JFrog and Cycode created an integration that will improve the security of our customers’ digital assets and dependencies. In light of a rise in breaches originating from artifacts, namely software supply chain attacks, there couldn’t be a better time to demonstrate how Cycode hardens and fortifies JFrog instances without slowing down release velocity.
JFrog is an industry-leading DevOps platform, serving a variety of organizations including blue-chip software companies including Meta (formerly known as Facebook), Amazon, Apple, Netflix, and Alphabet (formerly known as Google). Many startups also use JFrog tools. JFrog’s universal package repository has the ability to support a variety of package and dependency types; their cloud-native CI/CD pipeline provides end-to-end orchestration and optimization of all stages within the build and deployment pipeline. When you combine JFrog’s management system with Cycode’s knowledge graph, you have a secure solution providing oversight on assets from production to deployment.

To develop a modern application with competitive features, developers must rely on third-party integrations and software–it’s not uncommon for dependencies to compose upwards of 90% of an application’s codebase. Each dependency carries its own risk that the end application must address; according to the NIST SSDF, this may be defined as inherited risk. To mitigate this risk, organizations should take inventory of each artifact and assess the security of each component.
Maximizing developer productivity is the main focus of many software organizations. An emphasis on developer experience and agility characterizes recent innovations within the software development life cycle (SDLC), but security has not kept pace. There exists a pronounced lack of security tools and security visibility into new technologies.
JFrog’s Cycode integration enhances the security of the software supply chain. The implemented functionality’s overarching goal is to allow visibility of artifacts throughout the CI/CD pipeline. We subdivide this functionality into two parts: JFrog Artifactory features and JFrog Pipeline features.
JFrog Artifactory Integration with Cycode
At its core, JFrog Artifactory is a tool for storing artifacts, or components needed to help create a piece of software such as binaries or docker images. One of JFrog Artifactory’s strengths is its ability to handle so many different types of repository types. Debian, RPMs, Maven, Docker, Helm, and many others are supported, making JFrog Artifactory especially attractive to enterprises with mixtures of modern and legacy software.
Security teams often want to vet artifacts to help mitigate the risk of supply chain attacks, and this approach is being widely adopted across the industry. Google has recently released a framework with the explicit purpose of verifying artifact integrity across the supply chain, reflecting an increased need for tools to help achieve high levels of security.
The Cycode integration with JFrog helps encourage best security practices by scanning artifacts including binaries, docker images, and more for vulnerabilities. Cycode’s functionality includes preventing escaped secrets, identifying potential IaC misconfigurations, and detecting code leaks. This helps eliminate vulnerabilities caused by a lack of visibility into all parts of a CI/CD pipeline.
Cycode inventories Artifactory assets, which enables mutual customers to define custom policies based on events or artifact types. This can help enhance governance by auditing for excess privileges to ensure that all dependency updates are performed by approved admins; this is one example of the integration helping organizations adhere to SLSA standards, reducing the chance of a supply chain attack. The Cycode platform further promotes security best practices by verifying the provenance of production containers to confirm they’re from approved registries–this reduces the risk of code tampering.
JFrog Pipeline Integration with Cycode
JFrog Pipeline is an automated solution for building, testing, and deploying software as part of the CI/CD pipeline. The integration of Cycode into JFrog pipelines makes it straightforward to scan code, artifacts, and the CI/CD pipeline for secrets, misconfigurations, and leaks thanks to Cycode’s knowledge graph.
Cycode’s knowledge graph aggregates asset information, events, metadata, and user activity from DevOps tools, infrastructure, and security scanners across your entire SDLC. It then correlates seemingly disparate events to create contextual insights, prioritize remediation, reduce false positives, and ensure the integrity of the pipeline. Cycode’s knowledge graph allows the company to think like an attacker by identifying issues across a company’s software pipeline rather than only focusing on individual services; this helps provide security visibility and helps mitigate the risk of attacks through code tampering.
The Cycode integration with JFrog Pipelines allows for pipelines to be synchronized with Cycode’s knowledge graph–these pipelines are referred to as “Build Workflow” within the knowledge graph. Each pipeline has execution history, logs, and other attributes which are all accessible within Cycode. This accessibility enables functionality to peruse an auditable software bill of materials. The following queries offer a glimpse as to the capabilities of the knowledge graph. Users may explore pipeline executions to perform various knowledge graph queries.
