There’s no surprise that in today’s lightning fast paced development environment, speed, and efficiency are non-negotiable. Developers bear the weighty responsibility of delivering high-quality, secure cloud applications at a breakneck pace, in direct response to ever increasing market demands. Nevertheless, security and dev teams find themselves grappling with a myriad of daunting challenges:
- Managing the burden, cost, and inefficiencies of having too many siloed (and vendor-locked) security tools from code to cloud (SAST, SCA, Secrets, IaC, etc.)
- The incessant backlog of alerts (and false positives) with zero developer context
- Navigating a web of intricate development environments, tools, people, and processes
- Keeping up with an evolving threat landscape and compliance requirements
These hurdles often sow disagreement between security and development teams, resulting in unhealthy friction. This divergence in goals – what we call AppSec Chaos – contributes to a crescendo of alert fatigue, sluggish innovation, and critical alerts slipping through the cracks, all of which significantly erode trust between Security and Dev.
It’s finally time to bring in a new philosophy that brings security and dev teams working better together — transforming AppSec into a team sport.
This is why we’re excited to continue empowering every software-first Fortune 100 to 100,000 organization to deliver software fast without compromising on security through Cycode’s complete approach to Application Security Posture Management (ASPM).
Complete Visibility, Security, and Coverage — Instantly
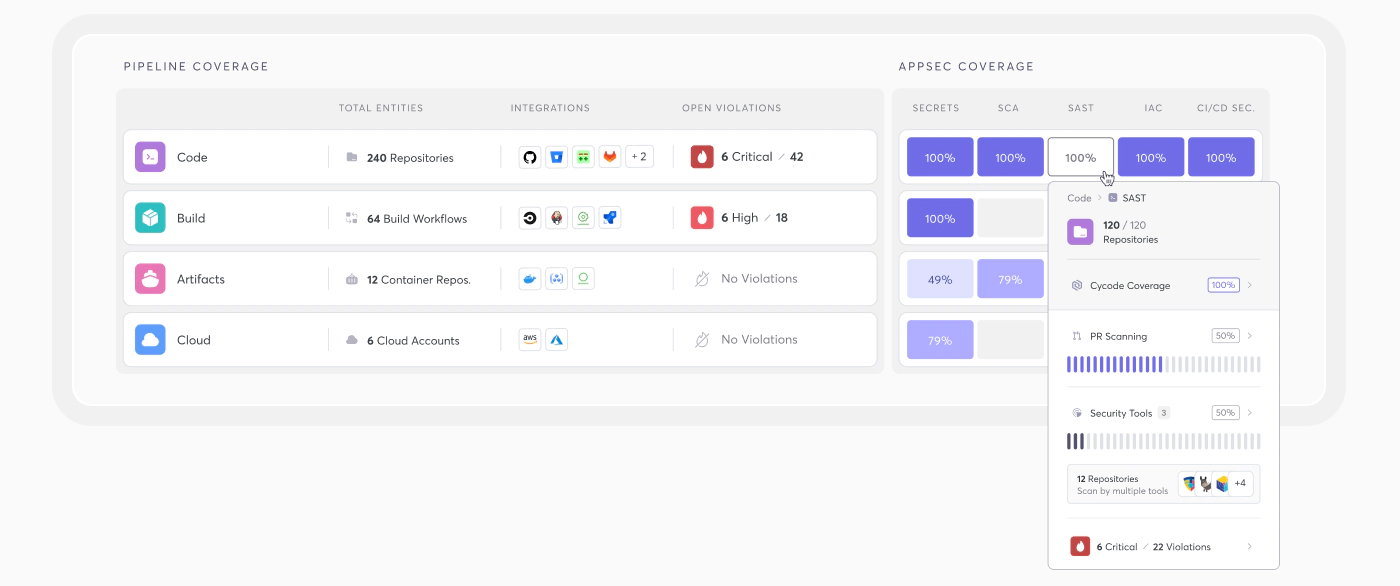
So what does a “complete approach” to ASPM actually mean? Even though it’s technically difficult to do, we’ve made it shockingly simple for our customers by making full visibility into their risk posture a reality, no matter what tools they use.
