Get a Personal Demo
Comprehensive IaC Security for Security
and Development Teams.
Prevent cloud misconfigurations and apply IaC security standards to
Kubernetes, Terraform, CloudFormation, ARM & more.
{ drift protection }
IaC Security Tools that Monitor and Keep Tabs
On Any Configuration Drift
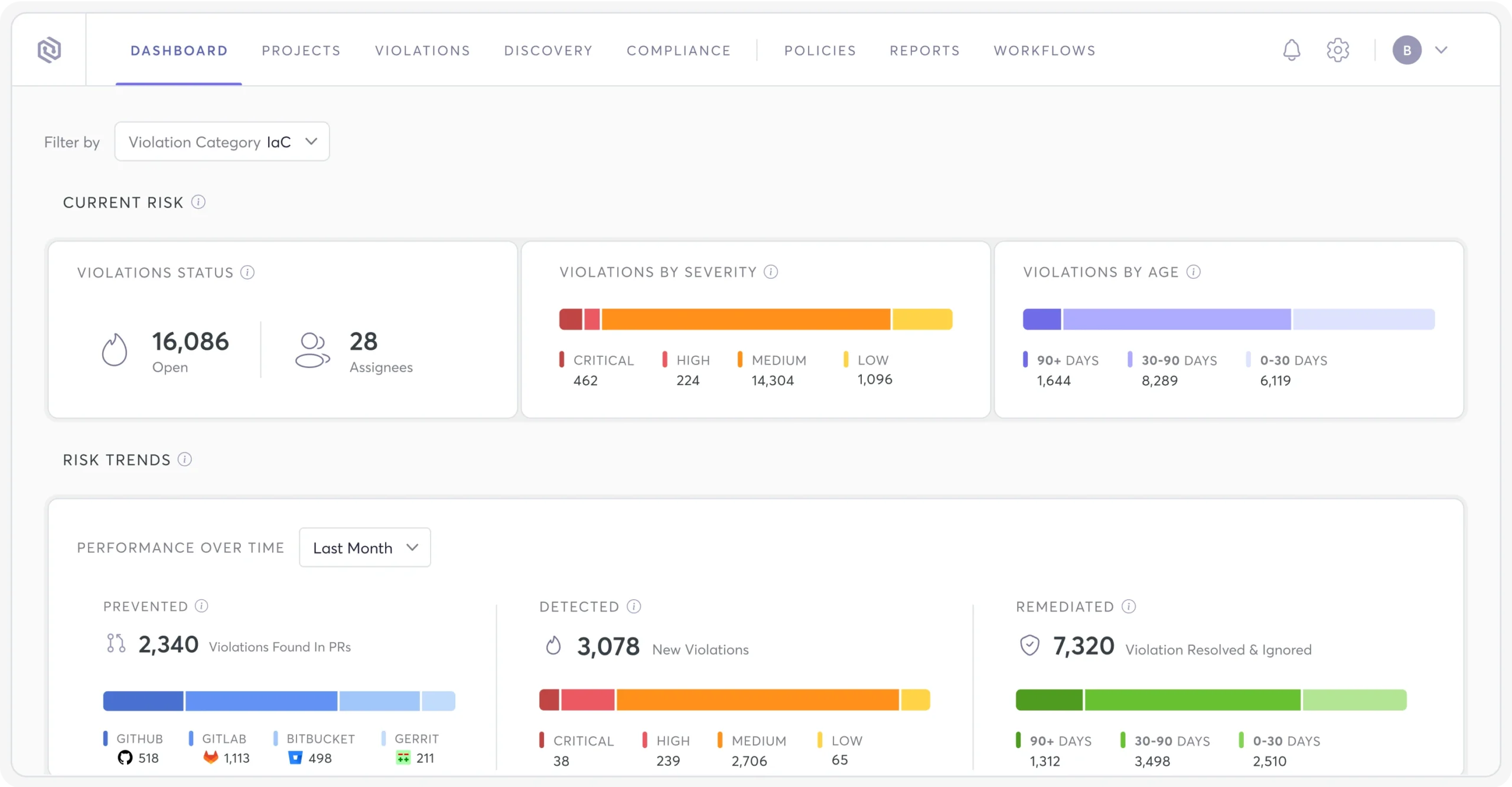
Continuously compare IaC configurations with those in production so you can identify drift. Find situations where configurations are no longer aligned and are operating in an insecure way. Alert the right teams so these environments can be fixed.
