Cycode workflows allow users to automate security functions such as alerting, ticketing, and remediation that respond directly to triggered violations or vulnerabilities. This helps teams improve their response time to security defects and provides visibility to security teams without forcing them to log in to overseen projects.
Developer environment integrations are already used for remediating security weaknesses–utilizing workflows within the Cycode platform allows users to use the abstraction power of the knowledge graph to enact specific actions under precisely defined conditions.
How Are Cycode Workflows Useful?
Automation is critical when solving programming problems, especially those which entail scalability. Cycode offers workflows that allow customers to partially or fully automate actions based on triggered events. Workflows may be configured based on specific violations, support filters, and can automatically execute remediate action on vulnerabilities.
The purpose of utilizing workflows depends on the intention of the organization. Workflows accelerate the remediation of found vulnerabilities, improve the visibility of vulnerabilities through ticketing, and help manage violations without having to handle them manually.
Workflows may be used for specific cases. For example, detecting a violation on any policy may be deemed relevant for a potentially dependent repo. Cycode workflows support such configuration which can help mitigate the risk of code tampering, cybersquatting attacks, and other vulnerabilities related to vulnerable dependencies.
How to Create a Cycode Workflow
To view and create workflows within the Cycode platform, users must first navigate to the “Workflows” tab. Cycode users may view the existing workflows in a table:
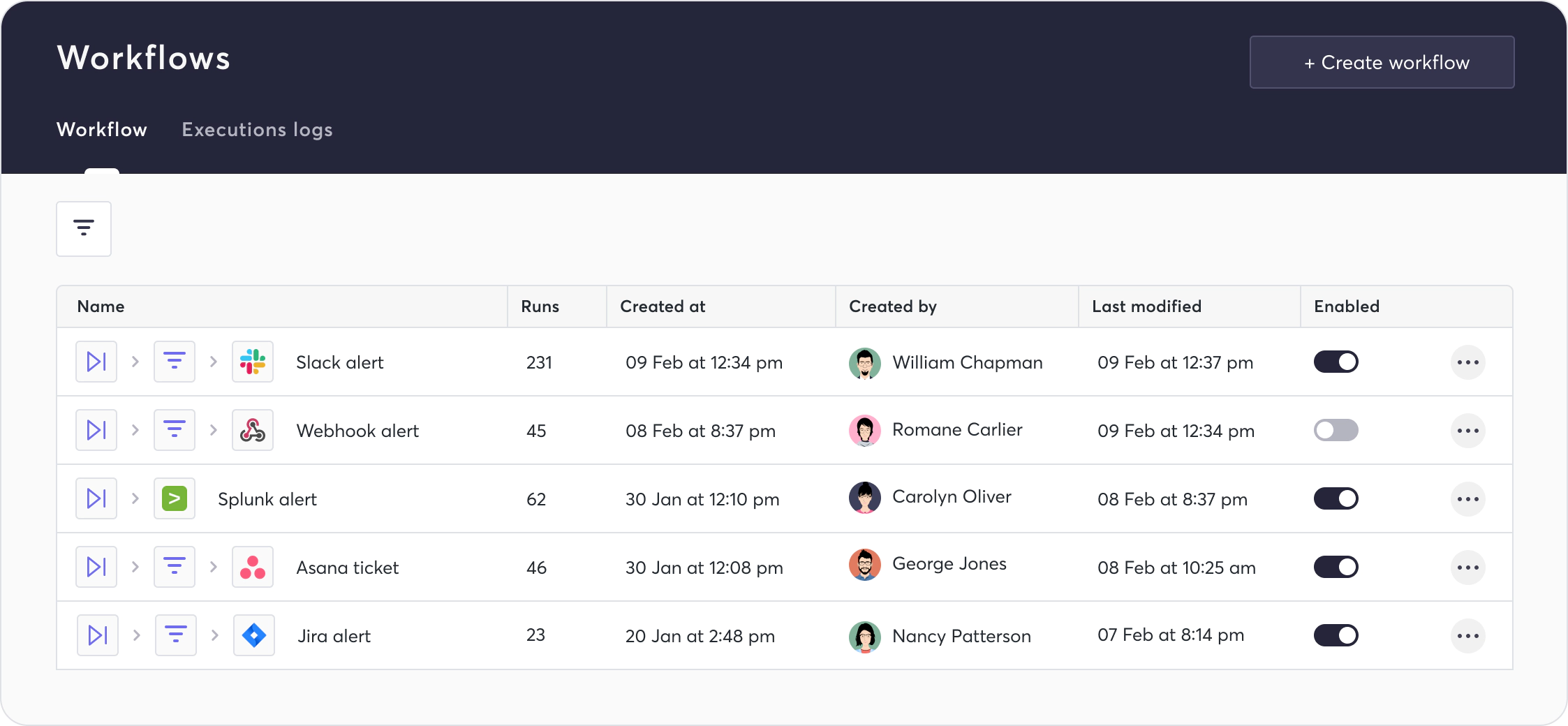
Information regarding each workflow is shown, including its name, outlined actions, run count, creation metadata, last modification time, and enablement status. More details may be viewed by clicking the ellipses.
