Get a Personal Demo
Enterprise
Software Composition Analysis
Designed for Devs.
Cycode’s modern, enterprise Software Composition Analysis (SCA) is the most advanced way for security and dev teams to scan, prioritize, and remediate application code for vulnerable open source dependencies.
{ scan }
Continuously Perform
SCA Scans for Vulnerable
Open Source Dependencies
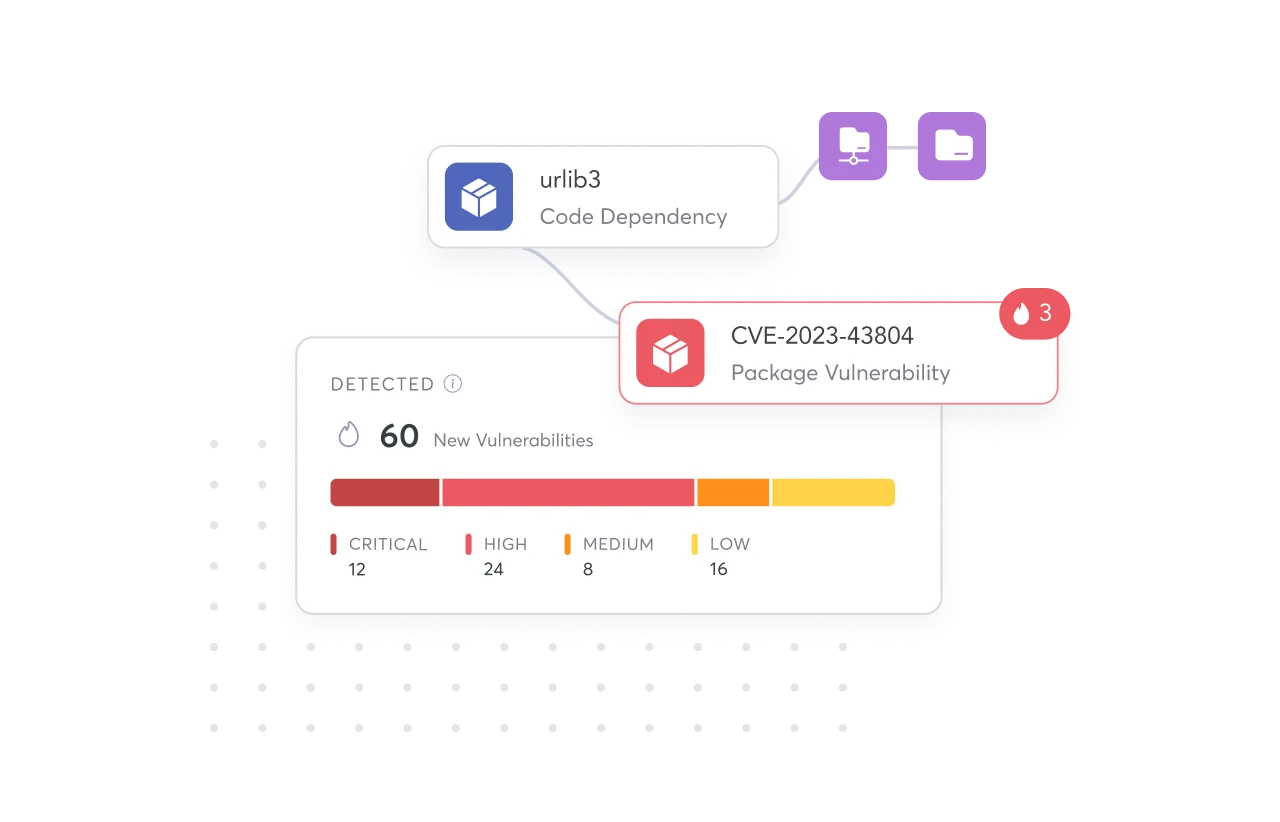
Automatically monitor your code and build modules for vulnerabilities or license violations before it goes into production using continuous software composition analysis.
