Cycode has created an integration allowing Terraform Cloud configuration drift detection between deployment environments. This helps improve governance, eliminate sources of potential vulnerabilities, and ensures that developer time is not wasted debugging IaC misconfiguration.
Terraform is a leading infrastructure-as-code (IaC) tool that allows declarative syntax to provision, deploy, and scale cloud resources. First unveiled in 2015, this tool has grown to be one of the most prolific in its space; according to HashiCorp’s State of Cloud Strategy Survey, the most popular cloud operating model tools are Terraform and Kubernetes, with 25% and 18% of respondents using each respectively.

Terraform may be used on Terraform Cloud, Hashicorp’s managed service for using Terraform in production. Terraform Cloud enables infrastructure automation for provisioning, compliance, and management of any cloud, data center, and service. This capability allows for functionality such as remote Terraform execution, version control integration, and other advantageous functionality for IaC over traditional infrastructure. This SaaS offering Terraform Cloud eliminates the need for organizations to host and manage infrastructure and improves a team’s ability to manage projects.
One of the main benefits of using IaC tools such as Terraform to manage and facilitate configuration changes between deployment environments is that this tool is much faster and less accident-prone than prior technologies. However, IaC is far from foolproof as users can still make changes to an environment directly.
For example, if production configurations are changed on a provisioning system via UI or a CLI interface, these changes may introduce configuration drift. In IaC, this drift occurs whenever a mismatch exists between the actual runtime configuration and predetermined build-time states.
Terraform Cloud Drift Detection With Cycode Integration
Cycode’s integration with Terraform unlocks new possibilities. The purpose of the integration is to provide alerts to developers that configuration drift has been detected between declarative IaC code and cloud deployment environments. In addition, this integration offers a straightforward way to remediate drift that is significantly faster and easier than previously defined means of reconciling the desired Terraform configuration with a real-world state.
About Configuration Drift
Configuration drift is not a new problem. When IT personnel manually configured physical servers in the days before cloud resources, configuration drift occurred because of the lack of visibility into configurations between environments.
IaC has made it possible to standardize configurations between deployment environments, but this has not eliminated the problem of configuration drift. For example, configuration drift can happen if an operator changes a deployment environment by way of a console without making the change across all deployment environments. Without checks to ensure that changes made do not break the necessary synchronization between environments, configuration drift can occur just as it did with bare metal servers.
Without additional tools, Terraform drift detection has shortcomings; Terraform cannot detect the drift of resources and does not manage associated attributes. If configuration drift is introduced, the technology intended to reduce error instead amplifies misconfigurations as it performs the core task of provisioning resources. The key to eliminating configuration drift is visibility–if developers can quickly check and audit infrastructure as code environments, the relevant engineers can reconcile mistakes before negatively affecting deployments.
How this Terraform Cloud Drift Detection Integration Works
The core of Cycode’s product is its knowledge graph technology. This tool aggregates data from DevOps tools, infrastructure, and security scanners to generate security insights and help provide meaningful insight to security teams. The most significant benefit to the insights drawn from this tool is that it breaks down silos of data to generate complex insights. In the words of Cobalt’s CISO:
“Cycode has saved us a massive number of hours hardening our source control management system, enforcing security configurations, and preventing secrets from entering our code. Plus, by plugging seamlessly into our developers’ workflows, our team adopted Cycode right away.”
The Terraform integration checks assets into Cycode’s knowledge graph, allowing Terraform resources to be scanned for misconfigurations and increasing the value of Cycode’s security alerts. Once the integration is implemented between an organization’s Terraform environment and Cycode tenant, instances of configuration drift can generate alerts.
