IaC Security for Security
and Development Teams.
Prevent cloud misconfigurations and apply security standards to
Kubernetes, Terraform, CloudFormation, ARM & more.
{ drift protection }
Monitor and Keep Tabs
On Any Configuration Drift
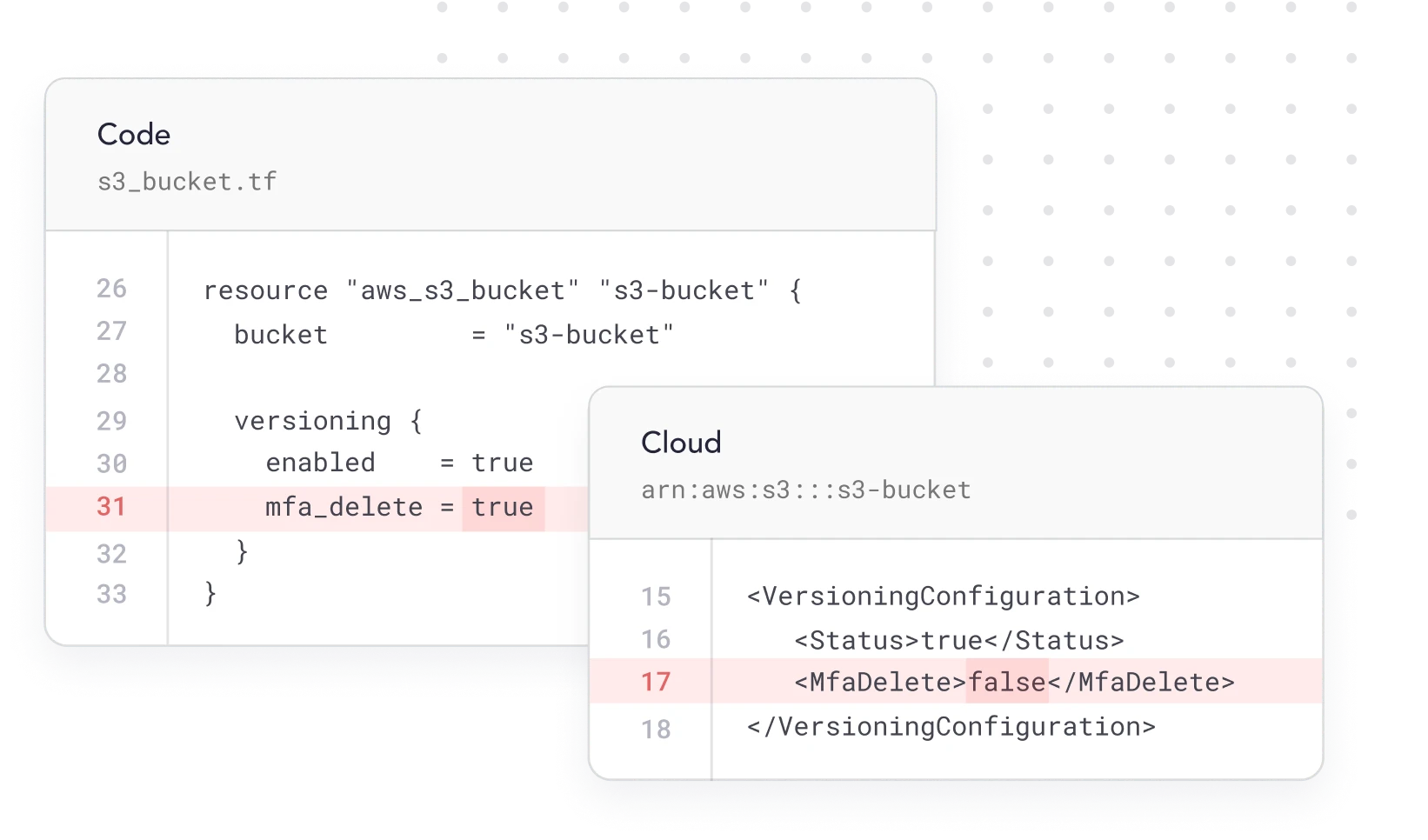
Continuously compare IaC configurations with those in production so you can identify drift. Find situations where configurations are no longer aligned and operating in an insecure way. Alert the right teams so these environments can be fixed.