Code Dependency Scanning
Pipeline Dependency Scanning
License Risk Identification
{ Prioritize }
Stay Focused on the Open Source SCA Risks That Matter Most
With enterprise SCA tools from Cycode, you can prioritize vulnerabilities that may lead to the biggest impact on the business — all while tracing back to its root cause, code owner, and path into production.
Risk Scoring
Reachability Analysis
Code to Cloud Traceability
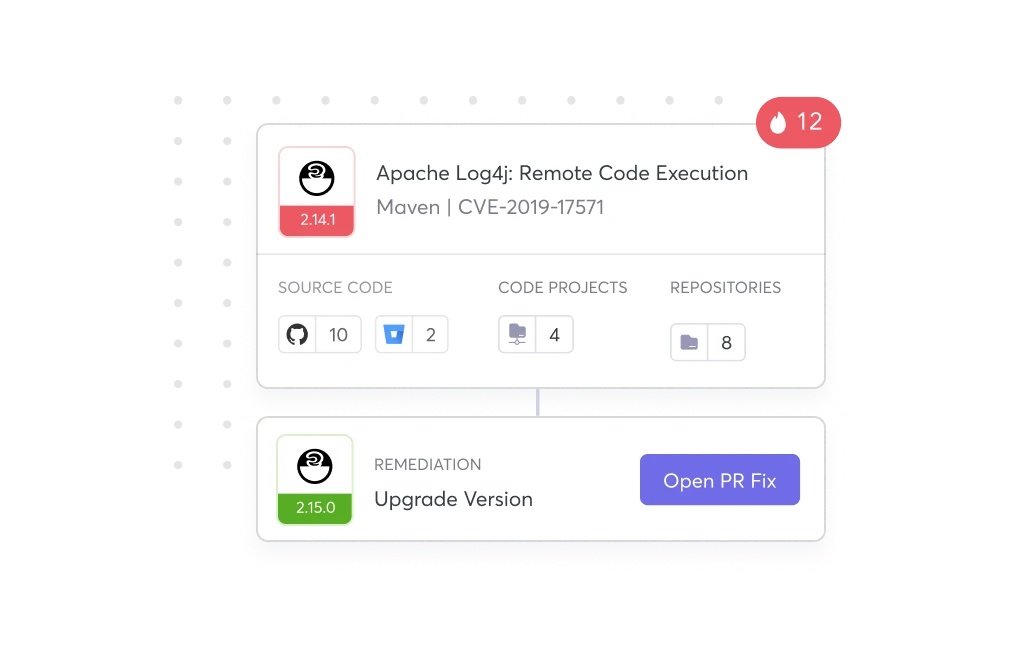

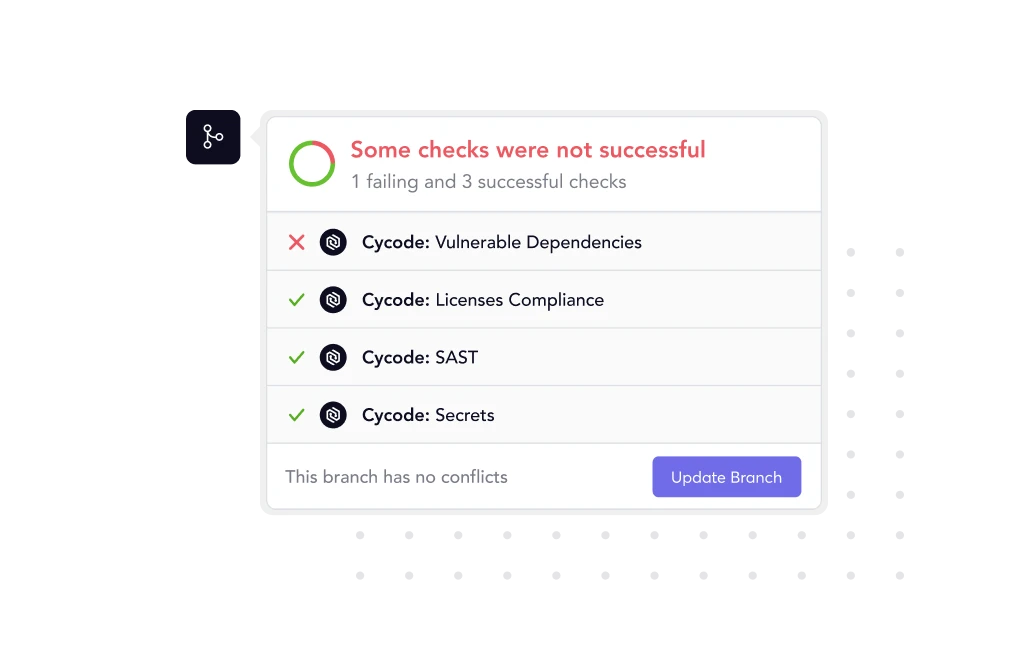
{ Remediate }
Ship Code Faster with
Developer-Friendly SCA Security Software
Automate open source vulnerability fixes in one click with software composition analysis that provides all the context, upgrades, and patches for your development team right within their Workflows via PR scan, CLI, or IDE.