For example, let’s assume configuration drift occurred between a Terraform test environment and the deployment environment. The alert for such a scenario would be viewable within the Cycode platform:
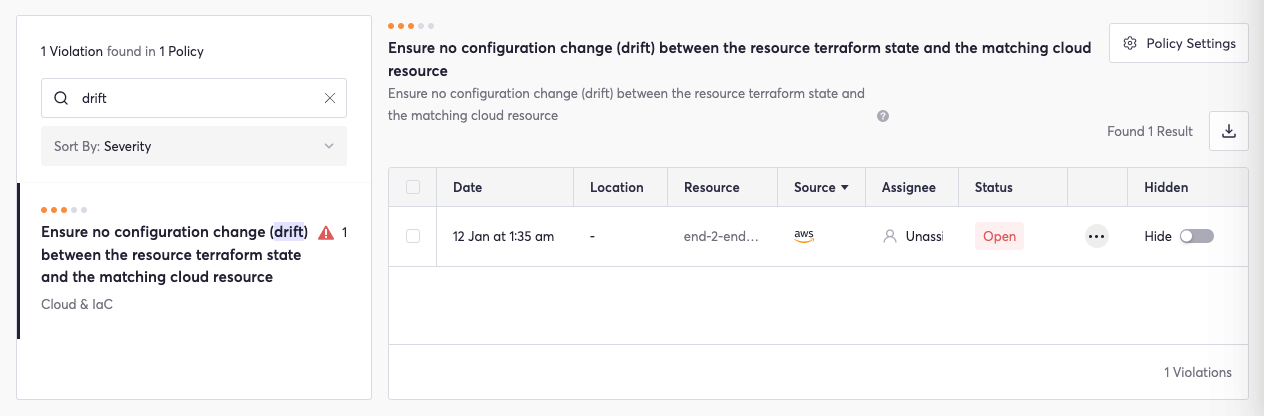 This disparity between the IaC configurations triggers a Cycode alert that is meant to be visible, thus helping improve security. Further inspection of the violation alert would reveal the specific disparity between the code and cloud resources triggering the alert:
This disparity between the IaC configurations triggers a Cycode alert that is meant to be visible, thus helping improve security. Further inspection of the violation alert would reveal the specific disparity between the code and cloud resources triggering the alert:
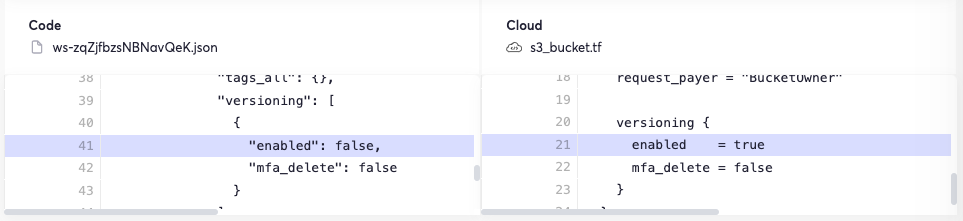 In addition to this platform alert, the integration can create warnings to developers that call attention to state changes in deployment environments that may result in mismatching settings.
In addition to this platform alert, the integration can create warnings to developers that call attention to state changes in deployment environments that may result in mismatching settings.
How to Integrate Terraform Cloud Into Cycode
Integrating Terraform into Cycode is a straightforward process. Cycode offers this integration directly, with minimal configurations that organizations can set in minutes. This integration may be performed on an existing workspace or on a new workspace.
