Cycode revolutionizes CI/CD security and pipeline integrity with its newest version of Cimon, which is part of the Cygives initiative.
Software development ecosystems thrive on continuous integration and continuous delivery (CI/CD) pipelines. With attackers increasingly targeting the software supply chain, CI/CD tools are vulnerable entry points. The escalating threat landscape requires robust security measures, and the delivery of these measures should be as frictionless as possible for developers. This is where the groundbreaking integration of Cimon with the SLSA framework revolutionizes CI/CD pipeline security.
Achieving evidence-based compliance within CI/CD pipelines is crucial for building trust and ensuring the security of your software supply chain and produced artifacts. However, traditional methods for achieving compliance often rely on manual processes, which can be slow, error prone, and leave limited audit trails. This lack of concrete evidence makes it difficult to demonstrate compliance during audits or pinpoint the root cause of security incidents. Cimon tackles this challenge by automating the collection of trusted telemetry throughout the build process, providing a verifiable record of software artifact provenance. This shift to evidence-based compliance empowers organizations to streamline audits, confidently track the integrity of their software, and minimize friction to engineering teams.
What Is Cimon?
Cimon (CI Monitor) is a state-of-the-art runtime security agent designed to protect CI/CD pipelines. It leverages eBPF technology to monitor and mitigate attacks within the kernel, offering real-time protection. Cimon’s capabilities include monitoring process execution, network access, and file access, effectively detecting and responding to security breaches like SolarWinds and CodeCov.
The following is an example of a Cimon process tree report in the Cycode platform:
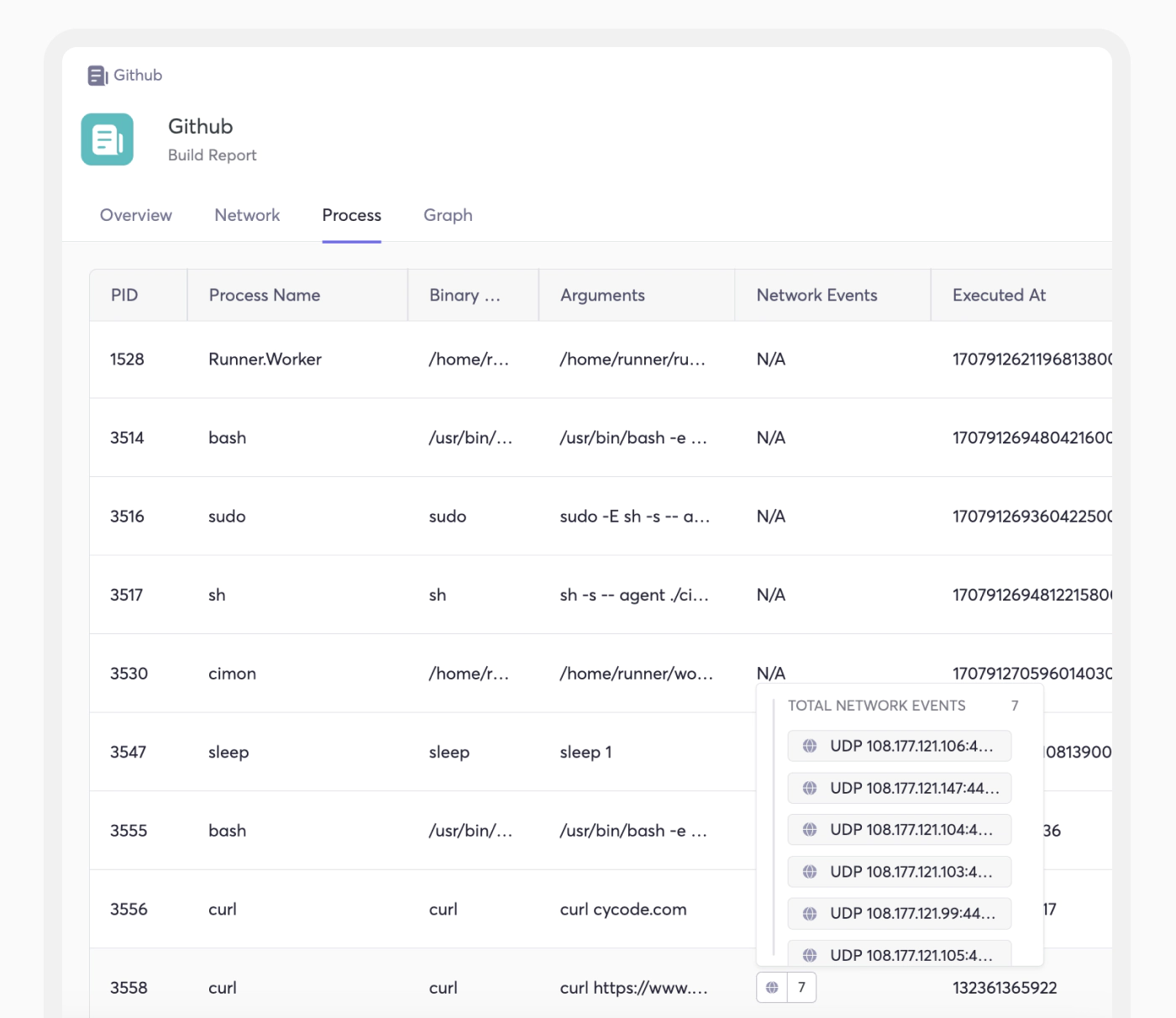
SLSA Framework: The Industry Standard for Artifact Integrity
SLSA provides a common language to discuss how secure supply chains and software really are. For each of the SLSA levels, specific build security controls are defined.