Automated IaC security scanning
Alert your team on any misconfigurations
{ visibility }
Identify All Your
Cloud Environment Misconfigurations
Let your devs easily find and fix IaC security misconfigurations through Cycode’s continuous scanning. Uncover alerts for your team across hundreds of misconfiguration types such as publicly accessible storage buckets, non-encrypted critical data, weak password policies, non-rotated encryption keys, and more.
Continuous infrastructure as code scanning for every change
Customizable detection logic for IaC security risks

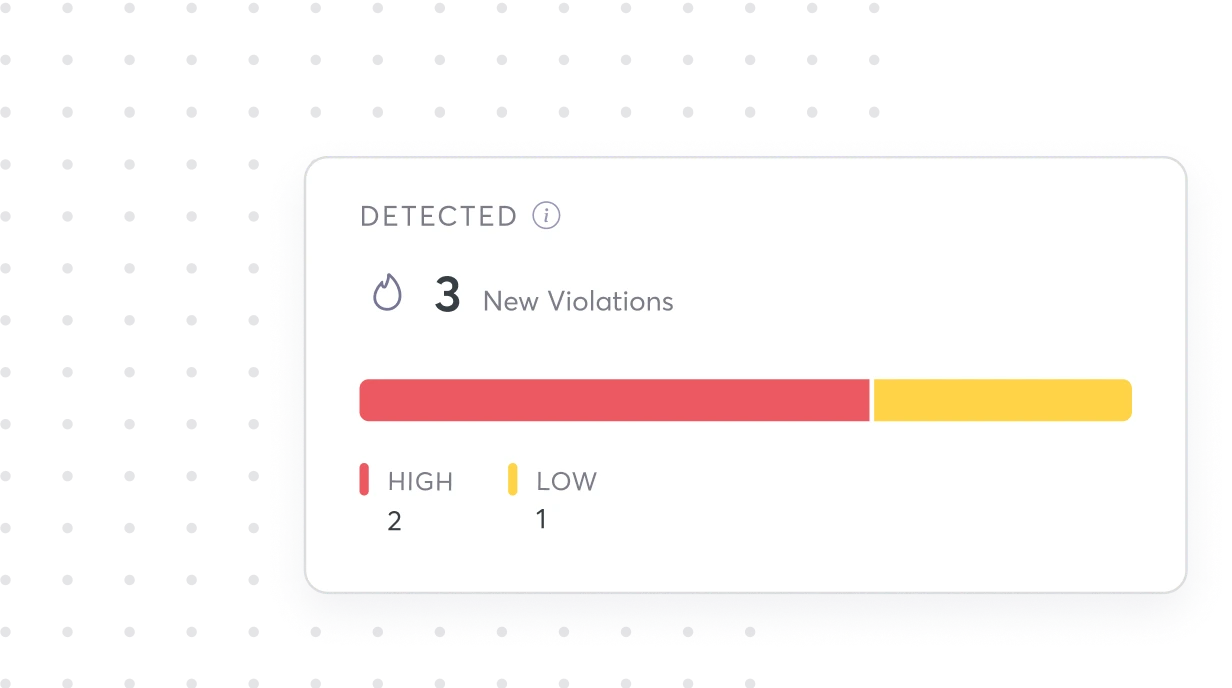
{ Prioritization }
Focus on the
Misconfigs that Matter Most
Prioritize your riskiest misconfigs with IaC security testing that helps ensure nothing slips through the cracks and impacts the business.