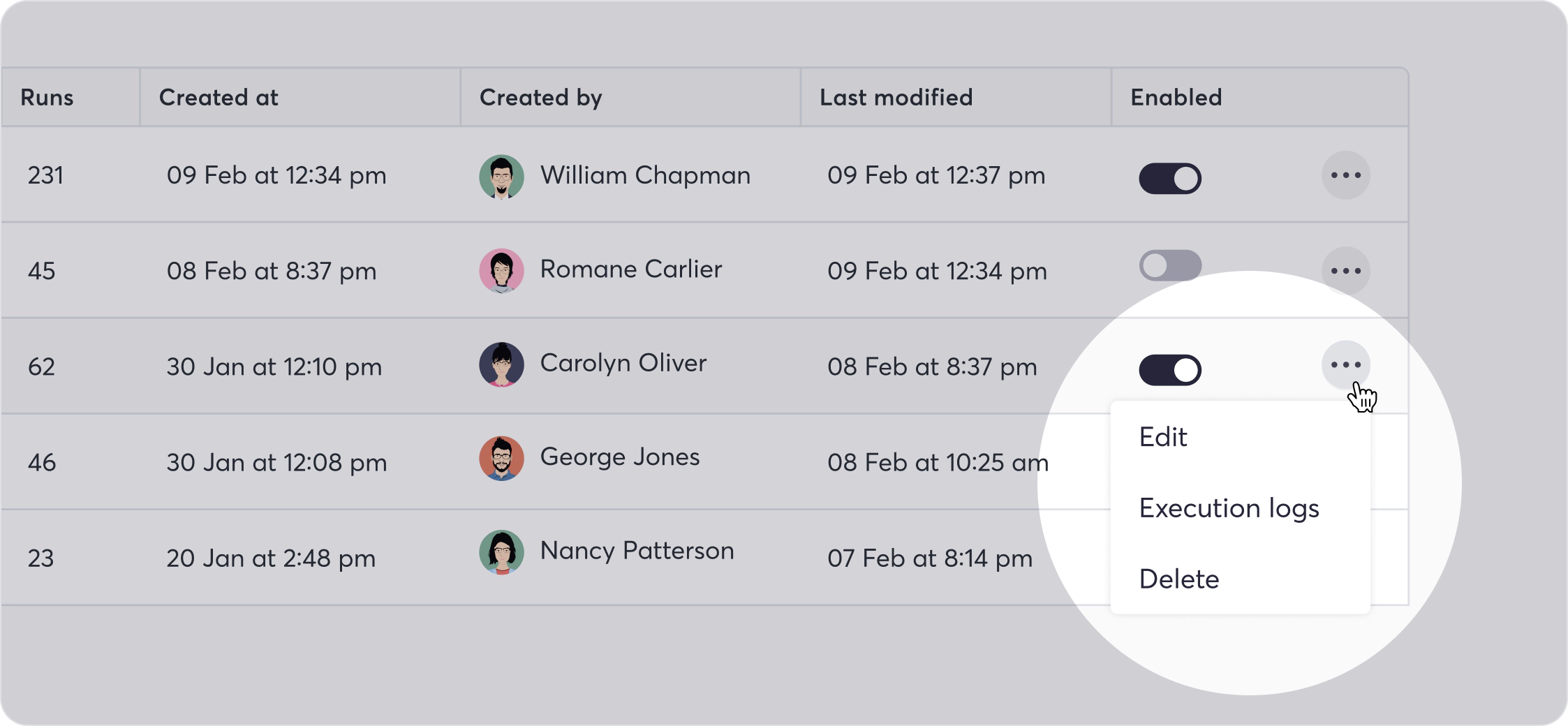
From here, teams may modify the workflow, users may view its execution logs, and users with permission may even delete the workflow.
Navigating to the Execution Logs section allows you to audit the runs of each workflow. Clicking the execution logs within the ellipses of an entry on the workflows tab directs you to the execution logs of that specific workflow:
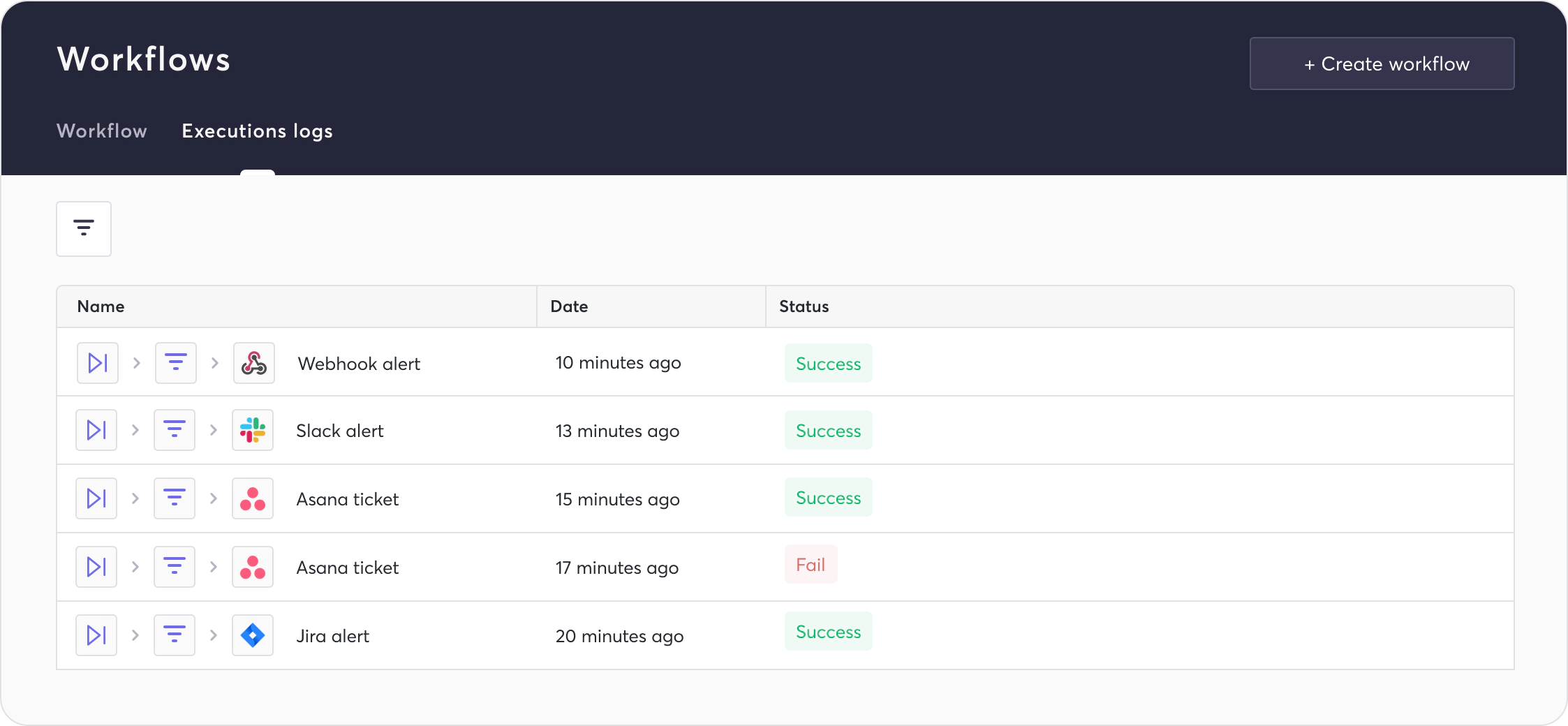