To configure the integration within Cycode, navigate to Settings and ensure you land on the Integrations page. Then, under the Cloud & Infrastructure section, select Terraform Cloud:

Now, select the add integration button. Clicking this button will direct you to the following page:
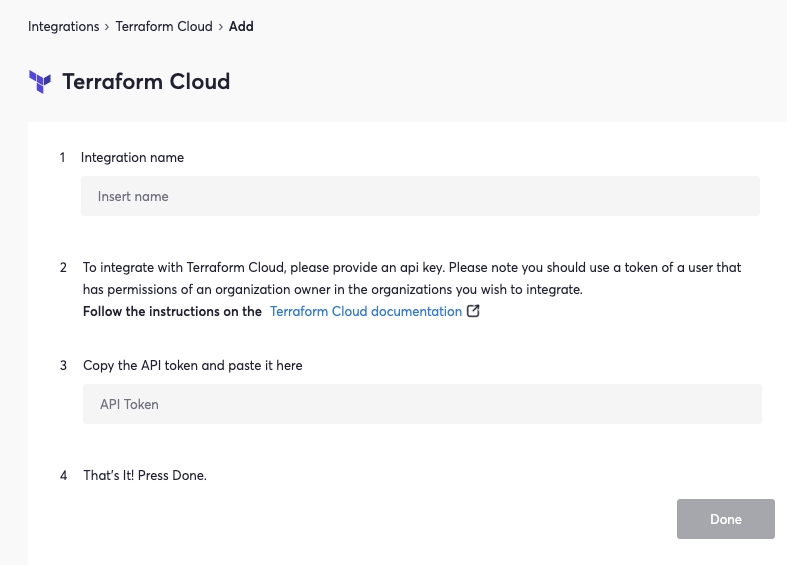
On this page, users can add the required pieces to complete the integration: the integration name and the API token. This API token needs to be associated with a user who has owner permissions for the organization you wish to integrate.
Critical Benefits Of the Cycode Integration
There are many benefits to integrations, particularly integrations that allow data to be analyzed or provide enhanced security visibility. The main advantages of integrating Terraform Cloud into Cycode include:
-
Detect and remediate configuration drift within the developer workflow
There are several benefits to pushing alerts to developers through pre-commit messages or within developer workflows. First and foremost, this form of alert integration presents the results to the developer responsible for maintaining the code in question; this allows the developer to fix potential bugs without wasting time refreshing themselves on the context of the issue.
In addition, implementing Terraform drift detection within the developer workflow allows for automatic remediation of IaC misconfigurations. Fixing mistakes within the PR workflow helps keep an organization’s developers focused on delivering high-quality code while also maintaining infrastructure that adheres to best practices.
-
Audit Terraform cloud resources within the Knowledge Graph
Cycode’s Knowledge Graph maps out assets in an organization’s software development ecosystem. The real value of this tool emerges when performing queries that require inputs from multiple stages of a deployment pipeline; the tool delivers complex insights that are only possible by breaking down data silos of the SDLC.
The knowledge graph provides an easy means of verifying that inputs and outputs match across all the interconnections within the software delivery pipeline. In the context of IaC, checking the handshakes between stages enables the identification of IaC configuration drift since such a scenario would entail a mismatch between the IaC configuration and actual production settings.
-
Enhanced matching between cloud resources and code resources
Certain IaC frameworks, including Terraform and AWS CloudFormation, utilize declarative syntax, meaning that the desired configuration is described directly in code. Implementing checks to ensure that IaC-declared resources match provisioned cloud resources checks that IaC code is written and deployed properly.
-
Enforce Terraform Cloud best practices using the Knowledge Graph
Developers already have enough work on their plate. This Terraform integration helps developers adhere to best practices for Terraform development while minimizing the time investment required to scan and remediate security issues.
Conclusion
Cycode’s mission with this integration is to help provide visibility into Terraform Cloud configurations. Catching these misconfigurations helps reduce the chance of introducing vulnerabilities and ensures the accurate deployment of IaC resources. The Cycode integration discussed above introduces Terraform drift detection to IaC security tools and advances the state of application security.
Cycode helps establish strong governance over every point of the IaC lifecycle by creating an inventory of all users, contributors, teams, organizations, and repositories in your organization; this governance extends into providing more oversight into changes made to code as a means of further protecting key code. Cycode also helps you automatically audit access privileges to identify and reduce excessive, unused privileges and implement separation of duties. These improvements help apply security best practices for IaC code when using Terraform, Kubernetes, and CloudFormation.
Want To Learn More?
A great place to start is with a free assessment of the security of your DevOps pipeline.
Originally published: January 24, 2022