Risk scoring engine
Impact & exposure level prioritization

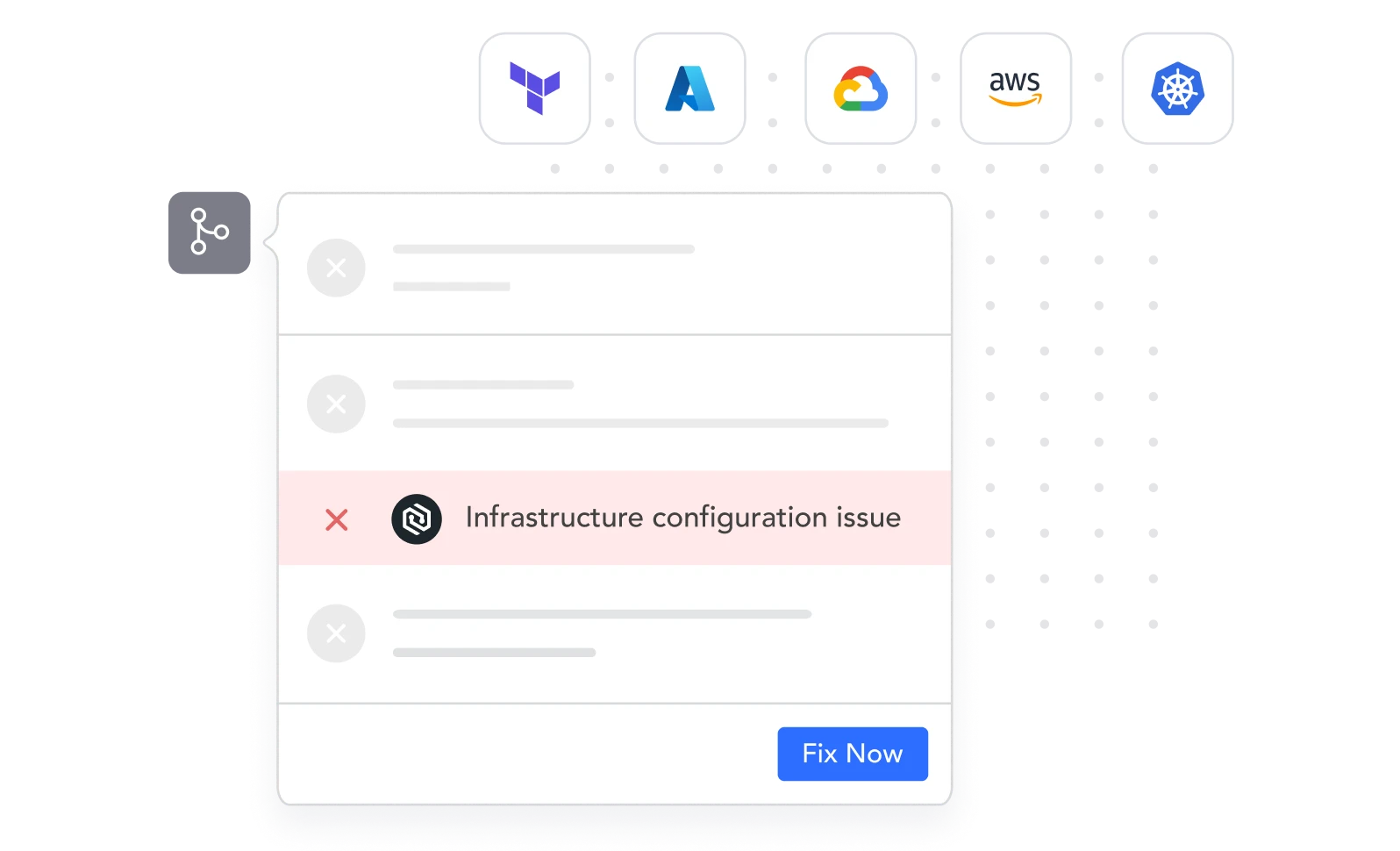
{ Developer Friendly }
Free Flowing IaC Scanning
within Developer Workflows
Scan new commits and merge requests for misconfigurations in compliance with NIST, CIS, or any custom built rules. If scans return IaC policy violations, Cycode automatically presents the results to developers and the code fix needed to remedy the issue.