- Let’s say we want to return instances where build workflows failed execution:
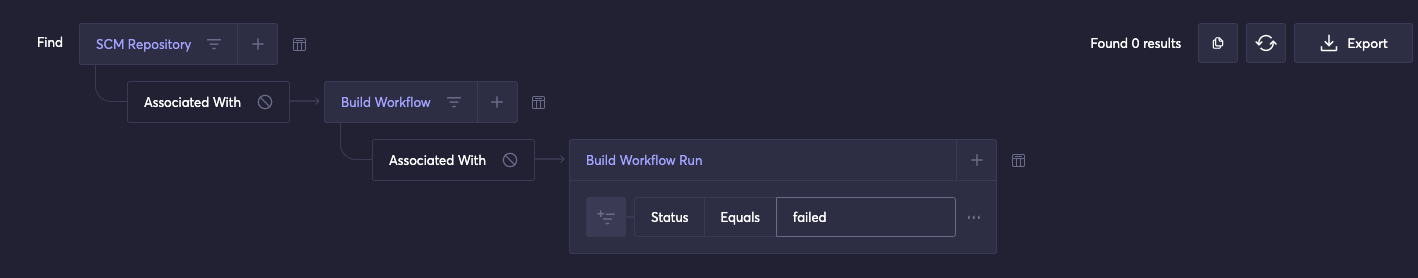 This query may be described as “For repo X -> get all build workflows -> where build workflow has run -> find failed runs.”In this scenario, the knowledge graph returns a list of build workflow runs that exited with a failed status. The knowledge graph scans the JFrog CI/CD pipeline and identifies build workflows that fail, providing enhanced visibility. Users may also parse logs associated with a pipeline using the knowledge graph.
This query may be described as “For repo X -> get all build workflows -> where build workflow has run -> find failed runs.”In this scenario, the knowledge graph returns a list of build workflow runs that exited with a failed status. The knowledge graph scans the JFrog CI/CD pipeline and identifies build workflows that fail, providing enhanced visibility. Users may also parse logs associated with a pipeline using the knowledge graph. - To determine if the records contain secrets, we may use a query similar to this:
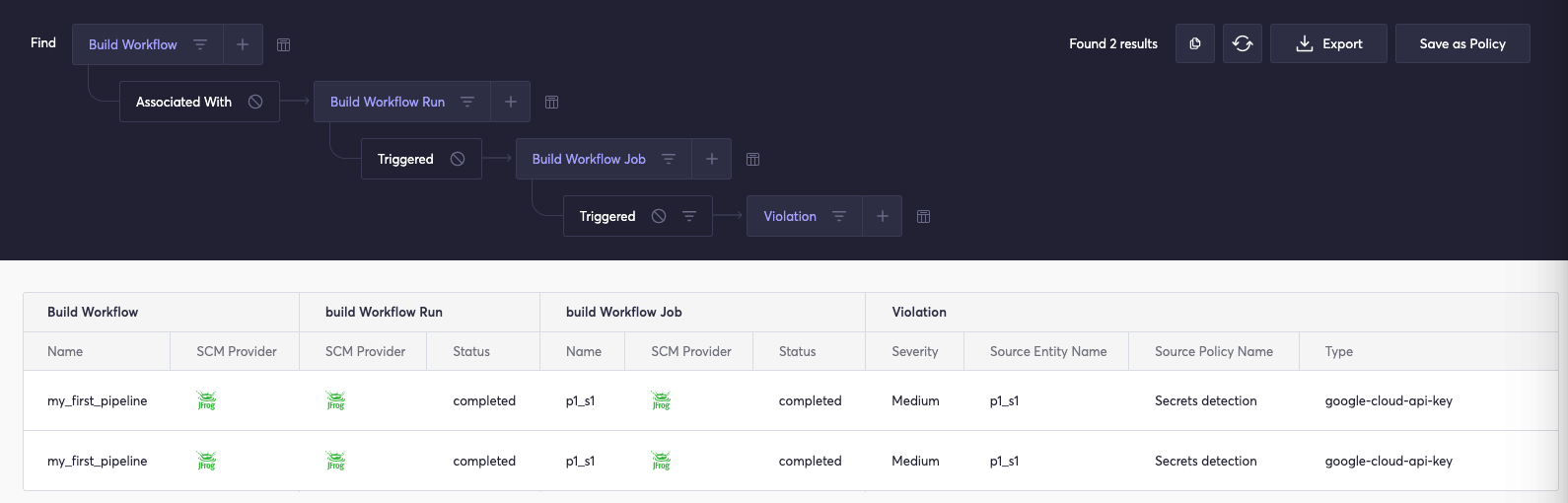
Filtering by “Build Log” in the secrets explorer allows us to track down any hard-coded credentials that reside in a vulnerable place. In the case of the JFrog integration, this will enable us to identify credentials that have made their way into Artifactory or the CI/CD pipeline.