The workflow execution logs table contains the workflow outline, the workflow name, the run date, and the status of the specific workflow execution.
Click the “+ Create Workflow” button to create a custom workflow. This opens the create workflow popup:
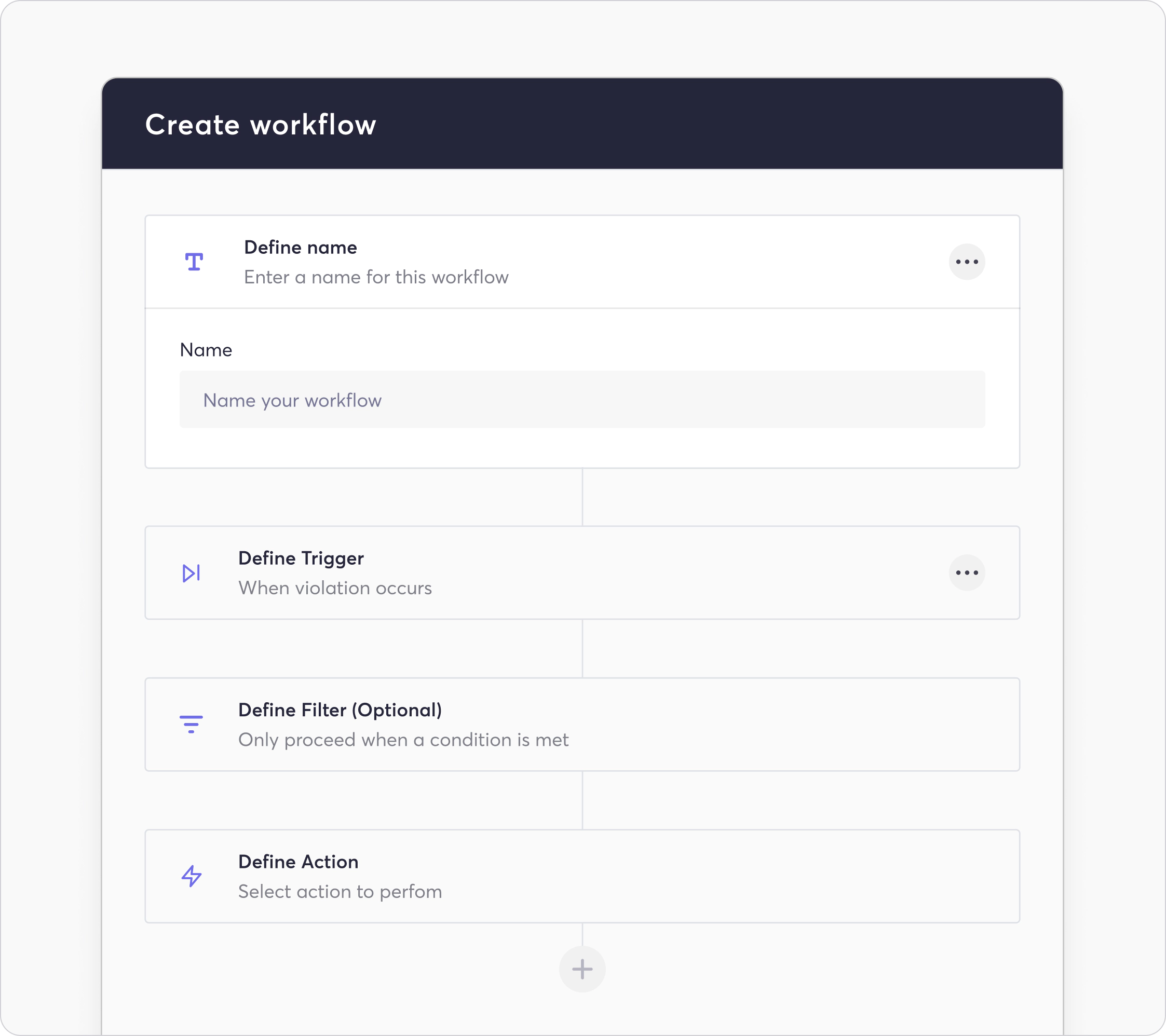
To create a workflow, users may enter the name, the trigger, the filter, and the desired action to take–these comprise the workflow components. These components allow Cycode users to define custom policies using the knowledge graph and take steps on the returned values.
