Open-source software has become a cornerstone of modern development, offering flexibility and efficiency. However, this reliance introduces complexities in securing these dependencies. That’s because traditional security tools often overlook vulnerabilities within third-party components, opening the door for significant security and compliance risks.
It’s no wonder 63% of security leaders believe CISOs aren’t investing enough in code security.
To address these challenges, Software Composition Analysis (SCA) tools have emerged, specifically designed to identify and manage risks associated with open-source components. This guide explores the key methodologies and capabilities that developers and security teams should prioritize when selecting an SCA tool.
Key Takeaways:
- SCA is essential for securing open-source dependencies but works best as part of a broader AppSec strategy.
- Must-have features for SCA tools include continuous vulnerability detection, risk-based prioritization, dynamic SBOM tracking, automated policy enforcement, and seamless developer integration with CI/CD pipelines and IDEs.
- Security leaders should evaluate beyond a feature list and consider factors like proprietary vs. open-source scanners, AI-driven automation, and correlation with other security signals for more accurate risk assessment.
What Are Software Composition Analysis (SCA) Tools?
Software Composition Analysis (SCA) tools are specialized security solutions designed to identify, analyze, and manage open-source and third-party components within an application’s codebase. Unlike Static Application Security Testing (SAST) tools, which ensure the security of your proprietary code, SCA tools provide visibility into the software supply chain, detecting vulnerabilities, licensing issues, and potential risks associated with external dependencies.
Note: For a comprehensive security posture, it’s essential to employ both SCA and SAST tools. To delve deeper into SAST solutions, consider reading our SAST Buyer’s Guide.
Benefits of Using Software Composition Analysis Tools
Incorporating SCA tools into your development process offers several advantages:
- Enhanced Security: Proactively identify and remediate vulnerabilities in third-party components, reducing the risk of exploitation.
- License Compliance: Ensure adherence to open-source licenses, preventing potential legal and operational complications.
- Operational Efficiency: Automate the monitoring and management of software components, streamlining workflows and reducing manual efforts.
- Risk Mitigation: By managing component risks effectively, SCA tools help minimize the attack surface and enhance the overall security posture of applications.
Want a more detailed overview of SCA and its tools? We recommend reading Cycode’s comprehensive primer on What Is Software Composition Analysis (SCA)?. If you’re at the tool evaluation stage, keep reading.
SCA Tools You Should Be Using
Using an SCA tool like Cycode is essential for securing your software supply chain. But the best security teams know that effective software composition analysis isn’t just about a single tool; it’s about an ecosystem of practices and methodologies that provide deep security insights, improve risk management, and enhance developer workflows
Cycode partners with leading development and security teams across industries, giving us a front-row seat to the strategies that work at scale. If you’re serious about securing your open-source dependencies, these are the additional “tools” you should have in your developers’ toolkit.