Automated IaC security scanning
Alert your team on any misconfigurations
{ visibility }
Identify All Your
Cloud Misconfigurations
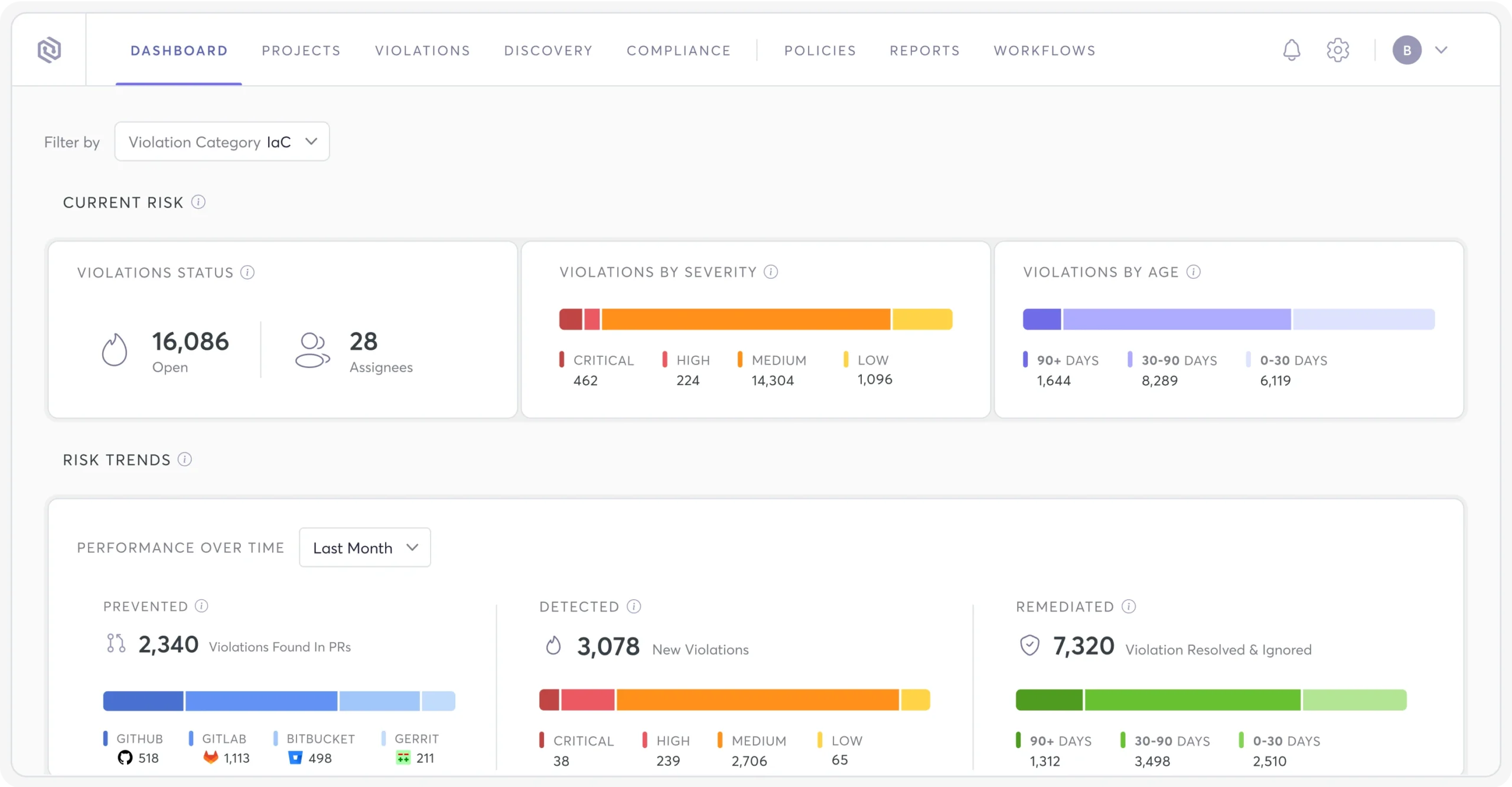
Let your devs easily find and fix IaC misconfigurations through Cycode’s continuous scanning. Uncover alerts for your team across hundreds of misconfiguration types such as publicly accessible storage buckets, non-encrypted critical data, weak password policies, non-rotated encryption keys and more.
