When you think about intellectual property, most people think of ideas (concept), design, documents, customer data. But they forget about the need to protect the source code – which is the critical part of an organization’s IP. When source code gets leaked, stolen or even deployed and left exposed ‘in the wild’, it can be detrimental to the organization.
Source code is extremely valuable and it needs to be protected. But, despite the critical role it plays in building applications, too many organizations continue to neglect putting the measures they need to have in place to protect their source code. In recent months, major companies like Mercedes-Benz , Nintendo and even Microsoft have had their source code leaked and vulnerabilities exposed.
So why aren’t companies rushing to protect their source code? Because source code is much more challenging to secure.
Your source code is everywhere.
Imagine a building with eight entrances/exits. On a super busy city street in any heavily trafficked area. Thousands of people walk by each day.There are no guards securing any of the doors and the doors are either unlocked or have flimsy, easy to break locks. Anyone can come and go as they wish. Would you want to live there? Work there? Probably not. Why? Because it’s not secure, which means everyone and everything in the building is vulnerable to theft and worse.
You are the source….code. You need to be secured. So does your code.
The Source Code Management System Conundrum
The problem with source code management systems (‘SCMs’) is that they are built with a specific goal: to improve collaboration, productivity and delivery. Not to secure source code.
SCMs are typically managed by R&D teams which work based on agile methodologies – aka deploy continuously and quickly. Unfortunately, this also means they tend to think about the security aspect later in the process, which is too late.
Access controls are typically not set up properly and it’s far too common and dangerous a practice that everyone has access to everything (also in part due to Github’s permission model), not to mention the plethora of leftover permissions that organizations tend to forget to update – leaving source code even more exposed.
That explains the back story. But why is source code so hard to secure?
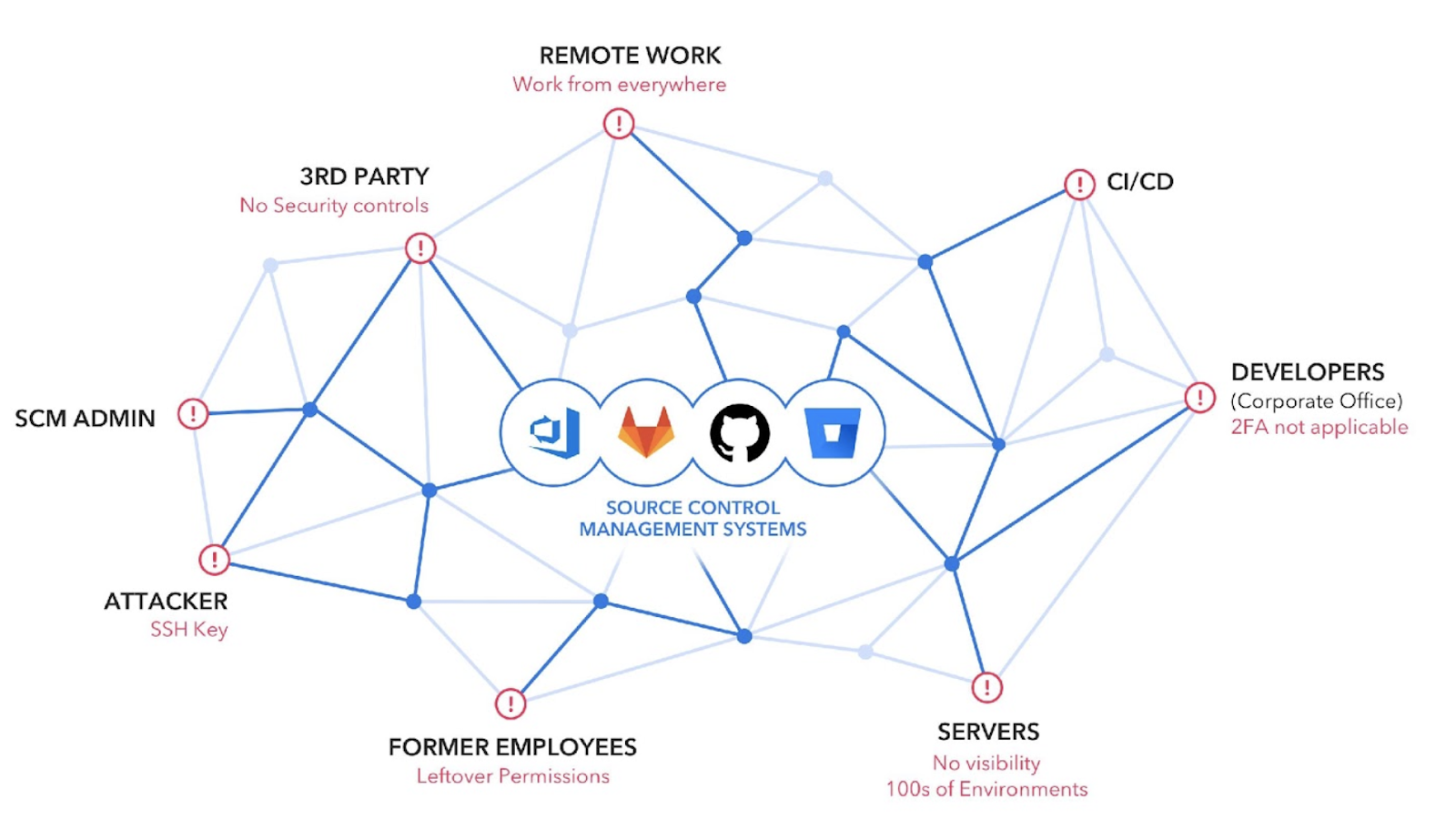
Out Of Control Source Code: Blame The Sprawl
The short answer to why source code is so difficult to protect is due to the sprawl.