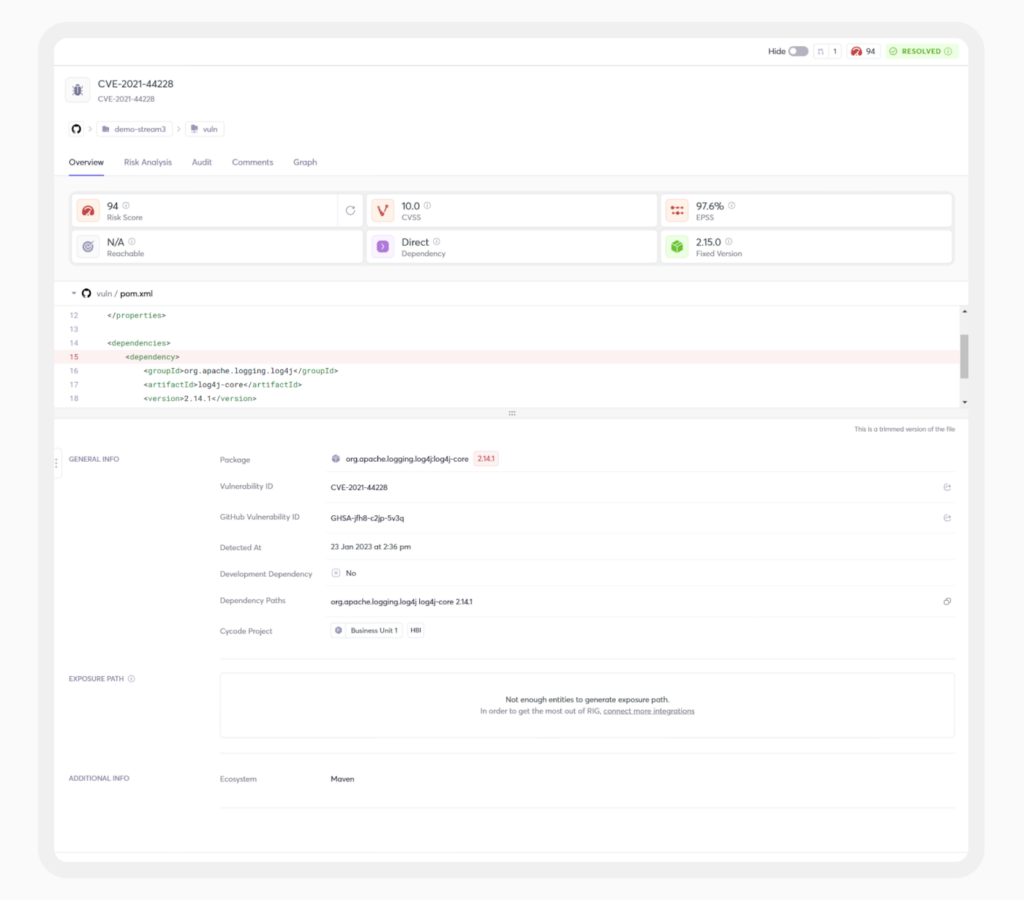
Continuous Vulnerability Detection & Prioritization
Traditional SCA tools rely on periodic scans, which means vulnerabilities can go undetected between checks. A more effective approach is continuous monitoring that catches risks in real time, ensuring that security teams can address them before they become a liability. Importantly, though, not all vulnerabilities require immediate attention. That’s why risk-based prioritization is also key.
Cycode’s approach streamlines this process by reducing noise and surfacing the vulnerabilities that truly need to be addressed, based on exploitability, code reachability, and business impact. This allows security and development teams to focus their efforts where they’ll have the most impact.
Supply Chain Security & SBOM Management
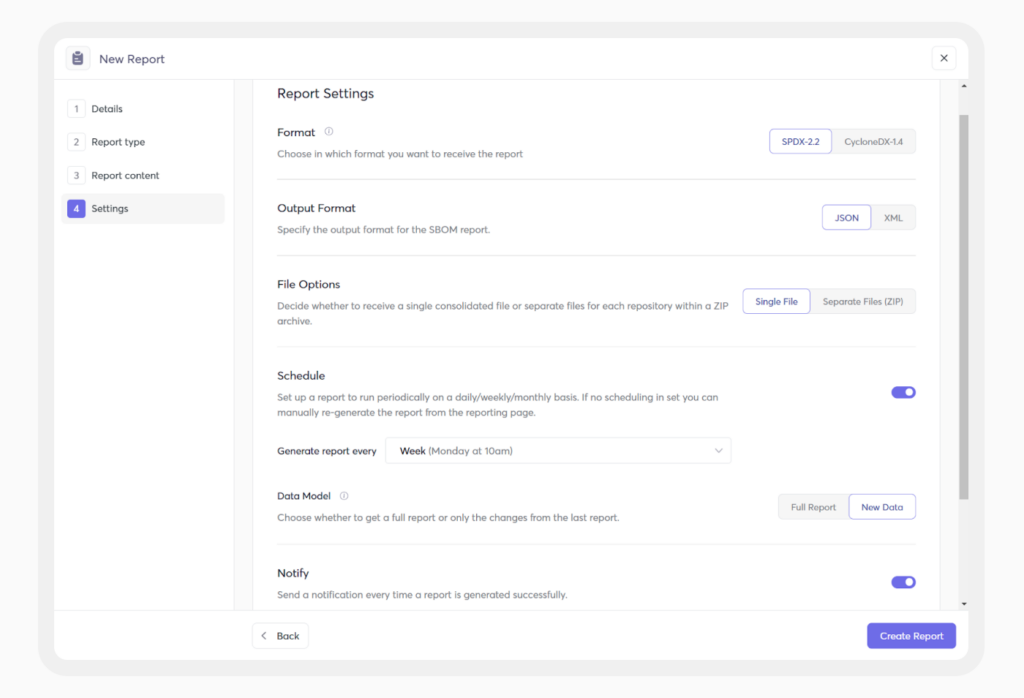
A Software Bill of Materials (SBOM) is foundational for understanding and securing your software supply chain. But teams shouldn’t make the mistake of thinking that they can generate an SBOM once and assume they’re covered. The reality is that software dependencies change frequently, and a static SBOM quickly becomes outdated, leaving security gaps.