Cycode’s ASPM stands as the complete platform for providing the ability to use its own native security solutions, but also the ability to add any third-party security solution through its new third-party, ASPM specific, click and connect platform — ConnectorX.
ConnectorX comes at a time where many organizations have invested in existing security solutions (i.e. SCA, SAST, etc.), so this allows a quick way to ingest any vulnerability type, or source into our ASPM platform for complete visibility. ConnectorX has been thoughtfully designed for breadth and scalability, already welcoming connectors from industry leaders like BlackDuck, Wiz, in addition to many more. This is inclusive to the already pre-built set of 40+ integrations we have today with coverage across the entire SDLC.
Now through any source, we’ve the ability to get you to visibility in 5 minutes to deliver you an automated, accurate, and real-time application inventory encompassing every tool, library, code component from APIs and data models to dependencies and cloud infrastructure. In addition, Cycode’s instant understanding of developers knowledge allows for continuous monitoring of any changes, enabling you to map your application architecture and attack surface in real-time.
With the 40+ existing integrations and the all-new ConnectorX, Cycode provides an unparalleled view of your security landscape, consolidating signals and vulnerabilities into a single pane of glass. This gives you the freedom to choose and connect with native or third-party scanners. This complete approach ensures Security and Dev teams can effectively address the complexities and inefficiencies associated with siloed and vendor locked tools.
Smarter, Laser-Focused Prioritization Through the Risk Intelligence Graph
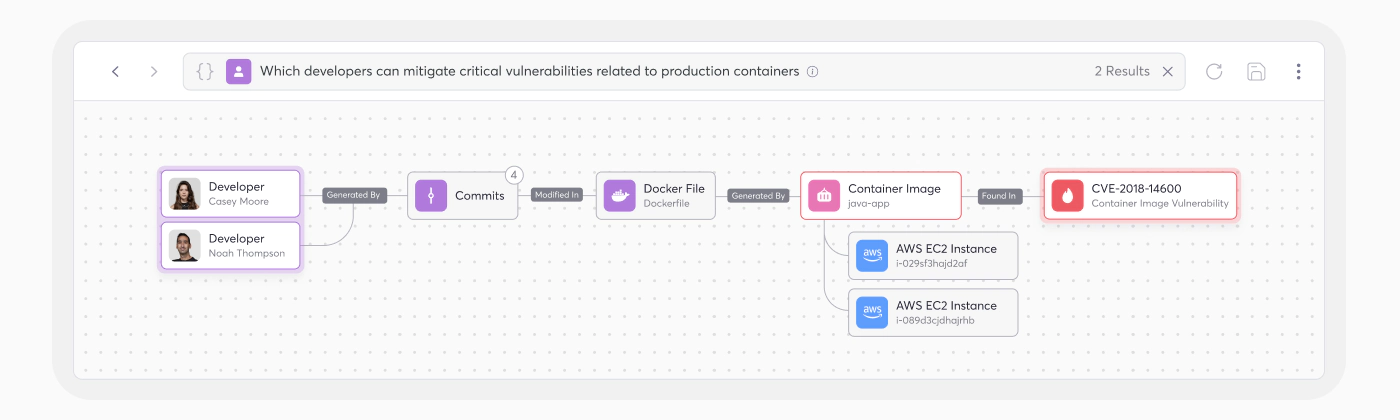
Through all this visibility and discovery, the Risk Intelligence Graph (RIG) is able to make it much easier to intake those thousands of vulnerabilities from any of your security solutions (native or via ConnectorX) in order to bring focus to the 1% of critical vulnerabilities that matter most for your Security and Dev teams. Here’s some of what you can expect through the power of the RIG:
- Business impact driven – prioritize based on risk score, high impact severity, and proximity to production
- Code to cloud traceability – pinpoint usage, and exactly what’s driving the different types of vulnerabilities between code to cloud for the fastest path to remediation
- Clear ownership identity – tie vulnerabilities from code to cloud back to their owners so they can get all the context and take action to fix it
- Blast radius reduction – see the broader organizational impact of individual or duplicate vulnerabilities so you can help remediate at scale
- Threat intelligence – proactive security notifications within the platform that provides updates on zero day attacks and threats with out-of-the-box policies to make sure MTTR on those zero day attacks are drastically reduced rather than trying to take days or weeks to resolve.