Automated PR fixes
Self-serve development workflows
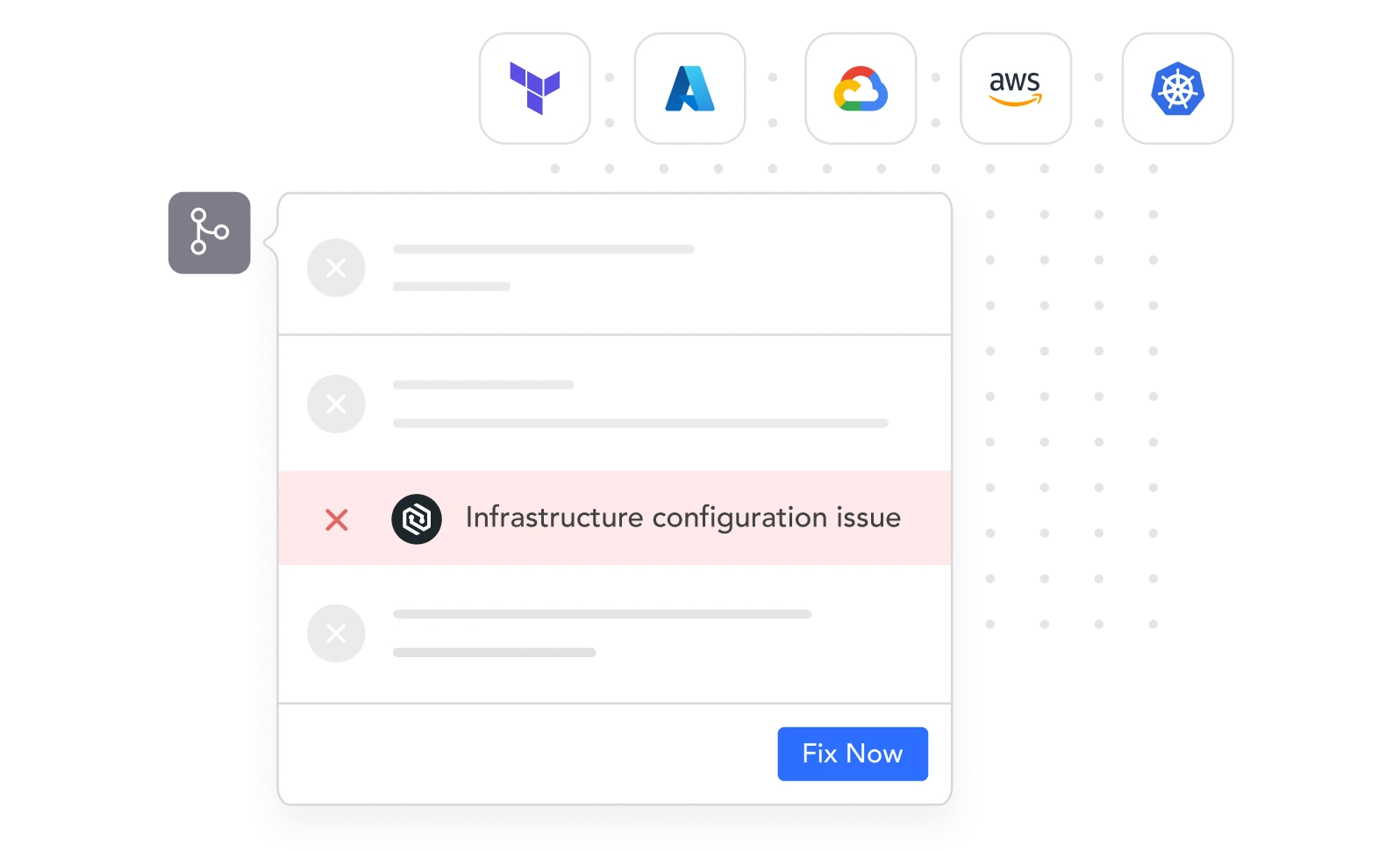
{ Remediation }
Automate Fixes with
All the Context You Need
Automatically open pull requests with the code fix needed to remediate the specific misconfigurations detected in your IaC security. This keeps your developers focused on efficiency and your infrastructure in line with best practices.