Remediation Context
Issue Tracking Integrations
Bulk Remediation

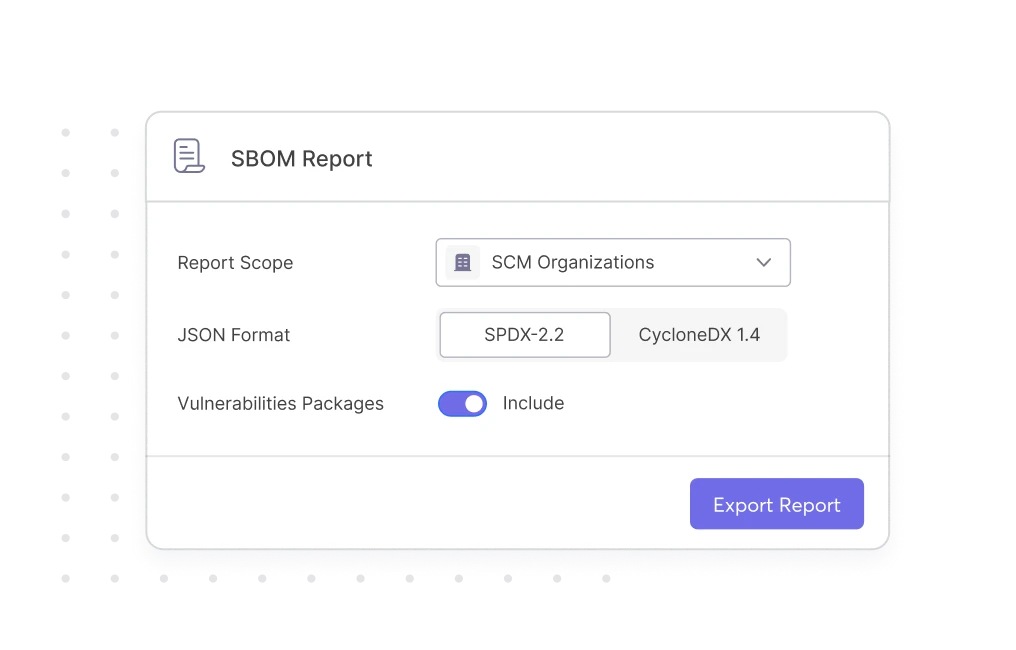
Auto-Generate
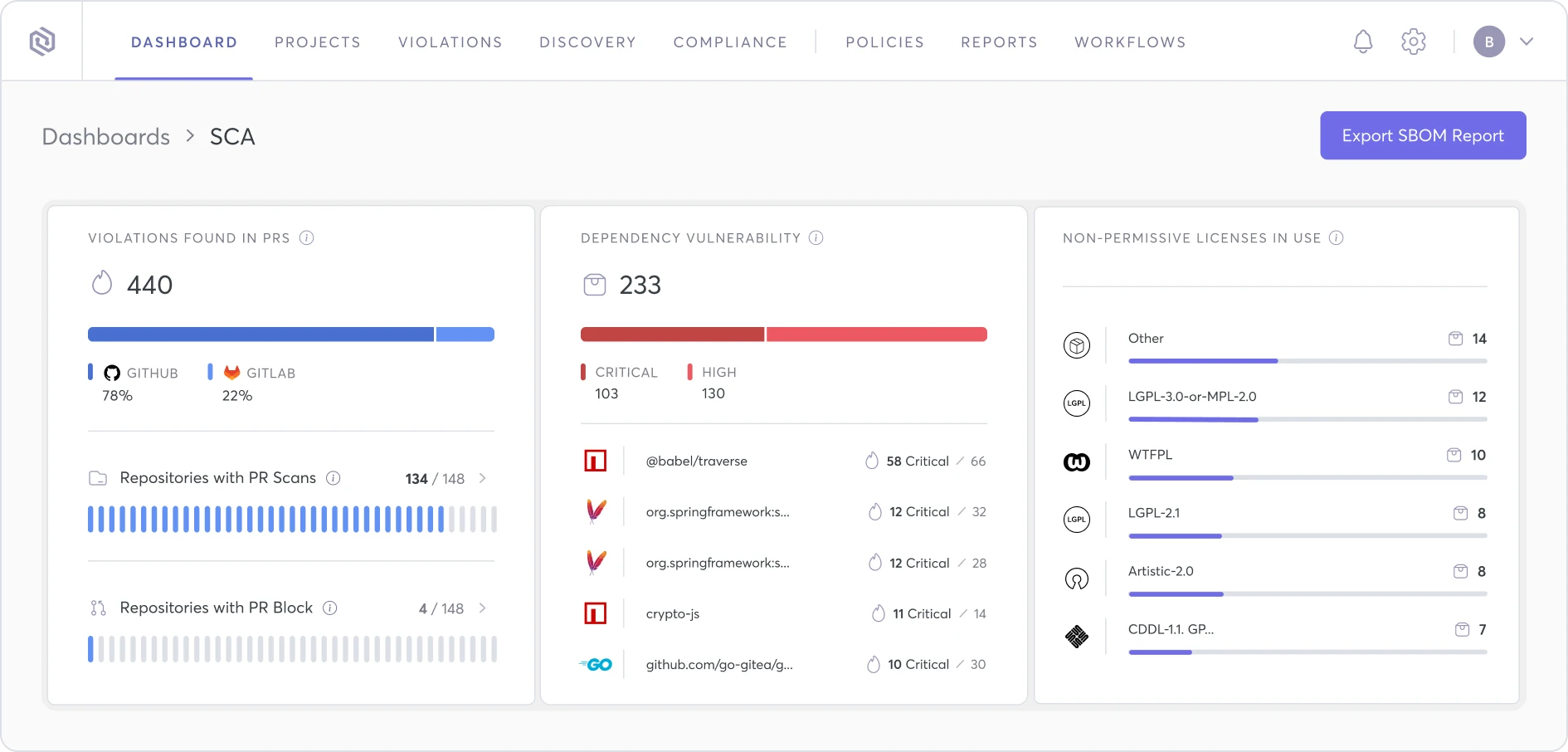
SCA SBOMs in Seconds
Using the Cycode SCA scanner, you always maintain an up-to-date software bill of materials (SBOM), and keep up with the speed of DevOps — where your components and their versions are always changing.

