Risk-Based Vulnerability Management (RBVM) was introduced to help security teams and developers focus their remediation efforts on their most critical risks. But is this approach enough to protect modern software supply chains from code to cloud?
It’s no secret that traditional approaches to vulnerability management just don’t cut it in today’s complex digital environments. Vulnerabilities need to be contextualized and viewed within the broader context of business risks.
In this article, we explore RBVM and how it works, discuss its benefits and limitations, and compare RBVM to a new category in cybersecurity: Application Security Posture Management (ASPM).
What Is Risk-Based Vulnerability Management (RBVM)
RBVM is a methodology for prioritizing security vulnerabilities based on their potential impact on the business. Unlike traditional vulnerability management, which often treats all vulnerabilities equally, RBVM takes into account several factors to determine which vulnerabilities should be addressed first. A few of these factors include:
- Asset criticality
- Exploit availability
- Exposure
- Existing security controls
- Threat intelligence
Note: RBVM does not perform vulnerability scans directly. Instead, it uses data from various vulnerability scanners and other security tools to prioritize and manage vulnerabilities based on risk.
The Difference Between a Risk and Vulnerability
Importantly, in the context of RBVM, it’s important to distinguish between the terms “risk” and “vulnerability”.
A vulnerability represents a potential weakness. Risk evaluates the likelihood and potential impact of that weakness being exploited, considering the broader business context.
In RBVM, the goal is not just to identify vulnerabilities but to prioritize them based on the associated risk, enabling teams to focus on the vulnerabilities that pose the greatest threat to the organization. More on this below…
Key Components of Risk-Based Vulnerability Management
Prioritization is the key difference between modern RBVM solutions and legacy vulnerability management tools. With that in mind, key components of RBVM include:
- Integrated threat intelligence: Data related to emerging threats, known attack patterns, indicators of compromise (IOCs), and active vulnerabilities in the wild is collected, processed, and analyzed to understand the current threat landscape.
- Comprehensive risk scores: Instead of relying solely on CVSS (Common Vulnerability Scoring System) scores, RBVM tools take into account various factors such as asset criticality, exploitability, threat, and potential impact on business operations. By calculating risk scores that are tailored to the organization’s specific context, decision-makers can prioritize remediation efforts more effectively.
- Automation: Automation plays a crucial role in streamlining vulnerability management processes, reducing manual effort, and accelerating response times. Automated tools can perform tasks such as vulnerability scanning, risk assessment, and prioritization.
How Does Risk-Based Vulnerability Management Work?
RBVM solutions continuously identify assets, assess vulnerabilities, and prioritize risks. Humans play a critical role in this process. They’re responsible for interpreting the outputs from RBVM tools, making decisions about prioritizing vulnerabilities, planning remediation actions, and overseeing the overall vulnerability management process.
Let’s explore each step in more detail:
- Asset Identification: RBVM starts with identifying all assets within the organization’s network, including hardware, software, applications, and data. This is often done using asset discovery tools that scan the network and create an inventory of assets.
- Vulnerability Assessment: Once assets are identified, vulnerability assessment tools are used to scan for security vulnerabilities across the network. These tools check for known vulnerabilities in software, misconfigurations, and potential weaknesses in the network infrastructure.
- Risk Prioritization: RBVM prioritizes vulnerabilities based on their potential impact on the organization and the likelihood of exploitation. This involves assigning risk scores to vulnerabilities, considering factors such as severity, exploitability, asset criticality, and threat intelligence.
- Remediation Planning and Implementation: Based on the prioritized list of vulnerabilities, it’s over to the humans in the loop to develop remediation plans to address the most critical issues first and get to work.
Example of a Risk-Based Approach
To better understand how a risk-based approach works, let’s walk through an example scenario.
Imagine an organization that has just completed a vulnerability scan across its entire infrastructure. The scan identified hundreds of vulnerabilities across various applications and systems, ranging from low-severity misconfigurations to critical flaws that could allow remote code execution.
In a traditional vulnerability management approach, these vulnerabilities might be treated equally, or addressed in the order they were found, potentially wasting valuable time on issues that pose minimal risk to the organization.