Auto-resolve remediated vulnerabilities
Remediation context and guidelines right within your developers IDE
Connect into the CI/CD workflow with Cycode CLI
Detect, block, and monitor vulnerabilities in the PR
Streamline remediation workflows through ticketing tool integrations
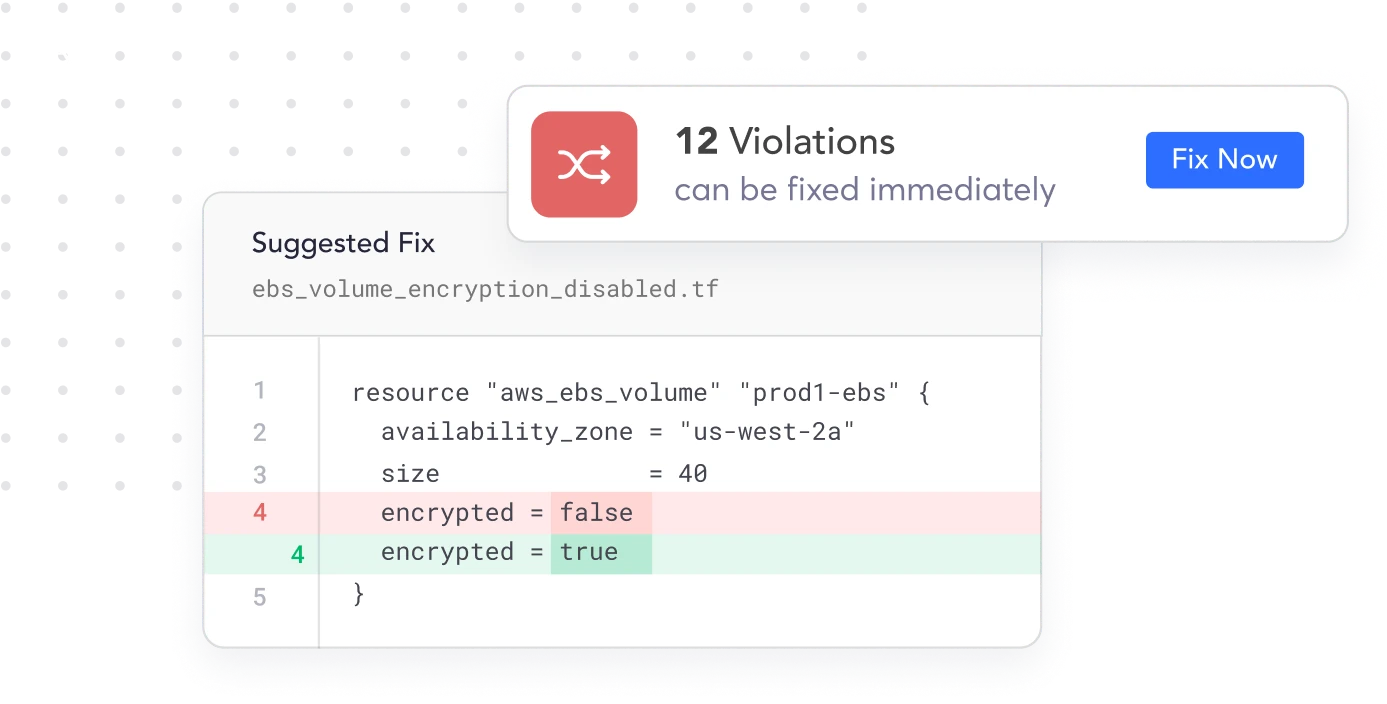

Reduce IaC Security Risks with Enterprise-Grade Protection that Scales
Cycode is built for the complexity of modern enterprises, offering IaC scanning tools that effortlessly scan IaC across all your environments. This scalable approach ensures comprehensive protection for your evolving cloud infrastructure without compromising performance or accuracy.
