediate value and allow maximum agility across your SDLC, all without complicated pricing or packaging.
Looking for a Live Demo?
Our Cycode experts will answer your questions and provide more info about the platform with a live-action demonstration.
Frequently Asked Questions
What is Checkmarx?
Checkmarx does have limitations though, particularly in detecting secrets and code leaks, securing CI/CD pipelines, and managing misconfigurations in cloud environments, which are increasingly critical for modern application security
How Does Checkmarx Work?
At its core, it parses your codebase into a logical structure that allows it to identify issues like injection flaws, hardcoded credentials, and insecure configurations without executing the code. Findings are then surfaced through its dashboard or pushed directly into developer workflows like IDEs or ticketing systems.
Checkmarx also offers supplementary tools like SCA and IAST through its broader Checkmarx One platform, though these are often used separately from the core static analysis engine. Its strength lies in its breadth of language support and customizable scanning rules, though it can require substantial tuning and expertise to minimize false positives and streamline remediation.
What Are the Specific Limitations of Checkmarx Application Security?
- High False-Positive Rates: Users report needing significant manual triage to manage noise.
- Performance Bottlenecks: Slow scans on large codebases; high resource usage can hinder CI/CD velocity.
- Complex Setup & UX: Integration and tuning require considerable time and expertise; UI can overwhelm newcomers.
- Costly Licensing: Targeted at large enterprises; steep pricing may deter smaller teams.
- Limited Extensibility: Although comprehensive, gaps exist in DAST commonly; newer ecosystems or frameworks may require third‑party add-ons.
These limitations help explain why organizations consider solutions like Cycode, which promise unified coverage with leaner workflows, fewer false positives, and faster ROI.
What Should I Look for in Checkmarx Alternatives?
- Visibility: Ensure the most comprehensive visibility into their code, including source code, open source code, and AI-generated code. You can't fix what you can't see.
- Prioritization: The tool should help reduce the noise of false positives and ensure the focus remains on the most critical issues that need resolution.
- Remediation: Effective developer workflows that enable seamless remediation of vulnerabilities within the developers' own environments.
- Tool Consolidation: A platform that can replace or provide seamless integration with existing security tools, offering a unified solution for better security and hygiene of the entire CI/CD pipeline.
An application security posture management (ASPM) platform like Cycode meets these needs by providing secure and compliant proprietary scanners for better prioritization, supporting enhanced collaboration between Sec and Dev teams. As a Checkmarx alternative, Cycode ensures comprehensive visibility, efficient prioritization, streamlined remediation processes, and effective tool consolidation to strengthen your security posture.
Why Is Cycode One of the Best Checkmarx Competitors?
- Software Supply Chain Security: Ensure end-to-end security, including secret detection and code leakage identification.
- Application Security Testing: Leverage proprietary scanners such as SAST and Next-Gen SCA. This includes comprehensive scanning of proprietary code, open source libraries, and AI-generated code.
- Third-party Integrations: Help security teams and developers gain a comprehensive understanding of their application security posture by integrating all your third-party and security tools.
- Risk Intelligence Graph (RIG): Gain enhanced visibility, prioritization, and remediation of critical vulnerabilities.
- Developer Experience: Enable developers to address critical vulnerabilities within their own environments without needing to log into Cycode.