With the power of the RIG, there’s more context of the application. Now you can associate risk to code owners, assess root cause, and ultimately remediate and prevent risks from being deployed to the cloud.
Controlled Shift Left and Remediation at the Speed of DevOps
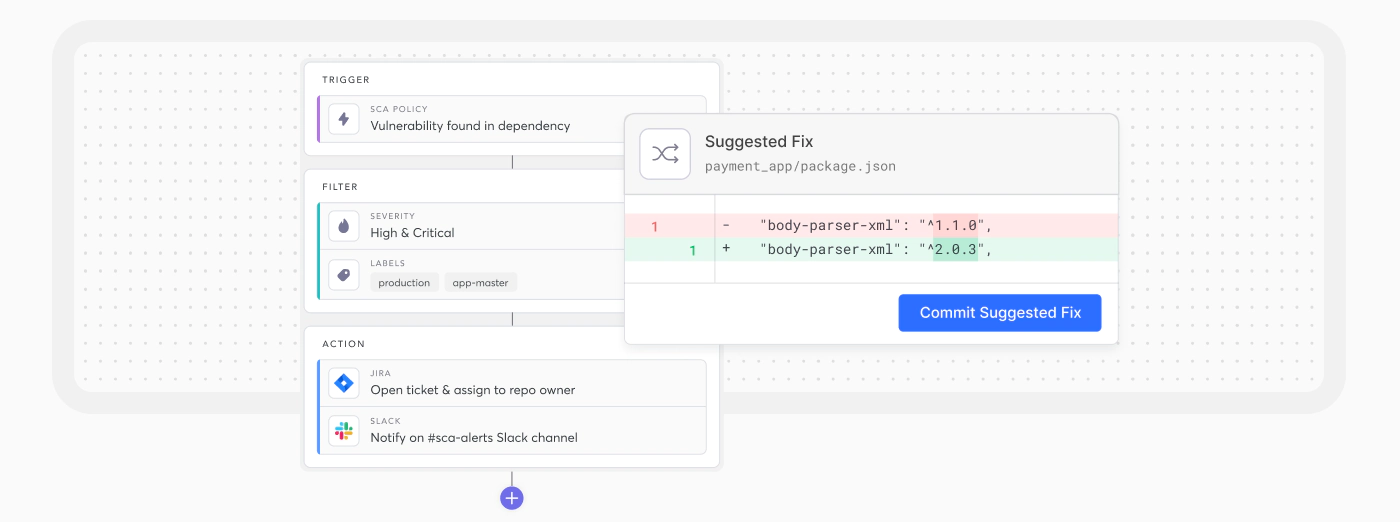
As an industry, we have finally learned that the Shift Left movement hasn’t lived up to its promises. Essentially, Shift Left was an easy way for security to throw noisy alerts over the wall to developers without any context or knowledge on how to fix them. This is disruptive, reduces productivity, and ultimately impacts the business.
We believe in a more balanced approach, called Controlled Shift Left. Our approach empowers your developers by meeting them where they work, enabling you to provide the necessary guardrails for secure, high-velocity development.
Conclusion and Parting Thoughts
Cycode’s complete approach to Application Security Posture Management (ASPM) unites Security and Dev teams with instant visibility, intelligent prioritization through the Risk Intelligence Graph (RIG), and a balanced Controlled Shift Left approach, ensuring secure, high-velocity development in today’s fast-paced landscape.
If you’re excited to discover how your Security and Dev teams can achieve Peace of Mind with the only complete ASPM, don’t hesitate to get in touch and take it for a test drive! Book a demo now to find out how we can help you achieve faster time to value, reduce critical vulnerabilities, and remediate faster.
Originally published: November 14, 2023