Rapid Integration
Deploy and integrate Cycode seamlessly into existing CI/CD pipelines within minutes, providing instantaneous feedback at every commit.
High Performance
Maintain fast development cycles with high-speed scans that scale to manage hundreds of thousands of infrastructure resources daily.
Unified View
Gain a single, consolidated dashboard to manage security policies and risks across all IaC repositories, unifying security efforts at an enterprise level.
Frequently Asked Questions About Enterprise IaC Security
What Is IaC Security?
Cycode provides comprehensive IaC security, unifying scanning, prioritization, and remediation to secure configuration files across the entire development lifecycle. This ensures you can scale your cloud infrastructure securely without introducing risk.
Why Is Infrastructure as Code Security Important?
Misconfigurations in IaC security can lead to:
- Security breaches
- Compliance failures
- Operational disruptions
What Are the Benefits of IaC Security?
- Early risk detection: Catches misconfigurations before deployment.
- Automated compliance: Enforces security policies within development pipelines.
- Faster remediation: Fixes vulnerabilities in code before they reach production.
- Scalability: Ensures security across cloud and production environments as they evolve.
- Efficiency: Reduces manual security reviews through automation.
What Is IaC Security Scanning?
How Do I Choose the Right IaC Security Scanning Tools for My Enterprise?
-
Unified Platform and Context
- ASPM Integration: Choose a platform that unifies IaC scanning with other security findings (SAST, SCA, Secrets). The solution should be part of a complete Application Security Posture Management (ASPM) platform, not a point solution.
- Code-to-Cloud Traceability: The tool must use a Risk Intelligence Graph to correlate misconfigurations in the IaC file with the actual running cloud environment. This is essential for accurate, risk-based prioritization
-
Priority and Remediation at Scale
- Contextual Prioritization: The tool must move beyond simple severity scores to prioritize findings based on real-world business risk (e.g., is the vulnerable resource exposed to the internet?).
- Developer-First Workflows: Look for deep integration into developer tools (IDE, PRs, CI/CD) that provides fast feedback and offers automated remediation or code fixes directly within the workflow to ensure high velocity.
-
Compliance and Governance
- Broad IaC Support: Ensure the tool supports all your frameworks (Terraform, Kubernetes, CloudFormation) and can enforce your security and compliance policies (e.g., CIS Benchmarks, SOC 2) as code across your organization.
How Does Cycode’s Enterprise Infrastructure as Code Security Work?
- Automated scanning: Identifies misconfigurations in IaC files.
- Policy enforcement: Ensures compliance with security standards (CIS, NIST, etc.).
- Secret detection: Prevents credential leaks in code.
- Drift detection: Monitors infrastructure for unauthorized changes.
- Remediation automation: Fixes issues before deployment without manual effort.
How Does Enterprise IaC Security Fit into an AppSec Strategy?
The three primary ways IaC security integrates into a broader AppSec strategy are:
- Enabling Shift Left Security: IaC security is the purest form of shift left security. By utilizing automated IaC scanners early in the development process (e.g., within the developer’s IDE or on every Git pull request), security teams catch misconfigurations and vulnerabilities before they are provisioned into the actual cloud infrastructure. This drastically reduces the cost and effort of remediation.