Continuous scanning of every code change
Customizable detection logic

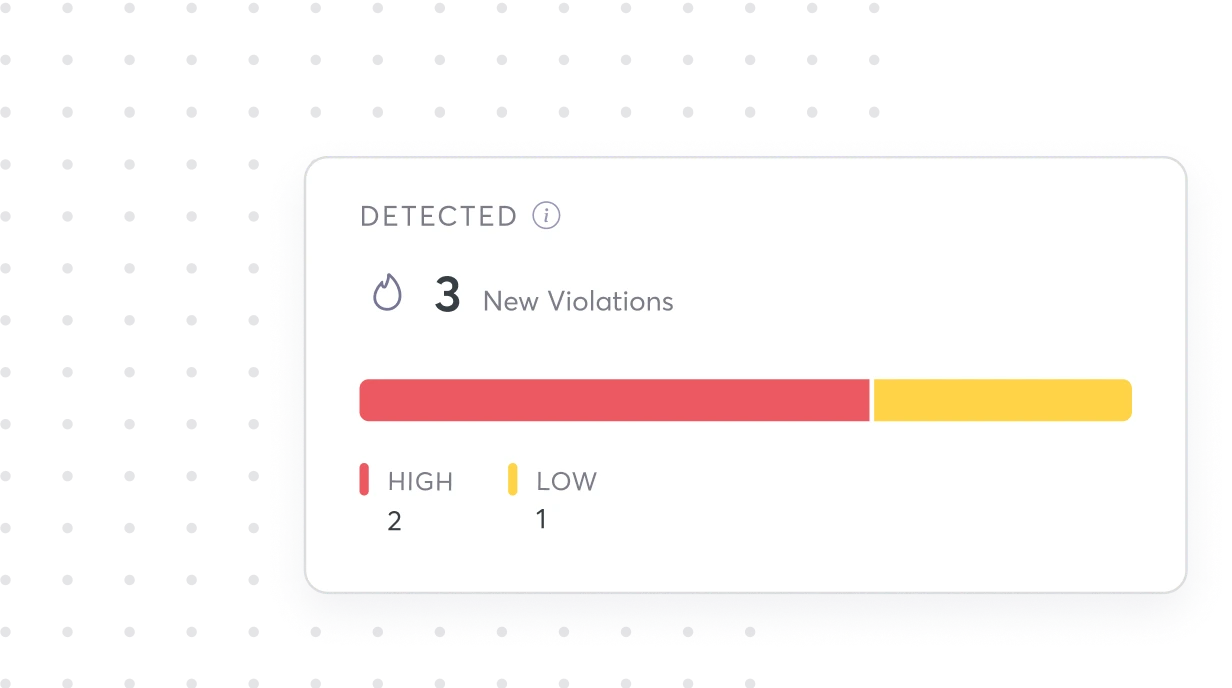
{ Prioritization }
Focus on the
Misconfigs that Matter Most
Prioritize your riskiest misconfigs so you can make sure nothing slips through the cracks and impacts the business.