Choose your organizations & assets

Generate in SPDX or CycloneDX format
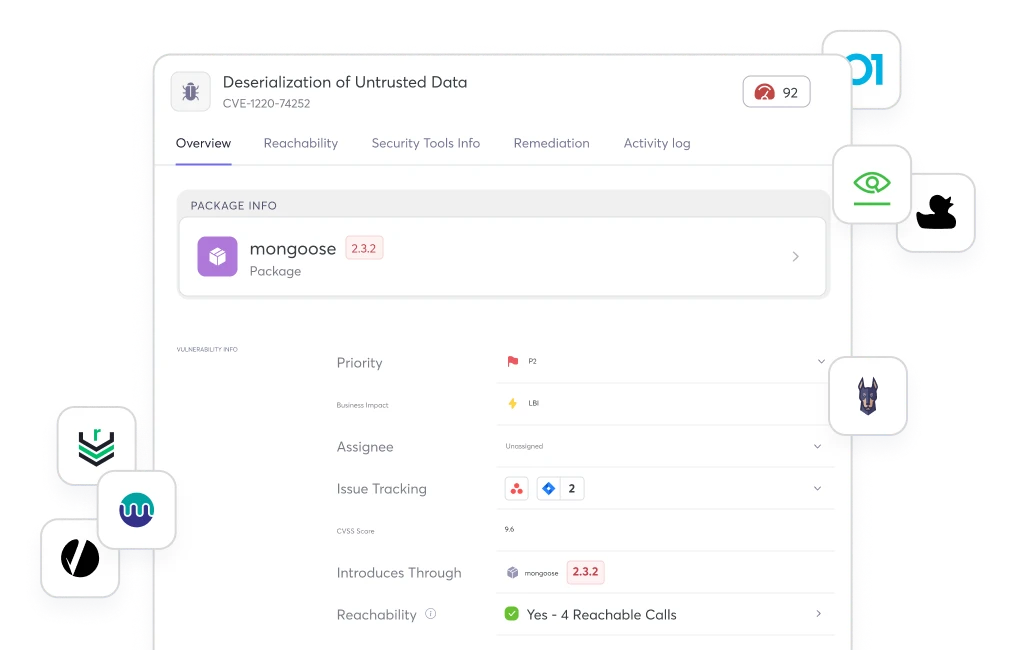
Complete Visibility
into All Your
Open Source Vulnerabilities
Select and connect your open source vulnerabilities and code scanning software of choice with the Cycode ASPM — all while getting the visibility, prioritization, and remediation that your organization needs to help standardize your AppSec program at scale.
Frequently Asked Questions
What Is Software Composition Analysis?
By understanding these aspects of code, developers can build more secure and reliable software.
How Do CISOs, Compliance Teams, and Security Managers Use SCA Security Software?
Here is how they use SCA software:
- Vulnerability Detection and Prioritization: SCA software automatically scans and analyzes open source and third-party libraries for known security vulnerabilities and license issues. It helps security managers identify vulnerabilities in both direct and transitive dependencies. The software then prioritizes these issues based on context like reachability and exploitability, allowing teams to focus on the highest-risk vulnerabilities that could have the biggest business impact.
- Ensuring Compliance: Compliance teams use SCA software to ensure that all open-source components are used in accordance with their licenses, helping to prevent legal risks. The software can also automatically generate a complete Software Bill of Materials (SBOM) in formats like SPDX or CycloneDX, which is essential for demonstrating due diligence and meeting regulatory requirements.
- Risk Management: For CISOs, SCA software provides essential visibility into the software supply chain. It helps to catch and fix risks early, before code reaches production, thereby reducing remediation time and enhancing the overall security posture. By providing insights into dependencies and version management, the SCA software helps in making informed decisions and effectively managing technical debt.
Why Is SCA Scanning a Critical Part of the SDLC?
SCA enables teams to catch and fix these risks early, before code reaches production. When enabled, it can:
- Detect vulnerabilities in direct and transitive dependencies
- Catch license violations before they become legal risks
- Prioritize issues with context like reachability and fixability
- Reduce remediation time by surfacing issues in developer workflows
- Enforce policies across code, builds, and pipelines
SCA Software vs. Traditional Vulnerability Scanners: What Are the Differences?
- SCA Software: This is designed to specifically scan and manage risks related to open-source components and third-party libraries within your application's code. It identifies known vulnerabilities (CVEs) and license compliance issues in these dependencies.