A modern approach involves dynamic SBOMs that update automatically as dependencies evolve, ensuring security teams always have an accurate view of their software components. Cycode, for example, provides real-time SBOM tracking, giving teams the ability to monitor their supply chain proactively rather than reactively.
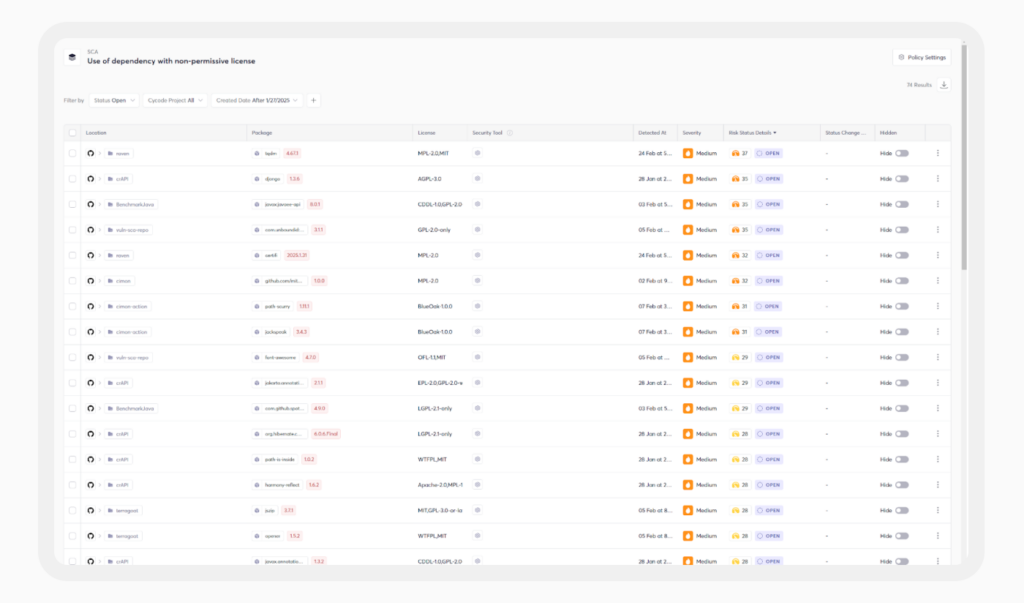
Open-Source License Compliance & Policy Enforcement
Managing open-source licenses isn’t just about legal compliance—it’s about protecting your business from unnecessary risks. Without visibility into the licenses governing your dependencies, your team could unknowingly introduce software that conflicts with your business model or legal obligations.
Of course, manually reviewing each license isn’t scalable, especially in fast-moving development environments. Automated license detection and enforcement streamline this process by flagging problematic licenses before they make their way into production.