Risk scoring engine
Impact & exposure level prioritization

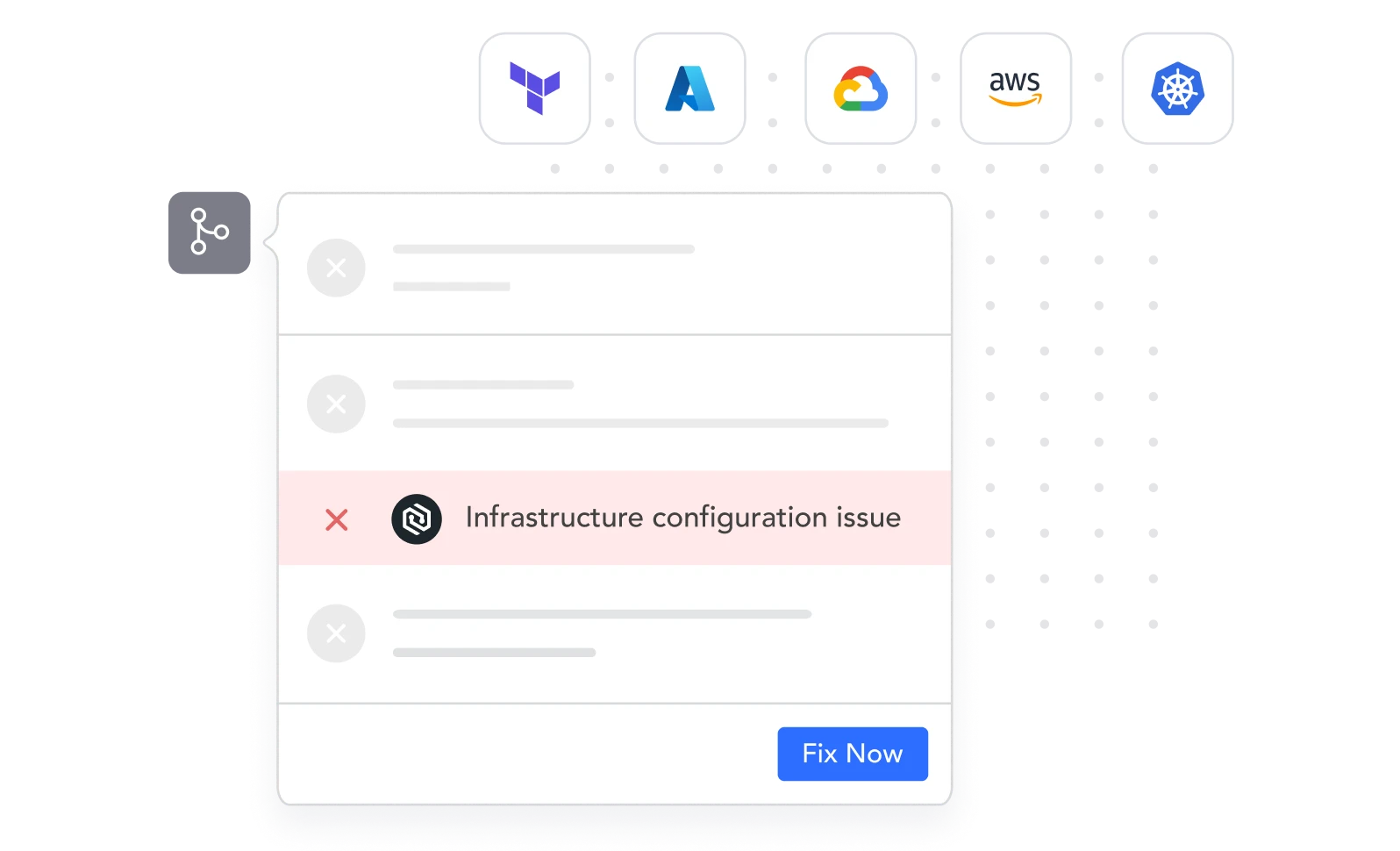
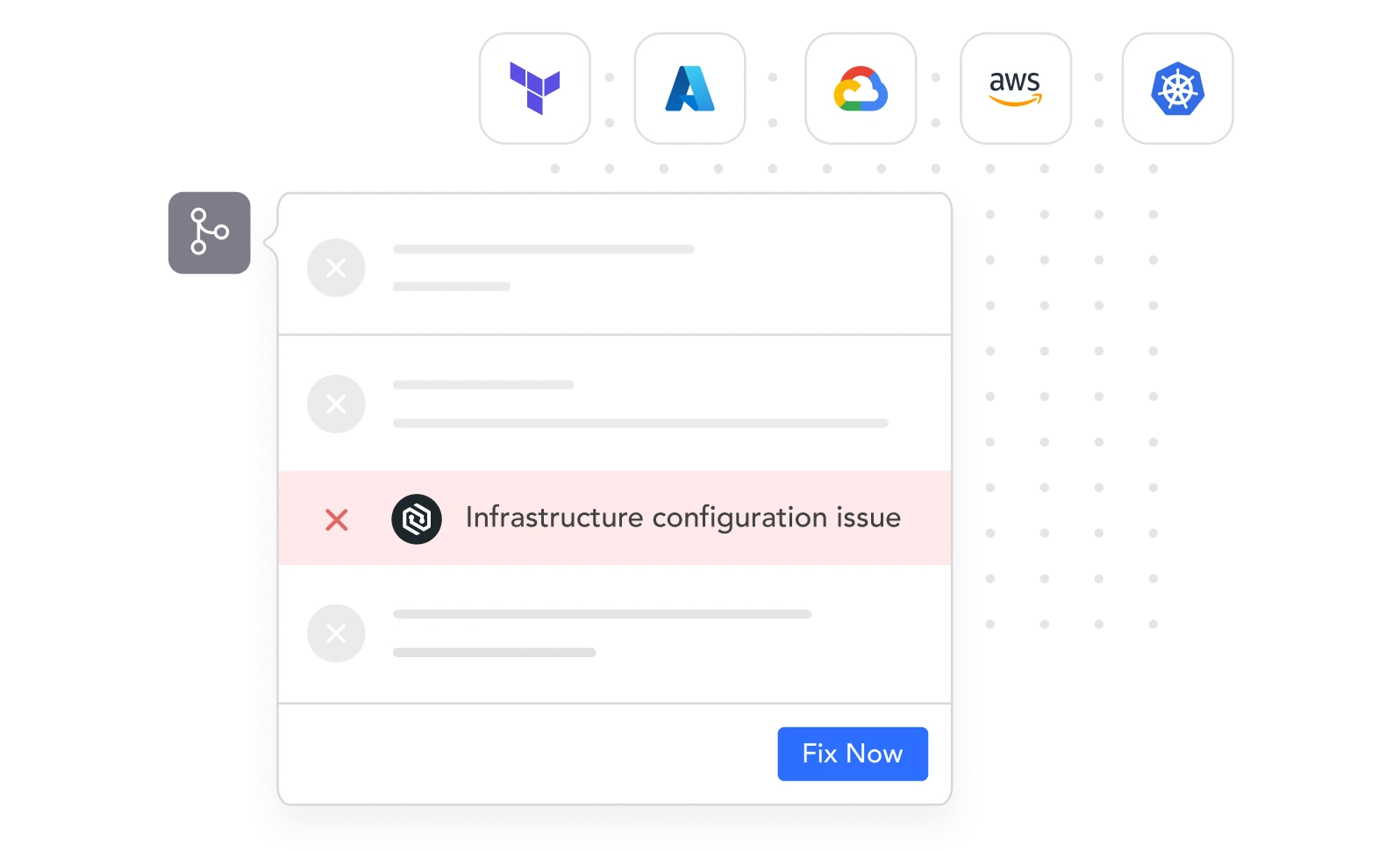
{ Developer Friendly }
Free Flowing IaC Scanning
within Developer Workflows
Scan new commits and merge requests for misconfigurations in compliance with NIST, CIS, or any custom built rules. If scans return IaC policy violations, Cycode automatically presents the results to developers and the code fix needed to remedy the issue.