However, with an RBVM approach, each vulnerability is prioritized based on several key factors, including asset criticality, exploit availability, exposure, existing security controls, threat intelligence, and more.
Based on this holistic assessment, the team assigns risk scores to each vulnerability, allowing them to focus first on the high-risk vulnerabilities that pose the greatest threat to the business. In this case, a critical vulnerability with a known exploit on a public-facing system would be addressed immediately, while lower-risk vulnerabilities are deprioritized for future remediation efforts.
How to Calculate Risk
Calculating risk in the context of vulnerability management is about more than just identifying weaknesses in your system. It requires a holistic approach, factoring in both the technical severity of vulnerabilities and their potential impact on your business.
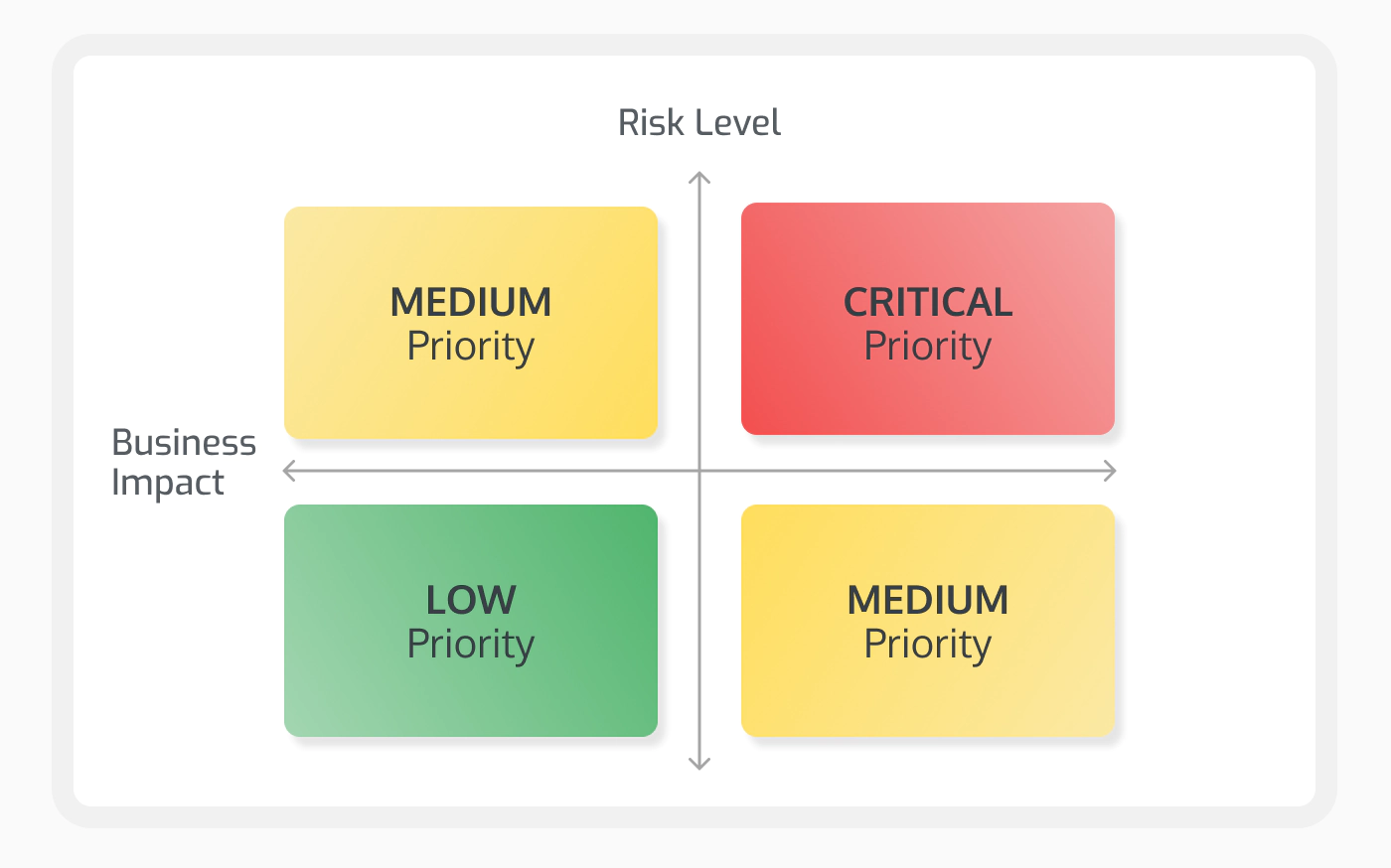
Here are the key criteria to consider when assessing risk:
- Vulnerability Severity: Start by measuring the technical severity of the vulnerability using the Common Vulnerability Scoring System (CVSS). This provides an objective way to assess how dangerous a vulnerability is based on factors like exploitability and impact.