On JFrog’s platform, within pipelines, we may view the builds where hard-coded credentials are introduced: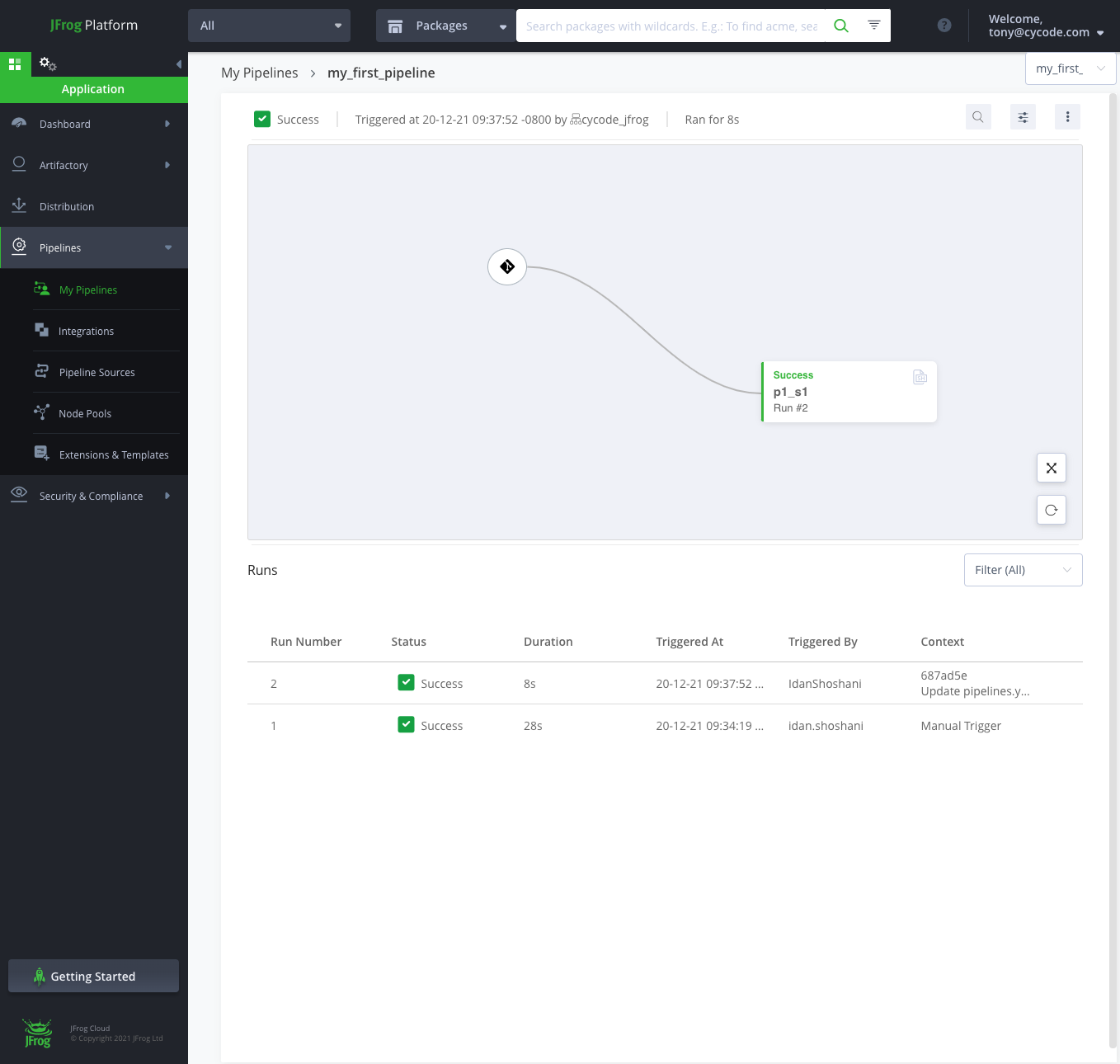
These hardcoded secrets may be viewed within the Violations section of the Cycode platform:
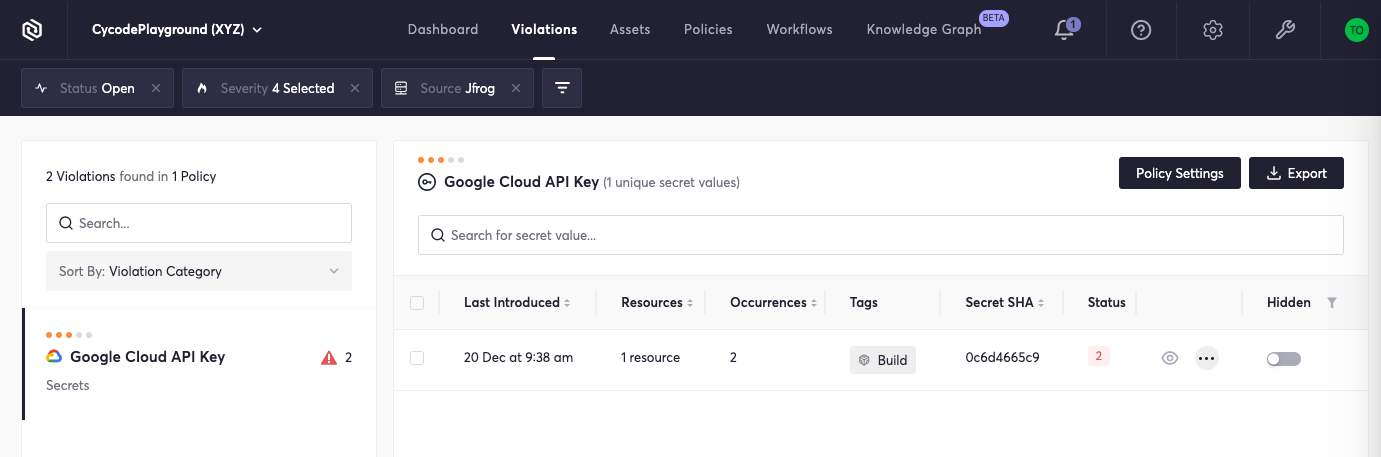
This view shows the secret in question and reveals details regarding the infraction. Clicking into this section reveals more details:

This view allows us to pinpoint exactly where each violation occurs and when our developers unintentionally introduced the secrets. Even in blameless cultures, this helps educate developers on best practices to help avoid future violations.
How to Integrate Jfrog into Cycode
The Cycode integration is relatively straightforward to set up. Only two parameters are required: the server URL and the admin access token.
- The server URL is the JFrog instance account URL.
- The admin access token is a flexible means of authentication with a wide range of capabilities. More information regarding token structure and usage may be found in the Identity and Access documentation. To create an admin token, start from the administration module, go to Identity and Access, navigate to the Access Tokens screen, and go to the Generate Admin Token section:
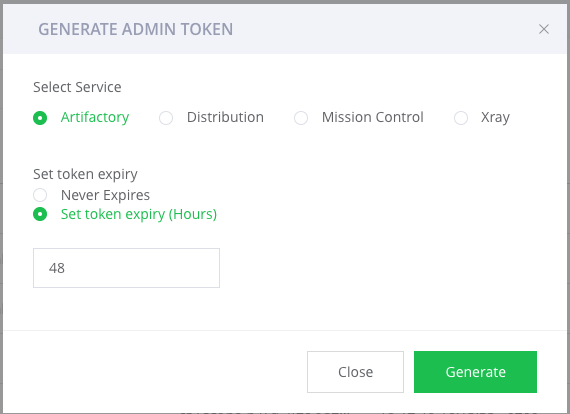 f
f - Now that we have generated the token, the integration can be completed on the JFrog platform. To view integrations, navigate to the Integrations under Pipelines:
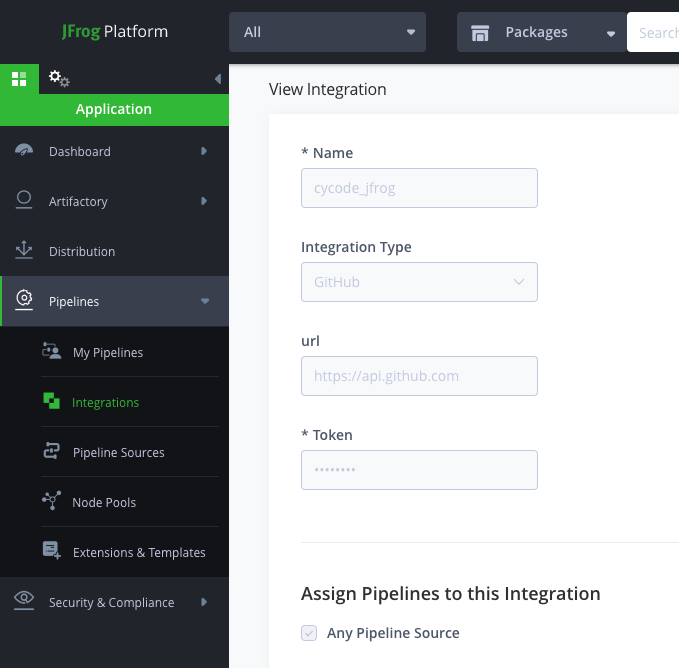
- Adding in the integration type and the URL finishes the configuration; we use Github within this sample interaction as this would help organizations adhere to best security practices for Github. The section below allows for users to assign specific pipelines to this integration.