Cycode Workflow Parameters
To illustrate, let’s image we want to create a workflow that automatically remediates violations where there exist stale admins in an organization. This will help this hypothetical organization automate its enforcement of the principles of least privilege across all its assets, thus strengthening governance and hardening security.
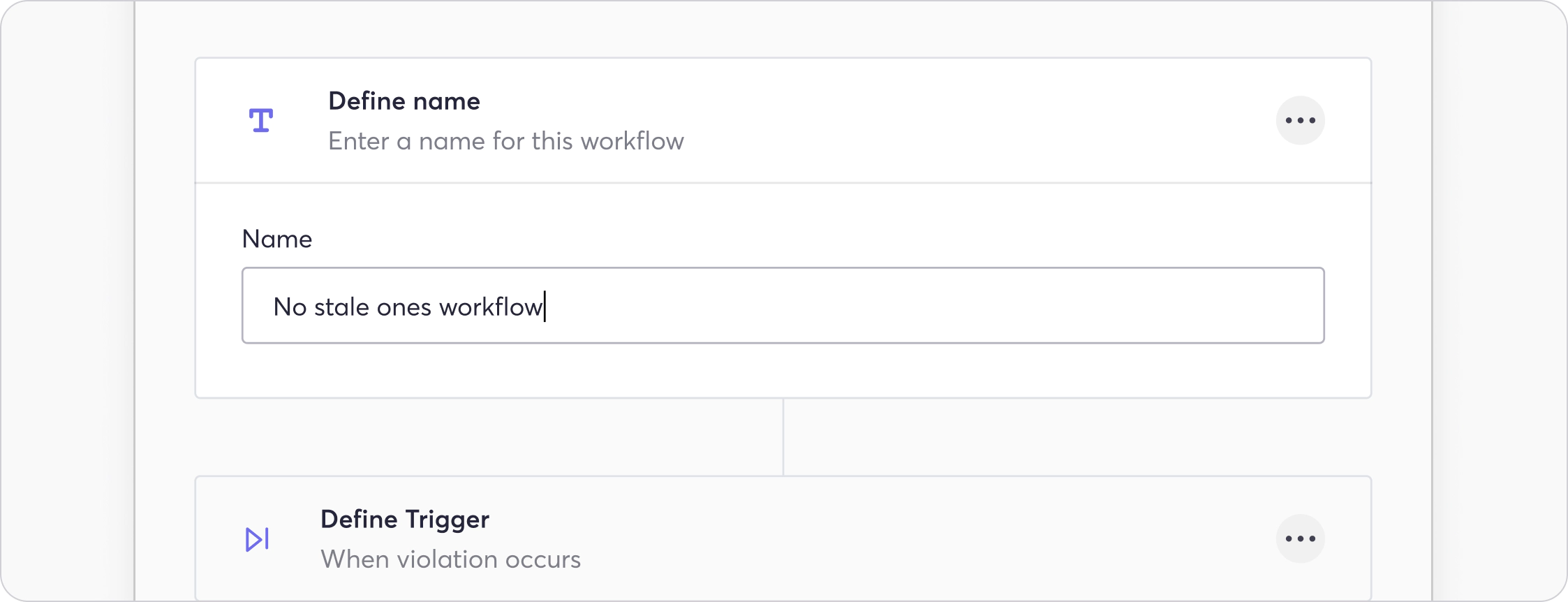
Name:
Enter a name for the workflow, ideally something descriptive for easy audit.