- Traditional Vulnerability Scanners (Network & Infrastructure): These tools scan the broader IT environment from the outside, like an attacker would. They look for vulnerabilities in networks, servers, and other hosts, such as misconfigurations, unpatched software, and open ports. They do not analyze the application's code itself.
- Static Application Security Testing (SAST): SAST is another type of vulnerability scanner that is often part of a comprehensive security program. Unlike SCA, SAST tools analyze your proprietary source code to find coding flaws like SQL injection or cross-site scripting (XSS) before the application is even run.
What Are the Risks of Using Open Source Components?
- Open source projects often suffer from inconsistent maintenance, resulting in delayed security patches and updates
- Vulnerabilities are publicly disclosed and, therefore, easy to exploit
- Attackers can use one vulnerability to exploit a number of companies — as many as are using that particular library or component
- Vulnerable components can be used to execute software supply chain attacks
How Does Software Composition Security Analysis Work?
- Component Identification: Software composition analysis tools scan software projects to inventory all components using manifest scanning and binary scanning.
- License Compliance: Open-source SCA security software assesses licenses of identified components to ensure compliance and avoid legal issues.
- Vulnerability Detection: SCA software cross-references components against vulnerability databases to identify known vulnerabilities and assess their severity through tools like risk scoring
- Prioritization and Remediation: Top SCA tools prioritize vulnerabilities based on reachability and exploitability, offering remediation advice and integrating with issue-tracking systems to streamline the process.
What Are the Benefits of Using a Software Composition Analysis Tool?
Other benefits of SCA software include:
Enhanced Security Posture: SCA code scanning enables organizations to proactively identify and address vulnerabilities in their software supply chains, preventing costly security breaches and safeguarding sensitive data.
Regulatory Compliance: Software composition analysis and security ensures compliance with regulations like GDPR, HIPAA, and PCI DSS by tracking third-party components, verifying licensing, and demonstrating due diligence in data protection, facilitated by accurate SBOMs.
Assured Quality and Reliability: SCA upholds trust by ensuring software quality and reliability, thereby protecting sensitive customer data and delivering seamless user experiences.
Streamlined Development Processes: Code scanning software automates dependency management, integrates with developer workflows, and enhances productivity, accelerating time-to-market while balancing speed, innovation, and security.
Empowerment Through Insights: An SCA scan provides insights for informed decision-making on dependencies, version management, and vulnerability remediation, empowering developers to mitigate technical debt and foster continuous improvement.
How Can Enterprise Software Composition Analysis Tools Impact DevSecOps?
- Move faster with less risk. By integrating continuous scanning into the pipeline, SCA tools catch and remediate open-source vulnerabilities early, preventing costly issues from reaching production.
- Empower developers. Tools provide developers with the context needed to quickly fix issues without leaving their workflow, using features like automated fixes and risk-based prioritization to reduce noise.
- Secure the supply chain. SCA ensures a complete and up-to-date Software Bill of Materials (SBOM) and provides continuous visibility into open-source dependencies, which is crucial for compliance and risk management.
Why Do Enterprises Rely on SCA Software for Compliance and Risk Management?
- Proactively manage risk by identifying and prioritizing vulnerabilities based on real-world impact, allowing teams to address the most critical threats first.
- Ensure legal compliance by continuously scanning for and flagging open-source license violations before they become costly legal issues.
- Establish a single source of truth with an up-to-date Software Bill of Materials (SBOM), which is essential for audit trails, security management, and providing complete visibility into their software supply chain.
How Do I Choose the Best SCA Tools for My Organization?
What to look for:
- Accurate detection of direct and transitive dependencies
- AI-powered risk-based prioritization
- Seamless integration into dev tools and pipelines
- License compliance and policy enforcement
- Scans across code, builds, containers, and cloud
- Consolidation with other AppSec tools to reduce sprawl
Check out Cycode’s SCA Buyer’s Guide for a more detailed breakdown of features, questions to ask, and how to evaluate the top-rated SCA tools for software supply chains.

 Solution Brief
Solution Brief