In the world of DevOps and cybersecurity, secrets like API keys, tokens, or passwords maintain the functionality and security of your applications. However, managing these secrets can pose a substantial risk if not handled correctly. Additionally, many enterprise-level companies need to know how to prioritize the secrets to remediate, because they have tens of thousands of secrets. They need to know which exposed secrets should be remediated first, and which could be handled later, to minimize risks.
The consequences of those risks can be substantial. No team is immune to this, either. In 2022, roughly 10% of authors uploading to GitHub uploaded a secret, and of all the cybersecurity breaches in 2022, over 50% of them involved exposed secrets.
This article discusses secrets and what they are, the need for secret validation, and announces a new feature for our platform: Secret Validation.
Active and Inactive Secrets:
API Keys, Tokens, and Passwords
An API key is a unique identifier used to authenticate a user, developer, or calling program to an API, serving as a control mechanism for accessing the associated software application or service’s data and functions. A token is a piece of data created by a server, representing the right to perform some operation, often used for authentication and authorization in secure web services and applications. Finally, and most familiar, A password is a string of characters that a user provides to verify their identity to a system, typically to gain access to resources protected by that system.
Active secrets enable secure communication between various parts of your system. These secrets, if exposed, could provide unauthorized access to sensitive resources, leading to significant security breaches. Meanwhile, inactive secrets are not in current use, but still exist within the system. If exposed, they can still cause risk and potential harm to your system. These breaches include events like the 2019 Scotiabank breach, which briefly exposed login credentials for some of its 25 million customers and 97,000 employees.