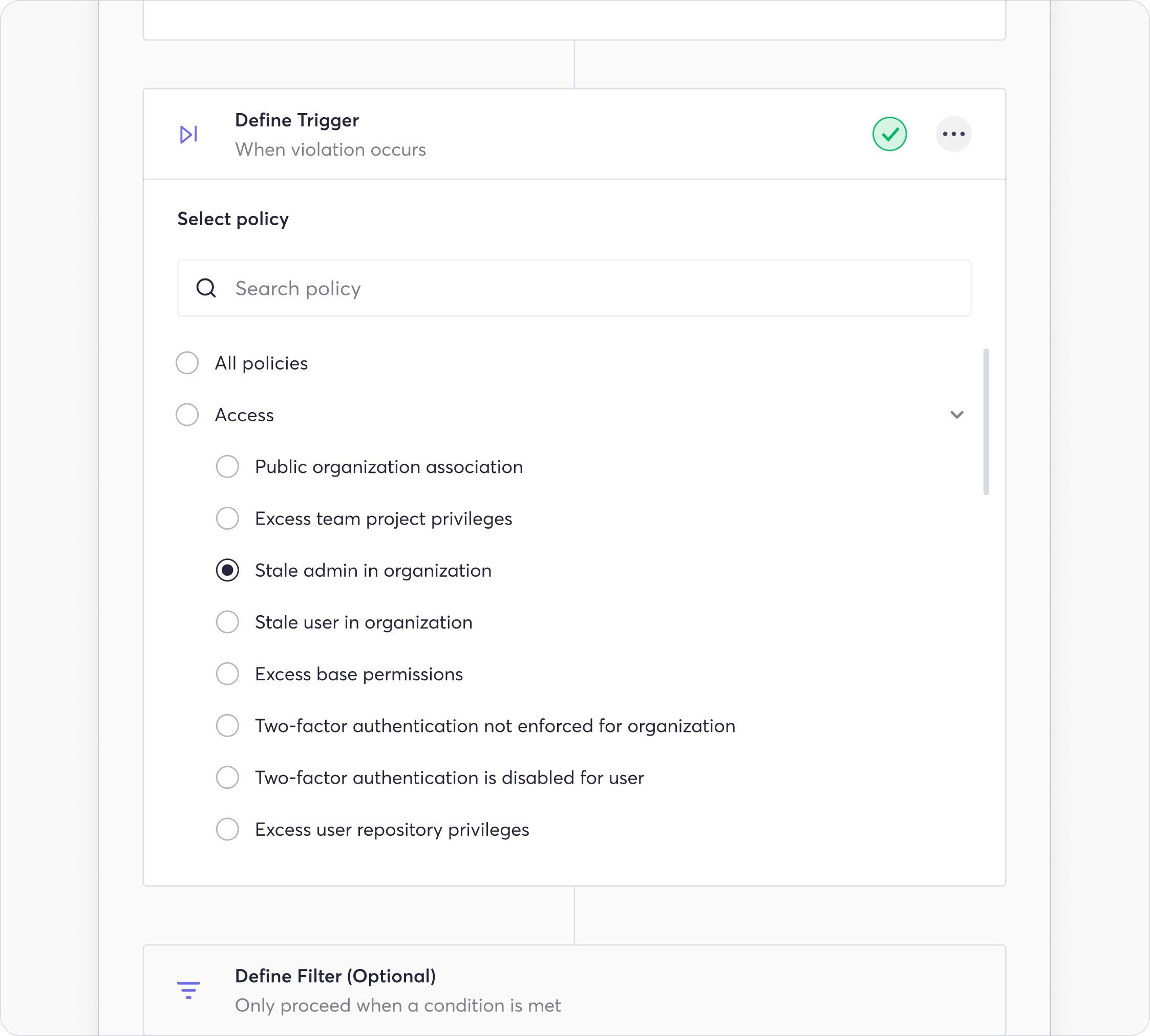
Trigger:
Define the policy or knowledge graph query used as the triggering event for the workflow. In our case, we select “Stale admin in organization” within access policies.
Filter:
We may precisely define when this workflow is run to prevent edge cases. In this hypothetical example, we do not enforce this policy on a specified user.
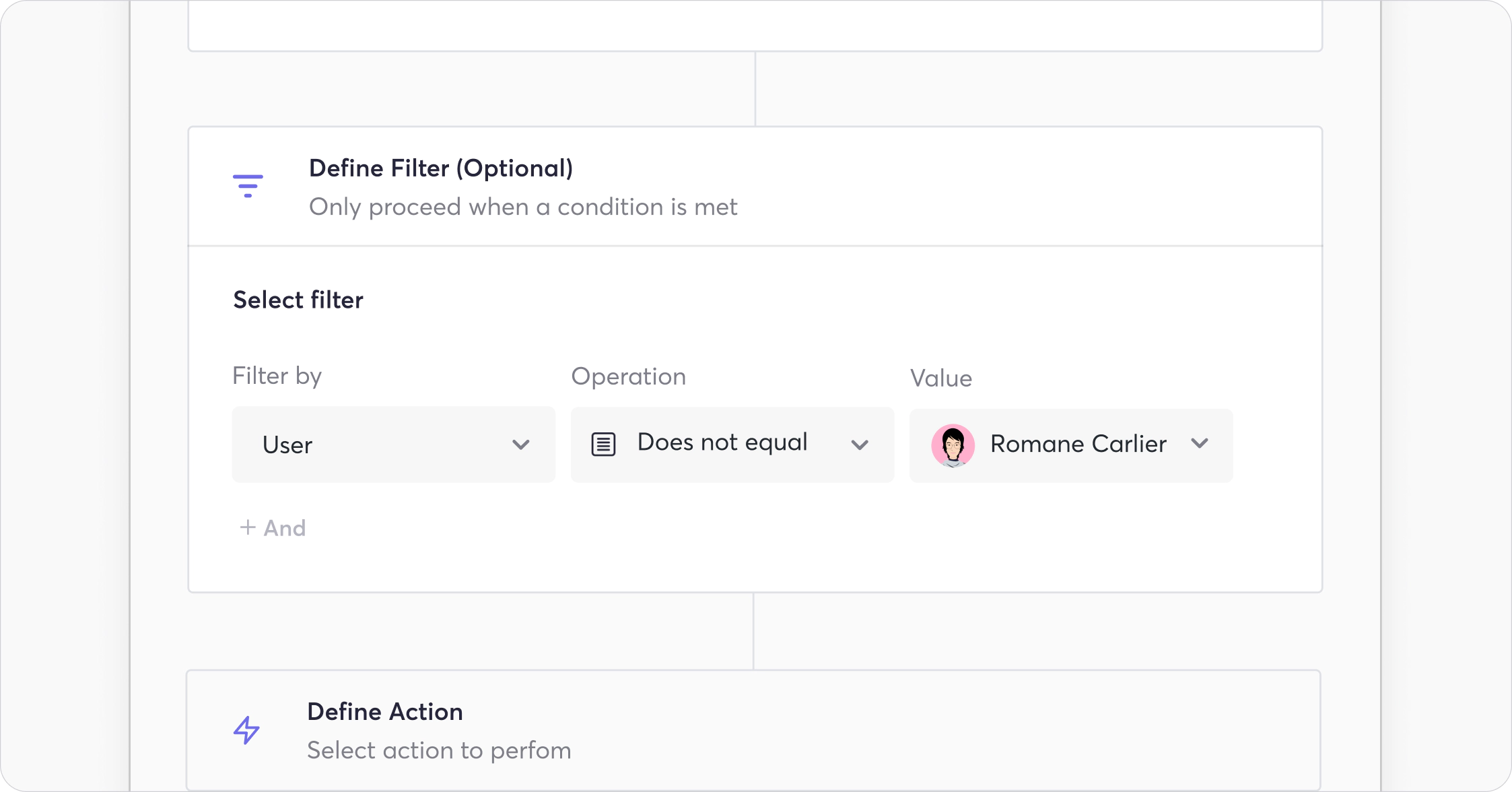