- Asset Value: Consider how critical the affected asset is to your business. A vulnerability on a production server holding sensitive customer data is far more critical than one on a low-importance internal tool.
- Exposure Level: Analyze how exposed the system is to potential attackers. Public-facing systems, or those with remote access enabled, typically pose a higher risk compared to systems that are only accessible internally.
- Threat Intelligence Integration: Real-time threat intelligence can help you understand whether certain vulnerabilities are actively being exploited. If attackers are already targeting a specific vulnerability, its risk level increases significantly.
- Business Impact: Evaluate the potential consequences of a successful exploit, including financial loss, operational downtime, legal repercussions, and brand damage. A vulnerability’s risk may be heightened if the impact on business operations is severe.
- Likelihood of Exploitation: Finally, assess how likely it is that an attacker would exploit the vulnerability. This involves understanding the complexity of the exploit and the skills required to carry it out.
Real-world Example
Imagine a publicly accessible web server running an outdated version of a popular web application. The CVSS score for this vulnerability is 7.5, indicating high severity. However, the server hosts a critical customer-facing application, increasing the asset value. Threat intelligence indicates that attackers are currently exploiting this vulnerability in the wild. The server is exposed to the internet, and given the simplicity of the exploit, there’s a high likelihood that it could be successfully attacked.
Based on these factors, the risk score would be very high, requiring immediate remediation.
Risk-Based Vulnerability Management Benefits and Challenges
RBVM solutions represent a welcome change from legacy vulnerability management, which left security teams overwhelmed with alerts and unable to effectively prioritize. As a result of RBVM, organizations generally experience the following benefits:
- Reduced risk
- Enhanced productivity for security teams and developers
- Improved collaboration
- Enhanced compliance
But RBVM isn’t perfect. Despite the context these solutions offer, teams face a number of challenges, especially when turning insight into action. For example, RBVM lacks remediation tools and reporting capabilities. It focuses on existing vulnerabilities, and is dependent on risk scoring algorithms.
Risk Based Vulnerability Management Best Practices
Security and development teams face numerous challenges when it comes to vulnerability management. From managing an overwhelming number of vulnerabilities to aligning remediation efforts with business objectives, teams must navigate competing priorities. The key to success lies in adopting a risk-based approach that focuses on the vulnerabilities most likely to impact your organization.
Here are some best practices to help you optimize your vulnerability management efforts:
- Automate Vulnerability Scanning and Remediation: The volume of vulnerabilities is often too large for manual management. By automating both the discovery and remediation of vulnerabilities, teams can stay on top of emerging threats without drowning in alerts. Automation also ensures consistency and speed, reducing the time between identification and patching.
- Leverage Threat Intelligence: Not all vulnerabilities carry the same risk. Integrating threat intelligence feeds into your vulnerability management process allows you to focus on the vulnerabilities that are actively being exploited in the wild. This data-driven approach enables better prioritization and more informed decisions.
- Foster Cross-Team Collaboration: Security can’t operate in a silo. Development, security, and operations teams must collaborate closely to ensure that vulnerabilities are remediated effectively and without disrupting business operations. This means adopting DevSecOps practices and using tools that integrate seamlessly into existing workflows, like issue trackers and CI/CD pipelines.
- Implement Role-Based Access Control (RBAC): Even after vulnerabilities are identified, it’s essential to limit who can access systems with known issues. Implementing RBAC reduces the attack surface by restricting access to only those who need it, providing an additional layer of defense while vulnerabilities are addressed.