Because of the risks, it’s critical to manage these secrets effectively, ensuring they are only accessible to those who need them, and are stored and transmitted securely. This is where Cycode’s new Secret Validation feature comes into play. It helps you identify and manage both active and inactive secrets effectively, enhancing your overall security.
How Cycode’s Secret Validation Works
We have extended our platform’s scanning capabilities to encompass Confluence, AWS S3 buckets, and Azure environments. Cycode now scans for secrets anywhere and everywhere in your SLDC. This includes source code, build logs, infrastructure as code, Kubernetes clusters, version histories, and more. This ensures you are protected from compromised insiders, malicious outsiders, and code leakage.
This helps organizations proactively identify and remediate hidden security risks by detecting hard-coded secrets in diverse platforms and cloud services. By including Confluence, AWS, and Azure, we can detect addresses a wider spectrum of security vulnerabilities across collaboration platforms and major cloud providers.
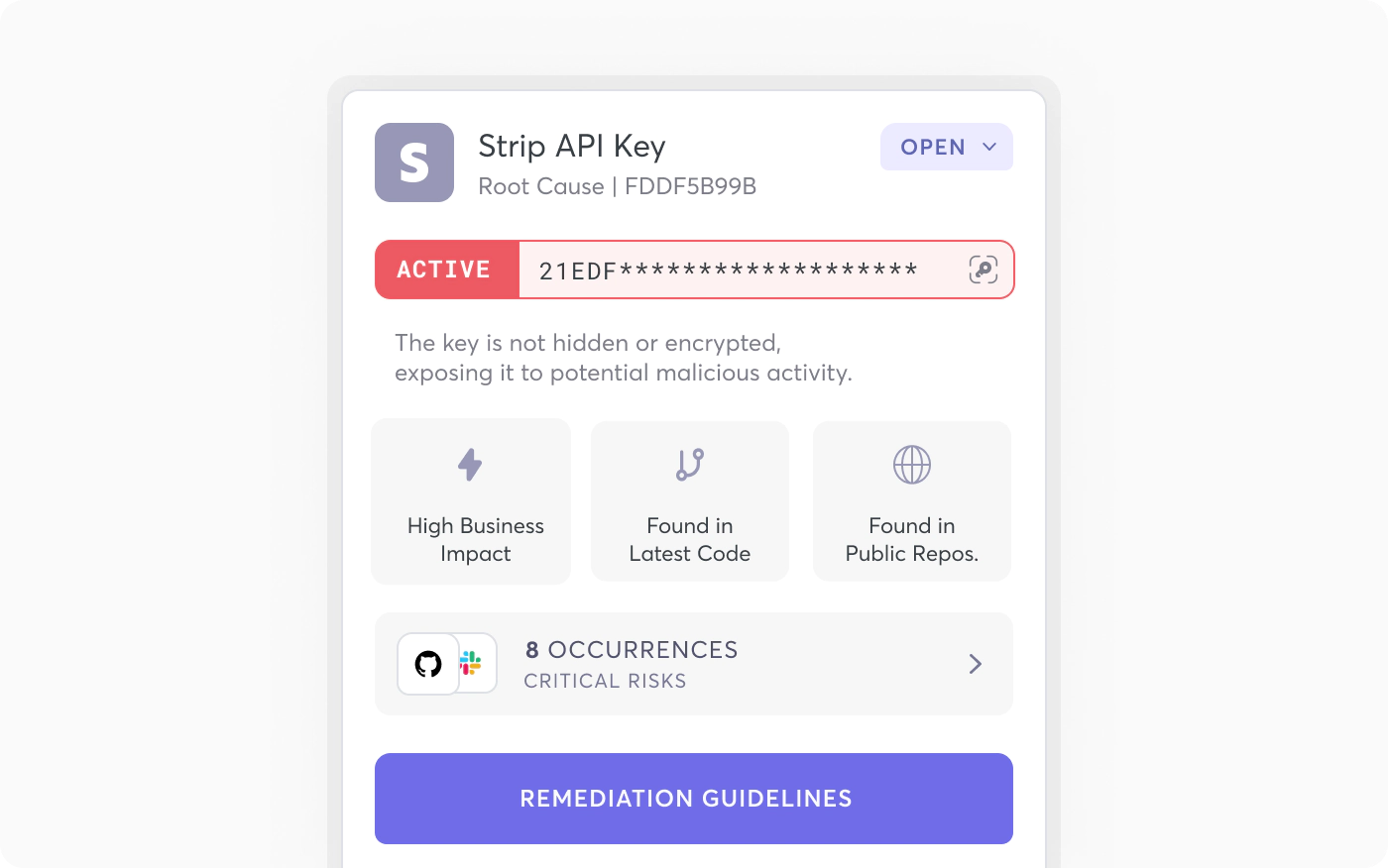
Our Secret Validation feature offers a robust set of capabilities to give you complete control over your secret management. You can enable or disable secret validation according to your needs. You also can enable it for specific secret types, allowing for a gradual rollout.
One of the key aspects of this feature is the different states of validity it offers for your secrets: active, inactive, failed to check, pending, and unknown. Each state gives you a clear understanding of a secret’s status, helping you make informed decisions.
1. Configuring and Using Cycode’s Secret Validation
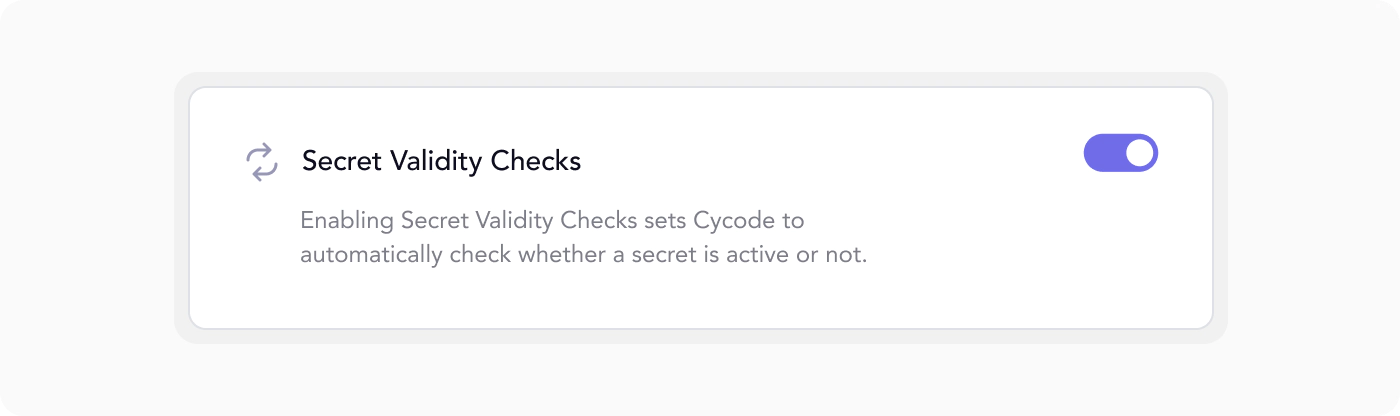
Configuring our Secret Validation feature is straightforward. You can enable or disable validity checks at your convenience.