- Governing the Software Supply Chain: It provides a critical control point across the entire supply chain. Implementing a robust IaC security framework ensures all infrastructure configurations—whether Terraform, Kubernetes, or CloudFormation—adhere to corporate policy and compliance standards (like CIS or PCI DSS) from the moment the code is written
- Providing Risk Context: IaC security data is fed into a central Application Security Posture Management (ASPM) platform to provide Code-to-Cloud traceability. This context is vital for prioritization, allowing security teams to understand which IaC risks translate to actual, exploitable vulnerabilities in production.
Do Cycode's IaC Security Tools Integrate with Any CI/CD Pipeline?
Cycode is built as a unified Application Security Posture Management (ASPM) platform, making deep integration a core necessity. Its primary goal is to shift IaC security left by becoming a mandatory guardrail within the CI/CD workflow. This integration ensures that security checks are automated before provisioning and management occur, including:
- Native Integrations: Cycode connects directly with popular CI/CD systems like GitHub Actions, GitLab CI/CD, Jenkins, Azure DevOps, Bitbucket Pipelines, and others.
- Workflow Enforcement: It automatically scans pull requests for IaC misconfigurations (in Terraform, Kubernetes, etc.) and can block the pipeline from executing a deployment until critical issues are remediated.
- Real-time Feedback: Integration delivers security findings and suggested auto-fixes directly back to the developer within their familiar CI/CD environment, preventing insecure infrastructure from ever reaching production.
How Does Cycode Help Detect and Manage Exposed Secrets in IaC Templates?
Detection and Prevention
Cycode uses an advanced IaC scanning tool and a specialized secrets detection engine that continuously scans IaC files (Terraform, CloudFormation, Kubernetes, etc.) for patterns indicative of sensitive information—like API keys, passwords, and tokens.- Shift-Left Enforcement: Scans are automatically triggered on every commit and Pull Request (PR), blocking the secrets from ever being merged into the main codebase or deployed into the cloud.
Context and Management
Cycode doesn't just find secrets; it prioritizes and helps automate their remediation.- Risk Prioritization: The platform applies context to the exposed secret (e.g., what services can it access?) to provide a risk score, ensuring security teams focus on the most exploitable and high-impact exposures first.
- Developer-First Fixes: When a secret is found, Cycode provides automated remediation suggestions or generates a clean PR with the necessary fix, reducing the Mean Time to Remediate (MTTR) by allowing developers to resolve the issue directly within their existing workflow.
Does Cycode Support Real-Time Developer Feedback During Pull Requests or Commits?
Here is how real-time feedback is delivered:
1. In-Workflow Feedback for Pull Requests (PRs)
Cycode integrates directly into Source Code Management (SCM) platforms (like GitHub, GitLab, and Bitbucket) to provide instantaneous feedback on code changes:- Automated PR Comments: On every PR, Cycode automatically scans the code changes (diff) for secrets, IaC misconfigurations, and other security issues. Findings are displayed as inline comments within the PR interface, pointing directly to the vulnerable line of code.
- Security Status Checks: The platform updates the PR's security status check (often showing a "failed" status if a high-severity issue is found), enabling automated branch protection rules to block the merge before the insecure code is accepted.
- AI-Driven Remediation: In many cases, the feedback includes AI-suggested code fixes that developers can apply directly within the PR or their IDE, accelerating the time-to-remediate (MTTR) without requiring security team intervention
2. Local Feedback via IDE and CLI
To catch issues even earlier, before the code is pushed to a remote repository:- Pre-Commit Hooks: Developers can configure the Cycode CLI to run scans as pre-commit hooks. This instantly blocks a local commit if hardcoded secrets or critical misconfigurations are detected, ensuring the issue is fixed while the code is still on the developer's machine.
- IDE Plugins: Cycode offers plugins for popular Integrated Development Environments (VS Code, JetBrains), providing real-time, in-line security analysis and context directly as the developer types the code.

 Solution Brief
Solution Brief