- Track Risk Reduction Metrics: Continuous improvement requires tracking your efforts over time. By measuring the reduction of risk based on vulnerability closure rates, time to remediation, and the impact on overall system security, teams can refine their processes and demonstrate tangible results to stakeholders.
These practices, when implemented correctly, allow teams to stay ahead of vulnerabilities, reduce risk, and keep their systems secure without sacrificing operational efficiency.
Importantly, tools like Application Security Posture Management (ASPM) further enhance these efforts by providing centralized visibility, continuous monitoring, and automated prioritization, making risk-based vulnerability management more efficient and scalable across the entire development lifecycle.
What Is Application Security Posture Management (ASPM)
ASPM is an evolution of Application Vulnerability Correlation (AVC), introduced by Gartner in 2023 to continuously manage the security of modern applications and improve overall risk posture.
ASPM platforms ingest and analyze data from multiple sources to offer a consolidated view of application security in a single place. It also offers security and development teams the tools they need to detect, correlate, prioritize, and remediate security vulnerabilities across the entire software development lifecycle (SDLC) before they’re integrated.
Key Components of ASPM
ASPM has a number of important components:
- Code-to-Cloud Visibility: ASPM provides a complete view of your SDLC, including your code, tooling, processes, and data from operational environments such as cloud platforms, containers, and physical infrastructure. ASPM continuously monitors and identifies vulnerabilities, tool misconfigurations, and other potential weaknesses.
- Vulnerability Scanning: ASPM tools regularly scan applications for known security issues. This involves using a wide range of native and third-party testing tools, such as secrets scanning, SCA, and SAST.
- Prioritization and Risk Management: ASPM allows organizations to prioritize and manage security risks associated with their applications. This helps security teams to make informed decisions about which vulnerabilities need to be addressed first based on their potential impact on the organization.
- Remediation and Mitigation: Once vulnerabilities are identified, ASPM provides guidance on how to remediate or mitigate them. This can involve suggesting code changes, configuration adjustments, or the application of security patches.
- Compliance Reporting: ASPM solutions help organizations with compliance reporting to maintain security policies, standards, and regulations such as SSDF, SOC 2, and ISO 27001.
- Reporting and Analytics: ASPM tools generate reports and analytics that help organizations understand the security posture of their applications over time. These reports can be used to track progress, demonstrate compliance, and make informed decisions.
| Component | Description | Benefit |
| Code-to-cloud visibility | ASPM provides a complete view of the SDLC, monitoring code, tooling, processes, and data from cloud platforms, containers, and physical infrastructure. It continuously identifies vulnerabilities, misconfigurations, and weaknesses. | Offers full visibility into the SDLC, enabling proactive identification of vulnerabilities and misconfigurations across environments. |
| Vulnerability scanning | ASPM tools regularly scan applications using both native and third-party testing tools, such as secrets scanning, SCA, and SAST, to identify known security issues. | Ensures regular identification of security issues, preventing known vulnerabilities from going unnoticed in the application. |
| Prioritization and risk management | ASPM helps organizations prioritize and manage application security risks based on potential impact, enabling informed decision-making about which vulnerabilities to address first. | Allows for efficient risk management, ensuring that high-risk vulnerabilities are addressed first to minimize potential impact. |
| Remediation and mitigation | ASPM provides guidance on how to remediate or mitigate vulnerabilities, suggesting code changes, configuration adjustments, or applying security patches. | Provides actionable insights for addressing vulnerabilities, speeding up remediation and improving security posture. |
| Compliance reporting | ASPM aids in compliance reporting, helping organizations maintain security policies and meet standards like SSDF, SOC 2, and ISO 27001. | Simplifies compliance processes, ensuring adherence to security regulations and avoiding |
| Reporting and analytics | ASPM generates reports and analytics that track application security posture over time, demonstrating progress, compliance, and informing decision-making | Offers insights into security posture, helping track improvements, demonstrate compliance, and inform long-term strategies. |
Complete vs. Incomplete ASPM
Importantly, there are key differences between what we call complete ASPM solutions and incomplete solutions, also known as standalone ASPM.