Cycode’s SCA capabilities integrate license risk detection and policy enforcement, helping teams stay compliant without slowing down development.
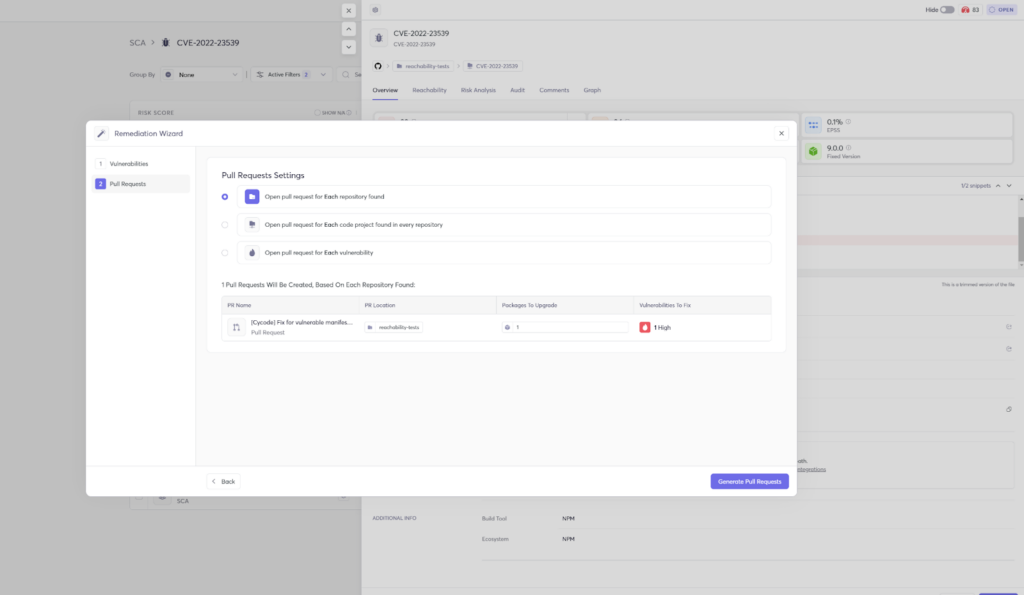
Developer-Centric Security & CI/CD Integration
If security feels like a roadblock, developers will find ways to bypass it. That’s why modern SCA tools must integrate seamlessly into CI/CD pipelines, code repositories, and even IDEs.
But security should do more than detect vulnerabilities. It must also enable developers to fix issues efficiently and maintain high velocity in software delivery.
The best solutions don’t just alert developers to issues—they provide actionable remediation guidance within the tools they’re already using. Cycode ensures that security is built into every stage of the development process, from commit to deployment and offers features like bulk remediation to make it easier for developers to fix vulnerabilities without friction.
Code Provenance & Open-Source Risk Monitoring
Some open-source packages are well-maintained and actively updated, while others are abandoned or vulnerable to attacks. Understanding where your dependencies come from, who maintains them, and whether they’re at risk of abandonment is crucial to securing your supply chain.
Proactive monitoring can help identify packages with suspicious activity—such as sudden changes in ownership or unusual update patterns—before they become a threat. Cycode employs AI-driven risk monitoring to provide teams with the context they need to make informed decisions about their dependencies.