SLSA controls require producing provenance attestation of the software as a core component. This attestation confirms the origin and integrity of software artifacts, assuring their security throughout the development lifecycle.
Current Challenges with SLSA Generation
While the SLSA framework offers a clear path to secure software supply chains, generating SLSA attestations can be a hurdle. Traditionally, this process involves developers adding attestation generation for each artifact individually. As the build process grows more complex, tracking artifacts through the SDLC becomes cumbersome. This can lead to inconsistencies if not meticulously maintained. Additionally, not all build tools offer native support for SLSA attestation generation, creating compatibility issues and further complicating the process.
Automatic Evidence Gathering with Cimon
As a result of Cimon’s robust and mature feature set, it can now identify development events, pinpoint resulting artifacts, and generate SLSA attestations automatically.
This integration represents a major advancement toward a comprehensive tool that satisfies the Secure Software Development Framework (SSDF) requirements, fulfilling our vision for complete supply chain security.
Demonstrating the Workflow
Here’s a typical GitHub Actions workflow showcasing this integration:
steps:
- name: Run Cimon
uses: cycodelabs/cimon-action@v0
with:
client-id: ${{ secrets.CIMON_CLIENT_ID }}
secret: ${{ secrets.CIMON_SECRET }}
feature-gates: 'DataAnalysis=1'
- name: Checkout Code
uses: actions/checkout@v4
- name: Building Simple Go Project
run: |
go build
- name: Login to DockerHub
uses: docker/login-action@f4ef78c080cd8ba55a85445d5b36e214a81df20a
with:
username: ${{ secrets.DOCKERHUB_USERNAME }}
password: ${{ secrets.DOCKERHUB_TOKEN }}
- name: Building and Pushing Docker Image
run: |
docker build -t cycodelabs/simple-go-project:latest .
docker push cycodelabs/simple-go-project:latest.
Let’s explain the moving parts:
- We start the pipeline with standard Cimon installation. With minimal configuration, Cimon is integrated within the pipeline within just a few lines.
- We do a simple build procedure:
- Checking out our codebase
- Building a Golang executable
- The executable is embedded within a container image and pushed to a remote container registry.
The described process is a typical example of artifact creation, where native code is encapsulated into containers for deployment in cloud-native ecosystems. Despite its simplicity and popularity, this approach encounters challenges in dependency mapping and artifact provenance creation. While container images are easily traceable in the cloud, tracking the binaries within the container remains unfeasible with current tools. As a result, provenance generation for each artifact presents significant difficulties. To tackle this challenge, Cimon identifies such artifacts and enables automatic provenance generation for enhanced traceability.
Evidence Collection in Self-Hosted K8s Clusters
A popular setup in enterprise-grade CI environments is utilizing Kubernetes-backed self-hosted clusters to run the build process. By following a straightforward setup process, developers can harness Cimon’s capabilities within their Kubernetes environments.
kubectl create ns cimon kubectl create secret generic cimon-secrets --from-literal=CIMON_CLIENT_ID="Insert Cimon Client ID Here" --from-literal=CIMON_SECRET="Insert Cimon Secret Here" -n cimon kubectl apply -f https://cimon-releases.s3.amazonaws.com/cimon-ds.yml
With these steps completed, Cimon becomes an integral part of your self-hosted Kubernetes environment, automatically gathering evidence, identifying artifacts, and generating SLSA attestations.
SLSA Automation Results
By running the above example and exploring the Cycode Risk Intelligence Graph (RIG), we observe that two attestations have been uploaded – one for the Golang executable and another for the docker image. This allows organizations to analyze the attestations further, preserve them as evidence, or conduct an informed incident response process.
A developer running Cimon doesn’t need to configure anything as Cimon identifies what provenance needs to be generated, granting SLSA 1 with minimal effort on the developer’s part.

Plus, you get the Cimon runtime protection tooling, which monitors processes and network events, blocks unauthorized access, and ensures the build process can be trusted.
How Cimon Works
Under the hood, Cimon leverages its eBPF superpowers to trace every process, network connection, and filesystem operation within the operating system and identify the crucial events that led to the creation of software artifacts. Using this deep understanding, it automatically generates SLSA attestations – detailed reports that document the origin, build process, and provenance of your software packages. Think of it as an irrefutable birth certificate for each artifact, guaranteeing its legitimacy and trustworthiness.
Cimon supports a wide range of languages and builders, including Go, C, Java, Docker, and more.
How Cycode Complete ASPM Can Help Secure Your Software Supply Chain
While impressive on its own, Cimon’s automatic SLSA generation truly shines within the Cycode ASPM platform. The seamless integration of Cimon and Cycode empowers companies to build secure software from the ground up, leveraging the strengths of Cimon runtime capabilities with the richness of the Cycode Risk Intelligence Graph (RIG). It seamlessly integrates with minimal disruption, providing clear visibility and control to developers.
Attestations generated by Cimon are uploaded and analyzed by Cycode, simplifying the compliance process and allowing the artifact to be traced back to the code, granting unparalleled visibility into the SDLC. This powerful duo empowers developers to focus on building great software because they are confident in the security of their creations.
Learn More About Cycode
Cycode is the leading Application Security Posture Management (ASPM), providing peace of mind to its customers. Our Complete ASPM platform scales and standardizes developer security without slowing down the business, delivering safe code faster.
The platform can replace existing application security testing tools or integrate with them while providing cyber resiliency through unmatched visibility, risk driven prioritization, and just in-time remediation of code vulnerabilities as scale. Cycode’s Risk Intelligence Graph (RIG), the brain behind the platform, provides traceability across the entire SDLC through natural language.
To learn more about Cycode, book a demo now.