One of the unique features we offer is the periodic validity checks based on a secret’s age. If a secret is less than a year old, it’s checked weekly. This ensures your secrets are always up-to-date.
This feature also allows you to input multiple endpoint URLs for the same secret type, thus offering more flexibility. If you need more control, you can manually trigger on-demand validation for any detected secret, regardless of its status.
2. Auto-Resolution
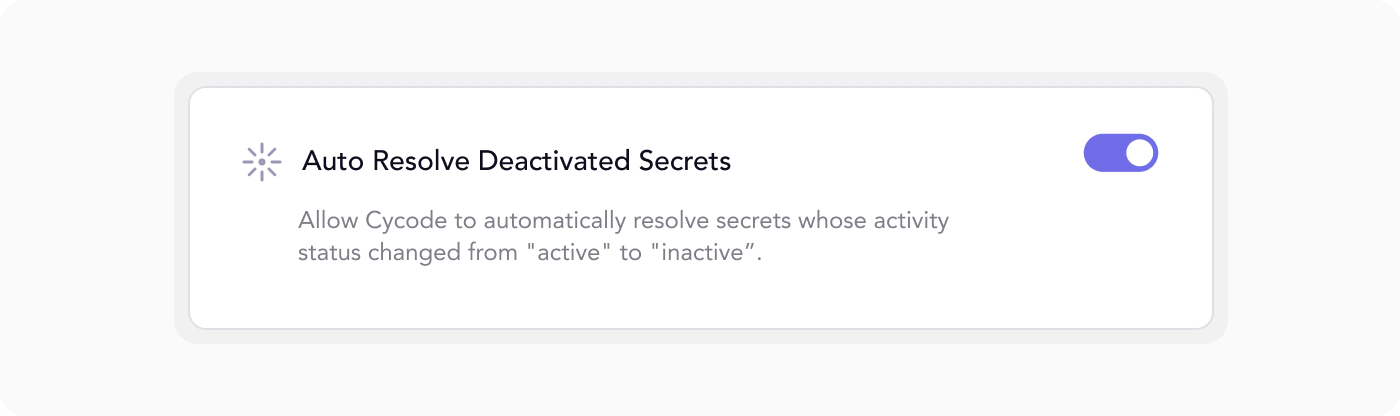
Cycode’s Secret Validation feature brings in a new level of automation with its auto-resolution functionality. It is designed to automatically mark a secret as ‘Resolved’ within Cycode when the secret is identified as revoked or invalid.
This allows your team to save valuable time by not having to resolve these issues manually. Moreover, it keeps your violation record clean and focused only on active and potentially harmful secrets, improving the overall efficiency of your security management.
In a nutshell, our auto-resolution feature helps streamline your secret management process by automating the resolution of revoked secrets.
Conclusion
Whether they’re active or inactive, handling secrets is crucial to ensuring your applications’ security and functionality. With Cycode’s Secret Validation feature, managing these secrets becomes a breeze. It offers a perfect blend of control, flexibility, and usability, making it an indispensable tool in your security arsenal. We encourage you to enable this feature and experience the enhanced security it brings to your SDLC.
Remember, security is not a one-time activity, but a continuous process. This feature is one part of our strategy to provide more robust breadth and depth to support our Fortune 500 customers. This expansion helps organizations proactively identify and remediate hidden security risks by detecting hard-coded secrets in diverse platforms and cloud services. By expanding to encompass Confluence, AWS, and Azure, Cycode delivers a comprehensive solution addressing a wider spectrum of vulnerabilities across collaboration platforms and major cloud providers. With this enhanced offering, enterprises can strengthen their data protection efforts, eliminate potential points of compromise, and maintain robust cybersecurity practices throughout their infrastructure.
Learn more about us or book a demo today!
Originally published: July 24, 2023