SCA Reachability
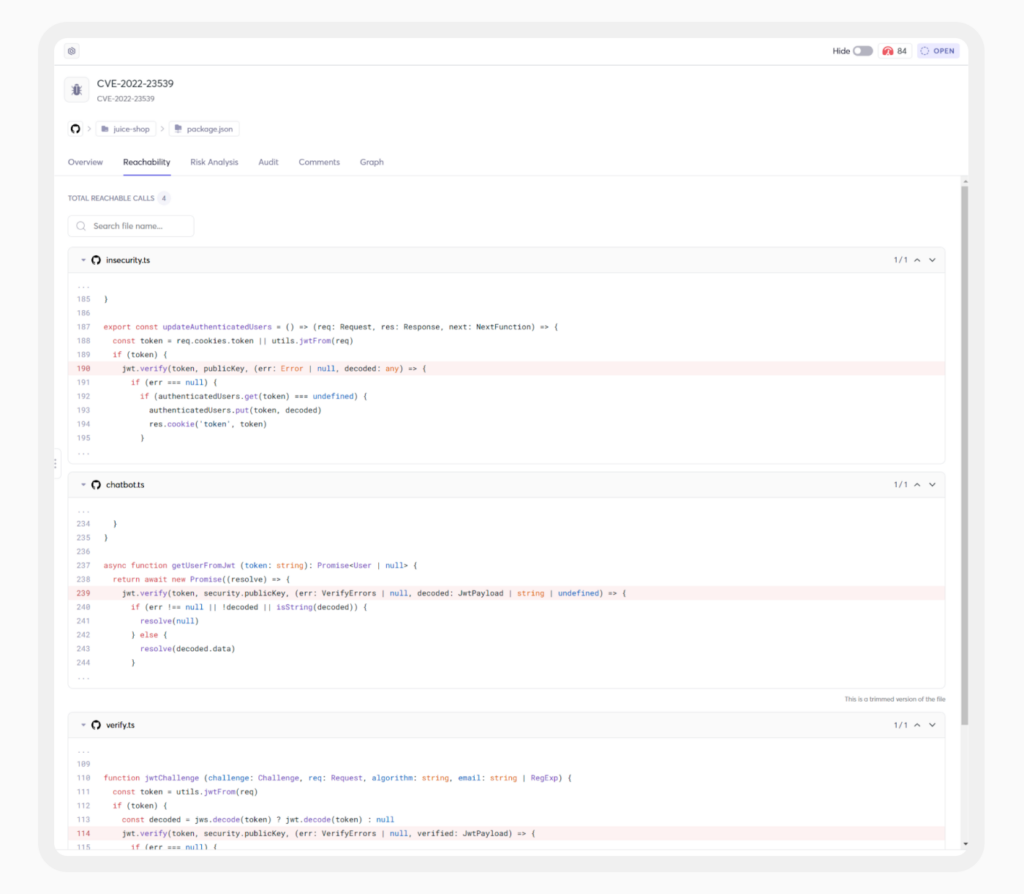
Traditional SCA tools flag vulnerabilities based on whether a package exists in an application’s dependencies. But this often leads to false positives, as many flagged vulnerabilities never actually run in production.
SCA reachability analysis solves this by determining whether vulnerable code is actually executed in the application. By focusing on vulnerabilities that are actively called, teams can filter out noise, prioritize real threats, and improve remediation efficiency.
Cycode’s SCA Reachability Analysis helps teams focus on vulnerabilities that truly matter, reducing security noise and ensuring remediation efforts are aligned with actual risk.
Key Considerations When Selecting an SCA Tool
As we’ve outlined above, a strong SCA tool should have key features that align with modern security and development needs, including:
- Continuous vulnerability detection to identify risks in real time
- Risk-based prioritization to focus on vulnerabilities that truly matter
- Dynamic SBOM tracking for real-time visibility into software dependencies
- Automated policy enforcement to streamline compliance
- Seamless developer integration with IDEs, CI/CD pipelines, and existing security tools
However, simply checking a feature list doesn’t tell the whole story. Security leaders need to look beyond basic capabilities and evaluate whether an SCA solution is truly built to meet the evolving needs of their organization.
Beyond features, here are the critical factors that separate the best SCA tools from the rest:
- Scalability: Can the tool handle large-scale repositories, monorepos, microservices, and complex CI/CD workflows as your company grows?
- Use of AI and Automation: Does the solution leverage AI to reduce false positives, prioritize threats, and streamline security workflows, or does it rely solely on static databases?
- Proprietary vs. Open-Source Vulnerability Scanners: Some SCA tools rely on open-source databases, which may lag in identifying emerging threats. Proprietary scanners (like those employed by Cycode) can provide more comprehensive detection and deeper insights.