And that’s it! The JFrog integration with Cycode is easy to set up; once set up, the integration scans all future build workflows for vulnerabilities. The setup time required to enable the insights provided is time well spent. Let’s take a look at the main benefits.
Key Benefits of the Cycode Integration
-
Allows for insights to be drawn from multiple sources to create a holistic view
One of the key features of the knowledge graph is its capability to aggregate data from different sources to provide unique insights. The information that can be conveyed through this aggregation of data is greater than the sum of its parts in that the insights generated can only be constructed by combining the data from multiple sources. These insights could theoretically be drawn by way of manual scans, but this would take exponentially longer than Cycode’s knowledge graph and would have enormous costs in terms of developer productivity.
-
Easily scan code, artifacts, and the CI/CD pipeline for secrets, misconfigurations, and leaks
The risk of hardcoded secrets stems from three sources: compromised insiders, malicious insiders, and code leakage. A complete hard-coded secrets solution must include comprehensive scanning and address the ways secrets are exposed, which Cycode delivers on. The consistent governance provided helps eliminate misconfigurations like publicly accessible artifacts, critical data that is not encrypted at rest, weak password policies, and non-rotated encryption keys.
-
Artifacts may be scanned within the developer workflow
At each point in the CI/CD pipeline, artifacts may be produced which can introduce vulnerabilities if misconfigured. Cycode helps developers break the habit of hardcoding secrets by integrating secret scanning directly into developer workflows via pre-commit and merge request scanning. In addition, Cycode’s automated remediate capabilities help fix the specific misconfigurations detected in JFrog Pipelines and beyond.