Additional filters include violation severity and user email, and operations include equals, does not equal, contains, and does not contain.
Action:
In our example, we desire to remediate the violation automatically. To accomplish this, we select “Take Action” under remediate, and select the option to “Revoke admin role”:
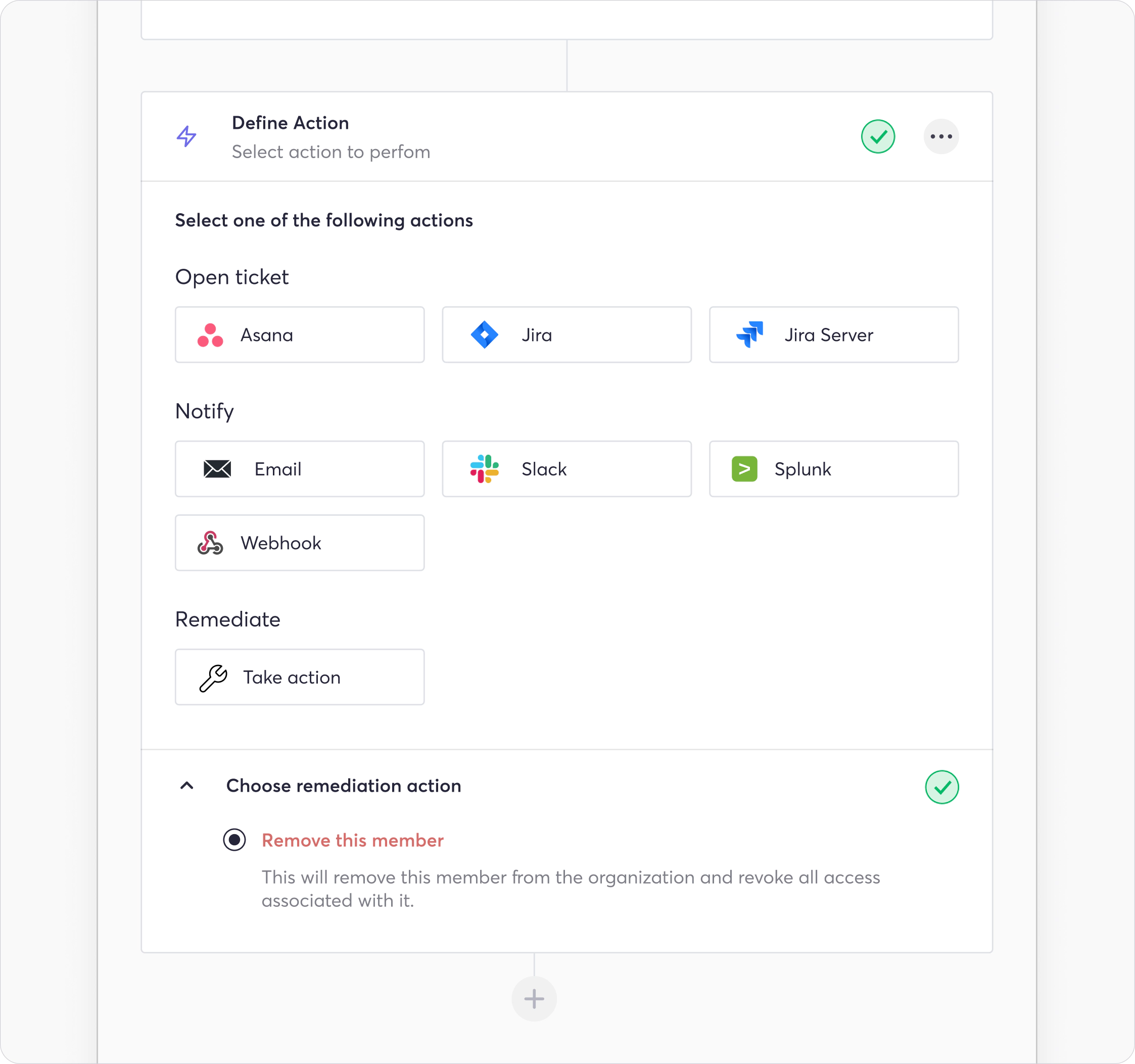
This is one of many possibilities when defining actions. Workflow actions may include ticketing, alerting, and remediation, depending on the violation and the enabled integrations.