Complete ASPMs allow organizations to easily select and connect third-party tools, platforms plus they offer a comprehensive suite of native application security testing tools for SCA, SAST, IaC, secrets, etc.
Incomplete ASPMs usually only aggregate data from third-party sources. They often have no native AST scanners or very limited scanning capabilities.
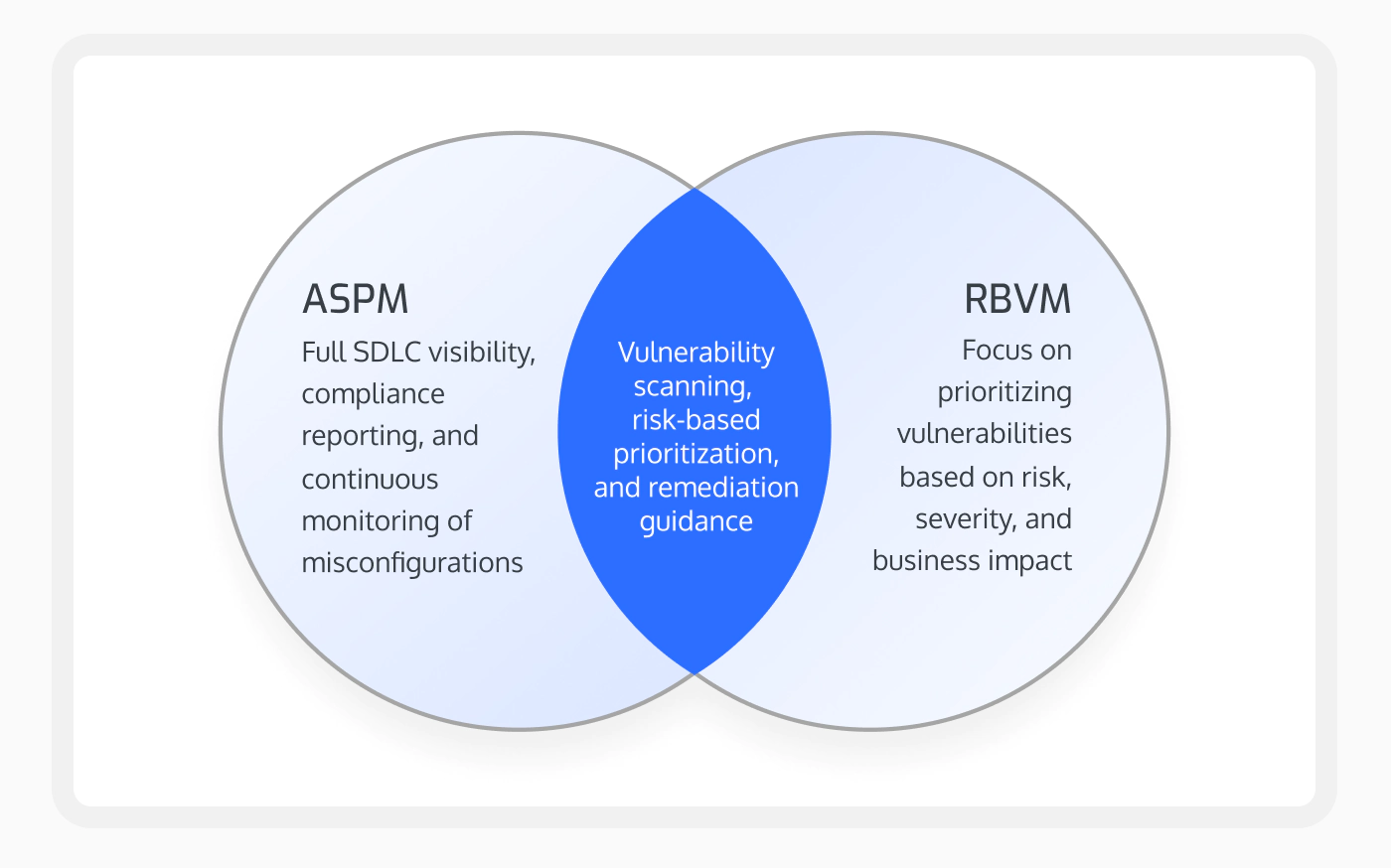
RBVM vs. Complete ASPM
Ultimately, both RBVM and complete ASPM solutions help security and development teams better allocate resources, improve productivity, increase collaboration, and reduce time to remediation. Likewise, both are focussed on context – understanding the relative risk of individual vulnerabilities within the context of your entire environment.