Automated PR fixes
Self-serve development workflows
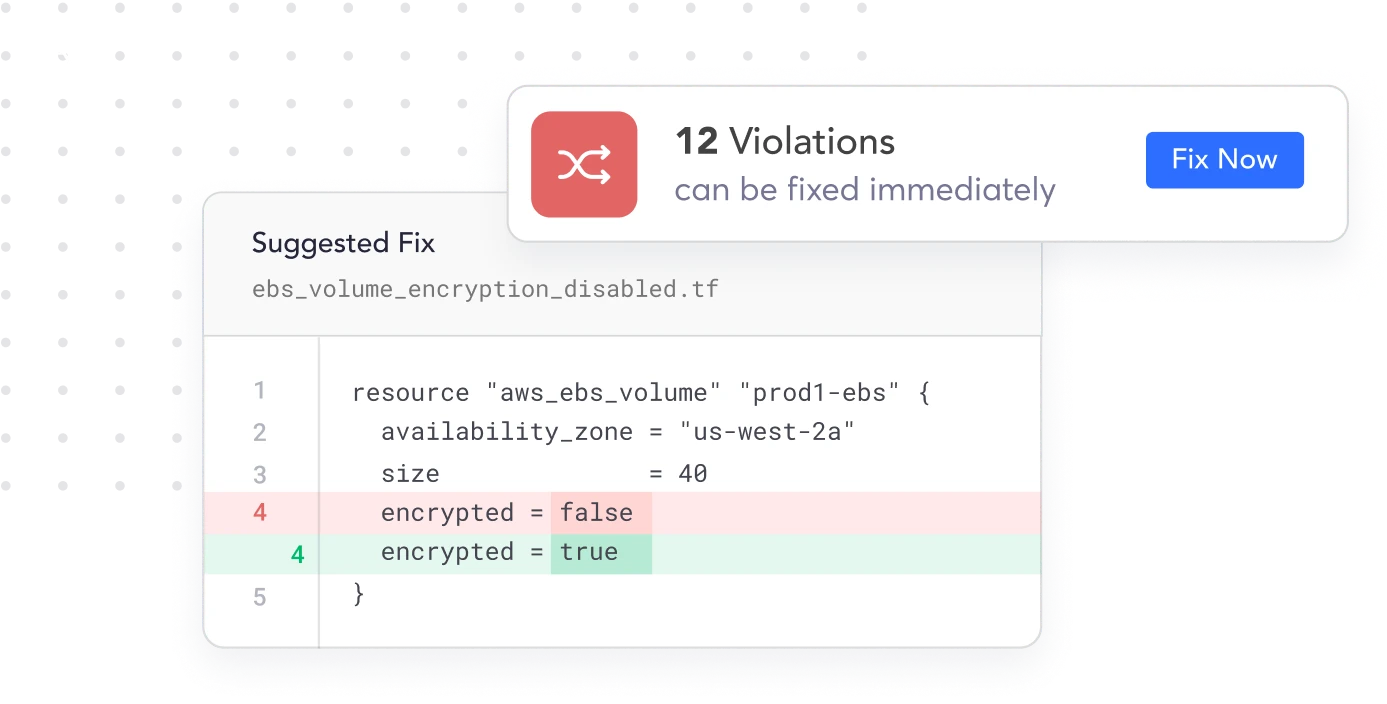
{ Remediation }
Automate Fixes with
All the Context You Need
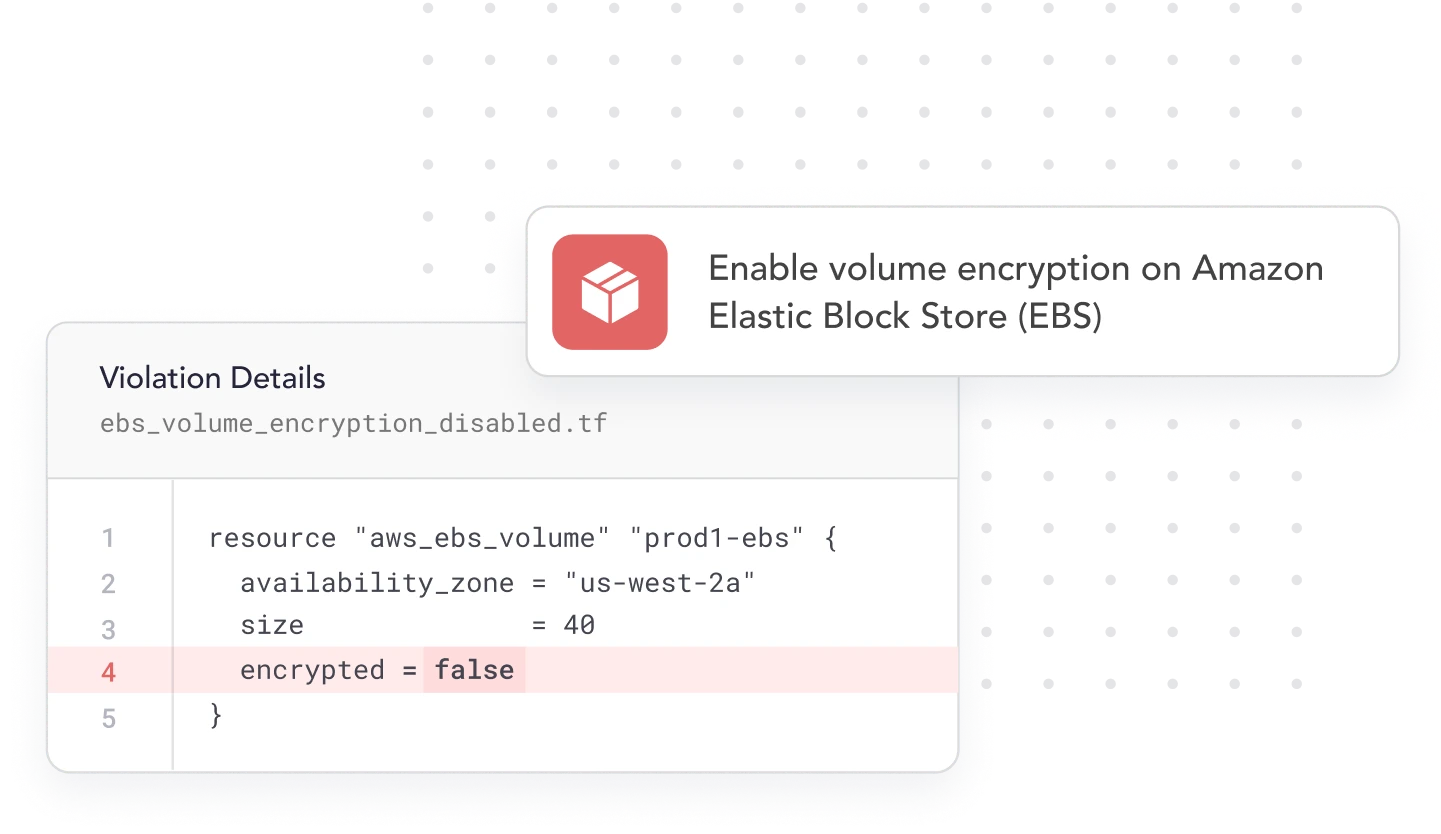
Automatically open pull requests with the code fix needed to remediate the specific misconfigurations detected in your IaC. This keeps your developers focused on efficiency and your infrastructure in line with best practices.
Auto-resolve remediated vulnerabilities
Remediation context and guidelines right within your developers IDE
Connect into the CI/CD workflow with Cycode CLI
Detect, block, and monitor vulnerabilities in the PR
Streamline remediation workflows through ticketing tool integrations

Frequently Asked Questions About IaC Security
What is IaC security?
Why is IaC security important?
What are the benefits of IaC security?
- Early risk detection:Catches misconfigurations before deployment.
- Automated compliance:Enforces security policies within development pipelines.
- Faster remediation: Fixes vulnerabilities in code before they reach production.
- Scalability: Ensures security across cloud environments as they evolve.
- Efficiency: Reduces manual security reviews through automation.
What is IaC scanning?
How does IaC security work?
- Automated scanning: Identifies misconfigurations in IaC files.
- Policy enforcement: Ensures compliance with security standards (CIS, NIST, etc.).
- Secret detection: Prevents credential leaks in code.
- Drift detection: Monitors infrastructure for unauthorized changes.
- Remediation automation: Fixes issues before deployment without manual effort.
 Solution Brief
Solution Brief