Workflow Action Integrations
Workflow action integrations add to the strength of Cycode’s no-code integrations; these may be further subcategorized as alerts, tickets, and remediation.
Send Alert
The following integrations pertain to alerting that vulnerabilities have been found:
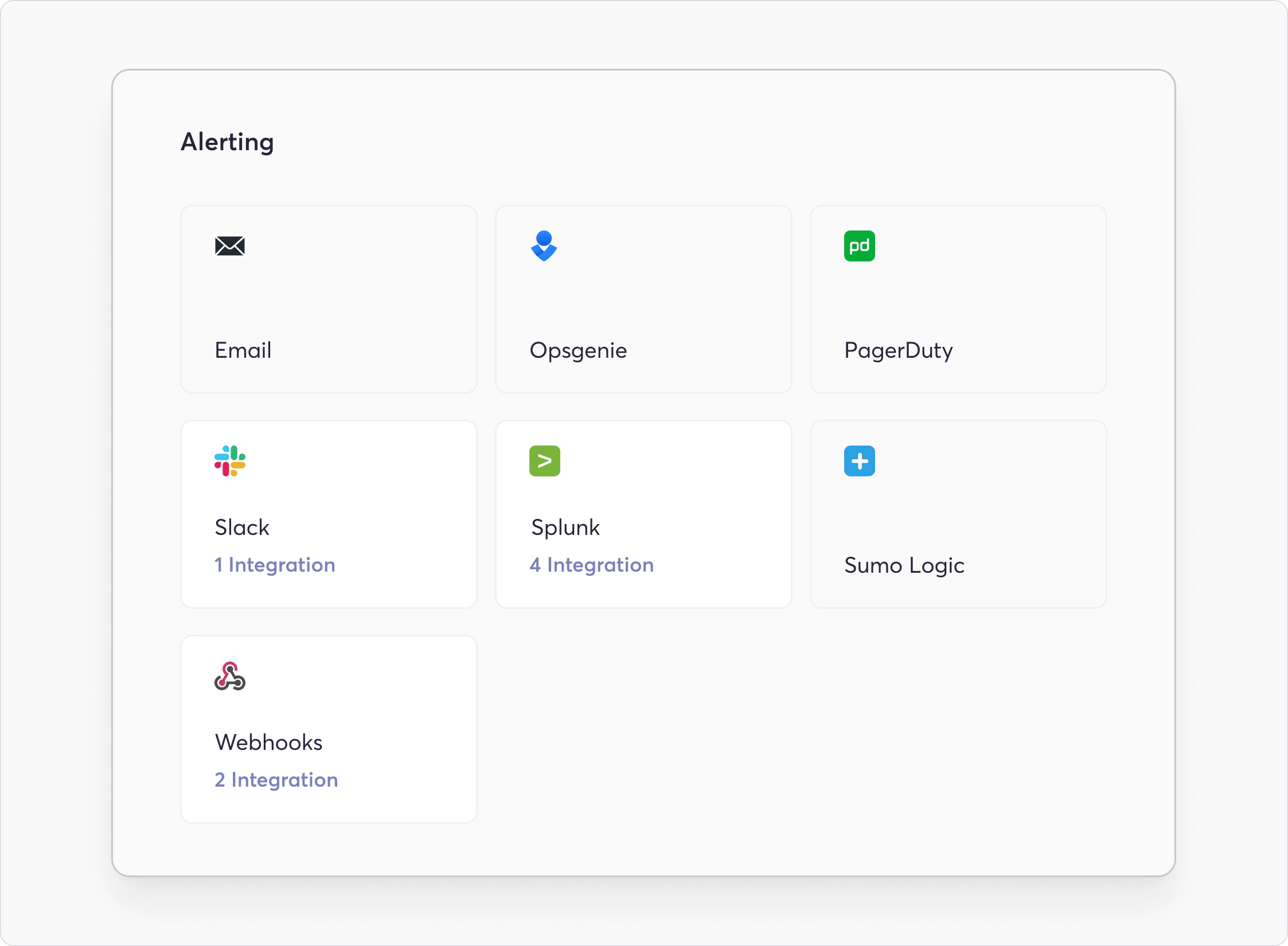
- Slack
- PagerDuty
- Sumo Logic
- Splunk
- Opsgenie
- Webhook
- Microsoft Teams (Upcoming)
Open Ticket
These integrations include functionality related to automatic ticket creation to track manual remediation efforts:
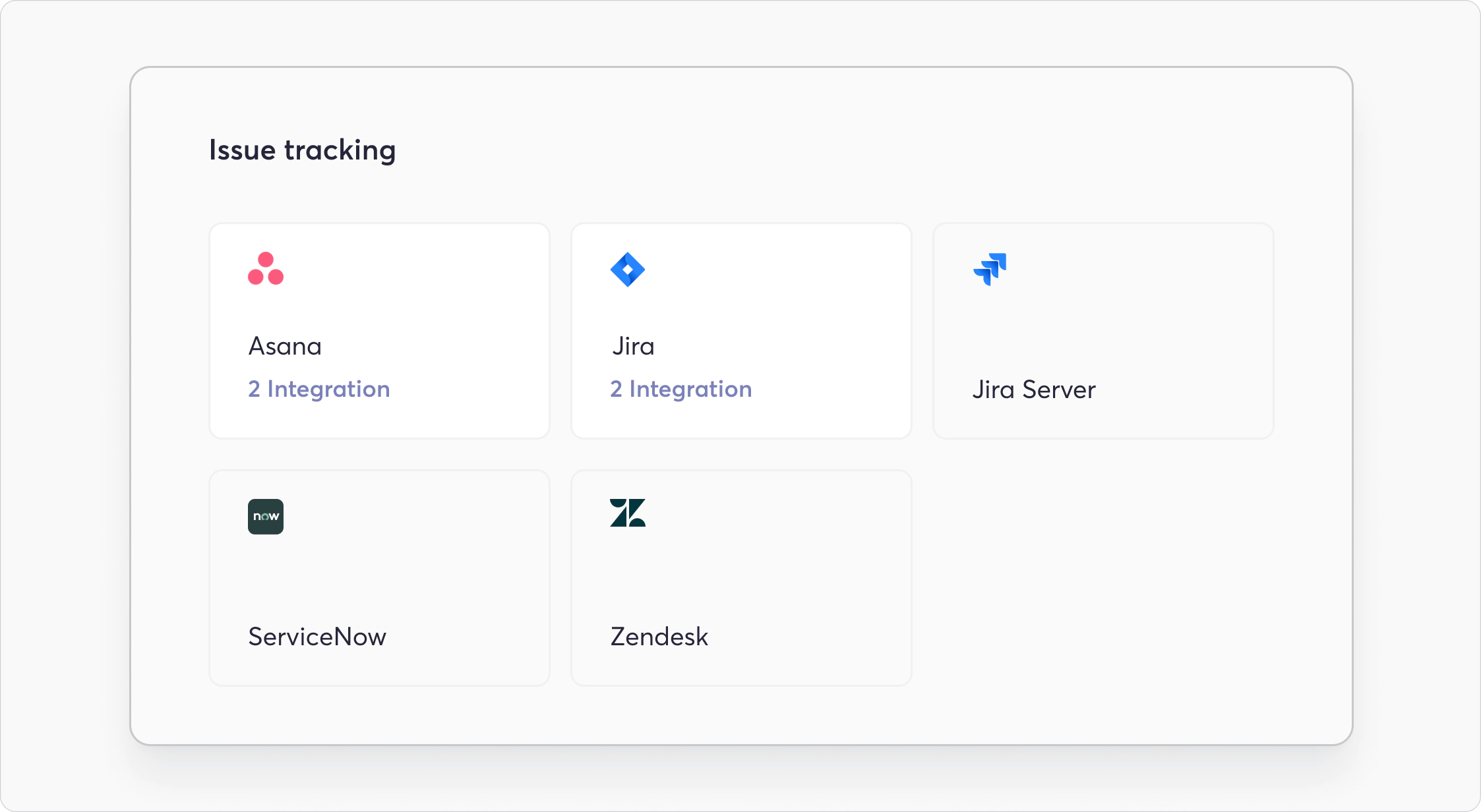
- Asana
- Jira
- Jira Server
- ServiceNow
- Zendesk
Remediation
Workflows support automatic remediation of violations. When automatic remediation is in place, workflows perform the work needed for organizations to adhere to best practices for security including enforcing principles of least privilege, establishing consistent governance of tools, and scanning for misconfigurations.
Cycode Workflows: Acting Upon Security Insight
In an increasingly interconnected world, it is important for organizations to act when vulnerabilities in dependencies are found. Cycode workflows meet this need by automating vulnerability mitigation when violations occur.
Security stakeholders may utilize Cycode workflows to provide alerts based on violations found within dependencies. This helps code owners stay aware of cases where a violation happens that is relevant for their owned repositories. Such workflows may prescribe remediation techniques that send emails when high severity violations occur, such as the integrity dangers introduced by the log4j vulnerability.
Learn More About Workflows
Schedule a demo or visit our website to learn how Cycode can help secure your software supply chains.
Originally published: March 3, 2022