But these two methodologies differ drastically when it comes to their purpose, scope, and functionality.
The TLDR version? RBVM simply helps security teams and developers understand which existing vulnerabilities to prioritize based on risk. ASPM, on the other hand, focuses on proactively preventing vulnerabilities from making their way into your systems by prioritizing risks and providing the tools and automation needed to remediate them in real-time.
Purpose: RBVM vs. Complete ASPM
RBVM focuses on prioritizing existing security vulnerabilities in an organization’s systems, applications, and infrastructure based on their potential impact on the business. That’s it.
ASPM is geared towards continuously managing the security of modern applications throughout the software development lifecycle (SDLC). It provides a consolidated view of application security and offers key features and integrations that help teams prevent vulnerabilities from entering the software supply chain.
Scope: RBVM vs. Complete ASPM
While RBVM covers attack types and surfaces across applications, infrastructure, and the cloud, these tools are generally limited in their ability to detect and address complex attack vectors such as supply chain attacks.
ASPM focuses on application and pipeline security. Platforms in this category prevent vulnerabilities from entering your systems through third-party components or insecure coding practices by correlating data from multiple sources, prioritizing risk based on business impact, and giving developers the tools they need to take action fast.
Functionality: RBVM vs. Complete ASPM
RBVM tools scan systems for known vulnerabilities, generate high-level reports prioritizing those vulnerabilities, and generally include some features related to vulnerability management.
ASPM platforms leverage SCA, SAST, IaC, and secrets scanning tools to analyze code for security weaknesses and identify vulnerabilities in components (again, before integration). To reduce context switching and enable developers to reduce time to remediation, ASPM platforms tie vulnerabilities back to their owners and integrate directly with developer workflows.
Finally, unlike the high-level reports that RBVM tools produce, ASPM platforms offer robust reporting capabilities that make it easy for security teams to pinpoint exactly what’s driving the different types of vulnerabilities. Some also offer real-time executive dashboards that make it easier to communicate risk with other stakeholders, enabling more seamless management and remediation.
Should I Choose RBVM or ASPM?
As we’ve said, RBVM and ASPM are not one in the same; comparing these two approaches is like comparing apples and oranges. To understand which is right for your organization, you need to consider your unique requirements.
Choose RBVM for:
- Identifying exploitable weaknesses in existing systems
- Prioritizing remediation efforts
Choose ASPM for everything RBVM does plus the following:
- Preventing vulnerabilities from entering the system through third-party components or insecure coding practices
- Prioritizing vulnerabilities based on business risk, exploitability, and severity
- Enforcing security policies during development
- Promoting collaboration between developers and security teams
- Consolidating disparate tools in your AppSec stack
- Building out and automating developer workflows
- Robust, real-time visibility of risk across all components, tools, libraries, languages, CI/CD pipeline, cloud infrastructure, and more
Importantly, it’s not a matter of one or the other. Integrations between ASPM platforms like Cycode and RBVM solutions like Nucleus Security clearly demonstrate that ASPM and RBVM are better together.
Learn More About Cycode
Cycode is the leading Application Security Posture Management (ASPM) platform, providing peace of mind to its customers. Our complete ASPM platform scales and standardizes developer security without slowing down the business, delivering safe code, faster. Cycode delivers cyber resiliency through unmatched visibility, risk-driven prioritization, and just-in-time remediation of code vulnerabilities at scale. Cycode’s Risk Intelligence Graph (RIG), the brain behind the platform, provides traceability across the entire SDLC through natural language. As a purpose-built platform for developer security, Cycode delivers visibility, prioritization, and remediation of vulnerabilities across the entire SDLC.
Want to learn more about Cycode? Book a demo now.