- Platform vs. Point Solution: Is the tool a standalone product, or does it integrate into a broader Application Security Posture Management (ASPM) platform? A unified security approach can reduce fragmentation and improve overall risk visibility.
- Developer Experience: Does the tool provide actionable remediation guidance within the developer’s workflow, or does it create bottlenecks that slow down development?
- Compliance Readiness: Does the tool support compliance frameworks like NIST, ISO, and SOC 2 with automated reporting and policy enforcement?
- Reachability analysis to prioritize vulnerabilities that are actually exploitable in runtime.
Use this table to help vet vendors and ensure you select an SCA tool that not only detects vulnerabilities but also supports broader security objectives and development efficiency.
| Feature | Why It’s Important |
| Continuous Vulnerability Detection | Ensures risks are identified in real-time rather than waiting for scheduled scans. Reduces the window of exposure. |
| Risk-Based Prioritization | Helps teams focus on vulnerabilities that are actually exploitable, reducing security noise and preventing alert fatigue. |
| Dynamic SBOM Tracking | Keeps track of changing software dependencies, ensuring security teams always have an up-to-date view of risks. |
| Automated Policy Enforcement | Prevents risky dependencies from entering the codebase by enforcing security and compliance rules automatically. |
| Seamless Developer Integration | Embeds security into developer workflows (CI/CD pipelines, IDEs), making it easy to fix issues without disrupting development speed. |
| Proprietary Vulnerability Database | Detects risks faster than tools relying only on public sources, ensuring more accurate and comprehensive coverage. |
| AI-Driven Automation | Reduces false positives, speeds up remediation, and improves efficiency through context-aware security insights. |
| Platform vs Point Solution | A platform approach (like ASPM) integrates SCA with other security tools (SAST, CI/CD security, secrets scanning), reducing tool sprawl and improving risk correlation. Point solutions lack this broader context. |
| Reachability Analysis | Determines whether a vulnerable piece of code within a dependency is actually executed in an application, helping security teams prioritize real threats over theoretical risks. |
Looking for more tips? Download our SCA tools cheat sheet.
Why Cycode? A Smarter Approach to SCA
Cycode takes a smarter approach to Software Composition Analysis by integrating SCA within a complete ASPM platform. Unlike standalone SCA tools, Cycode correlates vulnerabilities across the SDLC, providing full risk visibility.
But Cycode doesn’t just stand out as an alternative to point solutions. It also stands out as the leading ASPM platform on the market. Here’s why:
- Proprietary Scanners for Deeper Detection: Unlike tools that rely solely on public vulnerability databases, Cycode’s proprietary scanners uncover hidden risks that others miss, providing more comprehensive security.
- Risk-Based Prioritization: Cycode’s Risk Intelligence Graph (RIG) correlates security data across the SDLC, ensuring teams focus on vulnerabilities that actually matter, reducing noise by up to 80%.
- Developer-Friendly Remediation: Cycode integrates directly into developer workflows, providing actionable remediation guidance and automation that helps fix issues quickly—without disrupting velocity.
Want to see how Cycode’s approach to SCA simplifies security without slowing down development? Schedule a demo today.
Frequently Asked Questions
What’s the Difference Between SAST Tools and SCA Tools?
How Do SCA Tools Work?
What Is the Purpose of Software Composition Analysis?
Effective SCA helps organizations reduce security debt, minimize legal risks, and maintain the integrity of their software products.
How Do You Implement SCA Tools Into Workflows Effectively?
- Conduct an initial dependency audit to assess risk and establish baseline security metrics.
- Embed SCA into CI/CD pipelines to automate scanning during code commits, builds, and pull requests.
- Enable real-time SBOM tracking to maintain up-to-date visibility into all software components.
- Enforce policy-driven security controls to govern acceptable licenses and vulnerability thresholds.
- Automate remediation workflows to help developers fix issues without slowing down releases.
- Monitor continuously and adapt based on emerging threats and evolving security policies.