Next Steps for Enhancing Functionality of the Cycode Integration
This partnership between JFrog and Cycode enables a level of enhanced visibility that allows organizations to have increased visibility into the security of their code, artifacts, and pipelines. The idea of “connecting the dots” describes the end goal for the integrations as it is meant to enhance both governance and visibility of a pipeline.
Let’s take an example where a pipeline execution creates a build artifact that is in turn deployed by Kubernetes. Customers will be able to see a flow similar to the following:
Commit to a repo –> Triggered build workflow –> Build uploaded artifact to Artifactory –> pulled by Kubernetes –> running on a pod on a machine.
This query will verify that pipelines create and maintain key artifacts by returning values matching the parameters. This verification helps ensure the provenance of the build and deployment, and also serves to provide a barricade against code tampering. The inverse of this query can be used to identify suspicious deployments much faster than a manual check would uncover this. Adding functionality to represent these connections visually is coming soon.
Conclusion
Cycode’s mission with this integration is to help provide security visibility into DevOps pipelines, which will maintain an inventory of assets residing in JFrog Artifactory and Pipelines. Cycode scans each component for various potential exploits, which improves pipeline visibility, which can help uncover weaknesses such as the log4j vulnerability, and orchestrates application security across the SDLC.
Originally published: December 31, 2021