Organizations have developers working from companies offices, from home or other remote locations. No CISO would be ok with a developer with access to intellectual property sitting in a Starbucks sipping a venti latte and cloning your company source code over open, unsecured wifi -in fact, any CISO would likely be horrified.
Don’t forget about other outsourced contractors or offshore developer centers and former employees who never had their access revoked.
With the shift left trend, more and more systems are getting access to the source code. Be it the CI/CD systems, ticketing management or productivity tools. Compromising any of these systems or servers will result in granting uneccessary access to the source code.
That’s the sprawl factor: having all of these people with a copy of or access to your very valuable source code, sprawled out all over.
Let’s add insult to injury with a little reminder about where your source code is stored, that’s right, the source control management systems. Systems that were specifically built for collaboration and NOT for security.
How Do Orgs Protect Source Code Today?
The companies that do make the effort to secure its source code usually use one or several of these three arduous methods:
1 – Data Loss Prevention (‘DLP’) Solutions – These solutions have pros, but the major con: False positives caused when events are mistakenly triggered by a policy. This is why most companies leave source code out of their DLP configuration.
2 – Manual Access Review – A very tedious process which is hard to track and existing solutions don’t support source control integrations
3 – Usage of Internal Scripts – Or, other open source projects to detect code leaks, secrets and misconfigurations. All very time consuming to develop and all produce a high false positive rate.
Three strikes and sorry, but you are out.
How Every Organization Should Protect Its Source Code
The ideal model to protect source code has a very simple formula.
1 – Immediate Visibility to your entire source code asset inventory
2 – Code Leak Detection across the public domain
3 – Detect Secrets that are embedded or hidden in code
4 – Reduce Insider Threat Risk by automatically flagging and revoking any unneeded or expired access permissions
5 – Real-Time Risk Detection of any bad security configurations
These are the de facto practices organizations need to protect source code. If you want to implement these methodologies quickly, reach out to us to see how our source code control, detection and response solution can protect your source code for you.
Originally published: May 26, 2020