CircleCI was breached. If you are using this tool:
- Immediately rotate all stored secrets and environment variables in CircleCI. These secrets are the holy grail for attackers targeting CI systems and may lead to accessing code repositories, package registries, cloud environments, and more.
- Review internal logs of systems related to your CircleCI secrets for unauthorized access from December 21, 2022, through January 4, 2023, or the date you rotated the secrets in CircleCI.
What Happened?
CircleCI, a continuous integration and delivery platform, has recently issued a warning to its users about a security breach that occurred beginning December 21, 2022, through January 4, 2023. The company has stated that an unauthorized third party was able to gain access to user accounts and associated data.
Upon discovering the breach, CircleCI immediately began an investigation and took steps to secure its environment. The company is confident at the moment that there are no unauthorized actors active in its system. The company has also invalidated all Project API tokens used to access the user environment and recommends all users rotate their secrets, such as API keys and SSH keys.
What Should You Know?
CircleCI secrets 101
CircleCI Secrets are environment variables that are encrypted and stored securely in the CircleCI platform. They can be used to store sensitive data, such as API keys or passwords, that need to be accessed by a CircleCI workflow. Secrets are stored in the context of a project and can be accessed by any job within that project that has the appropriate permissions. Secrets are encrypted at rest and are not accessible to anyone without the necessary permissions.
There are various ways to define secrets within the CircleCI ecosystem as can be seen in the CircleCI documentation:
- Environment variables declared inside a shell command in a run step.
- Environment variables declared with the environment key for a run step.
- Environment variables set with the environment key for a job.
- Context environment variables (assuming the user has access to the context).
- Project-level environment variables set on the Project Settings page in the web app.
What Should You Do?
As per the warning issued by CircleCI, it is recommended to “Immediately rotate any and all secrets stored in CircleCI. These may be stored in project environment variables or in contexts.”
You should rotate the secret value of each of the found secrets. Once the secrets are rotated, you should make sure they weren’t used in an unexpected or suspicious way. This is the second action item CircleCI recommended.
How Cycode Can Help
- Cycode’s platform is able to Identify if you are using CircleCI by inspecting your repository webhooks:
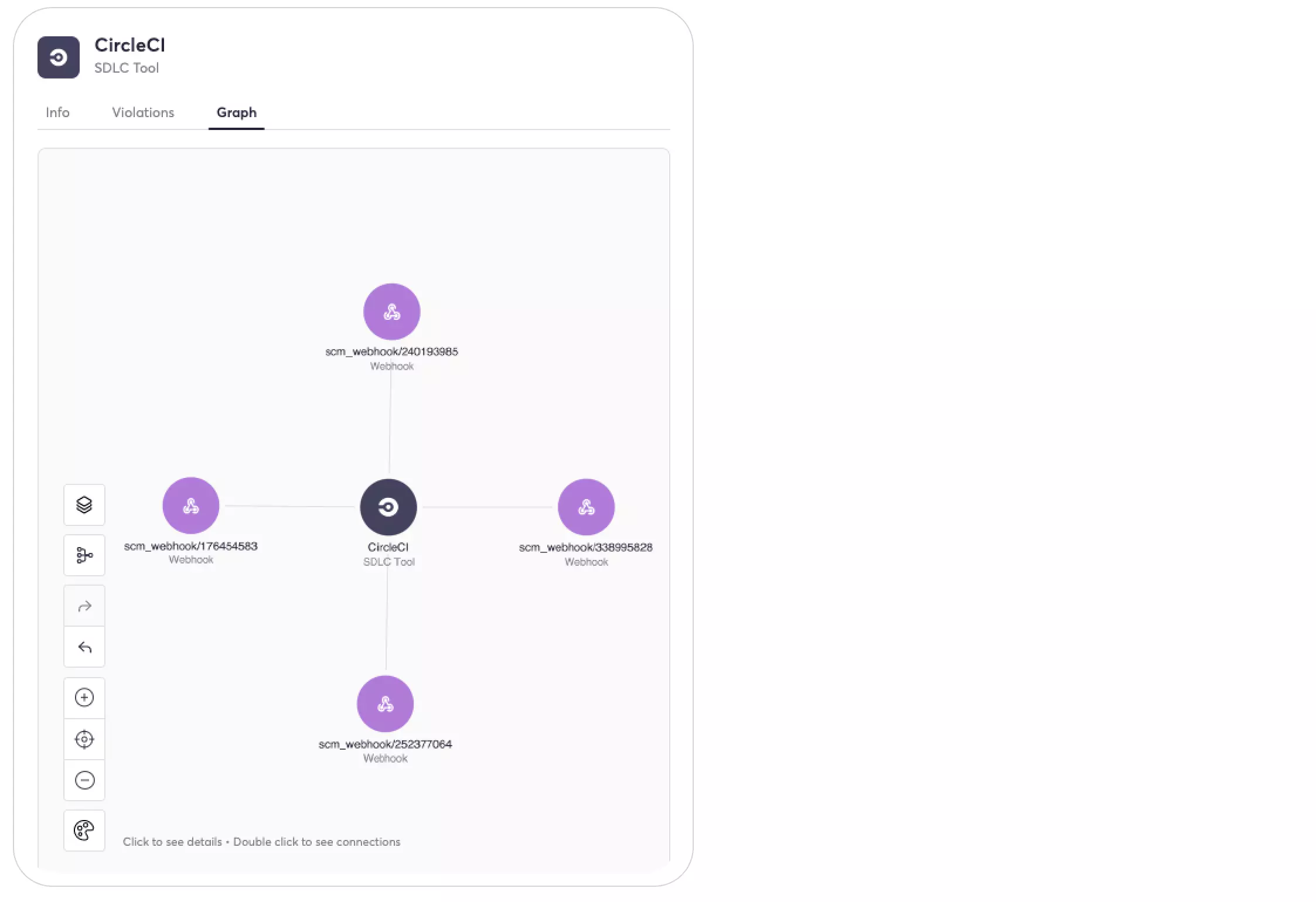
- Once you’ve integrated CircleCI with our platform, you can view all CircleCI-related secrets in our knowledge graph:
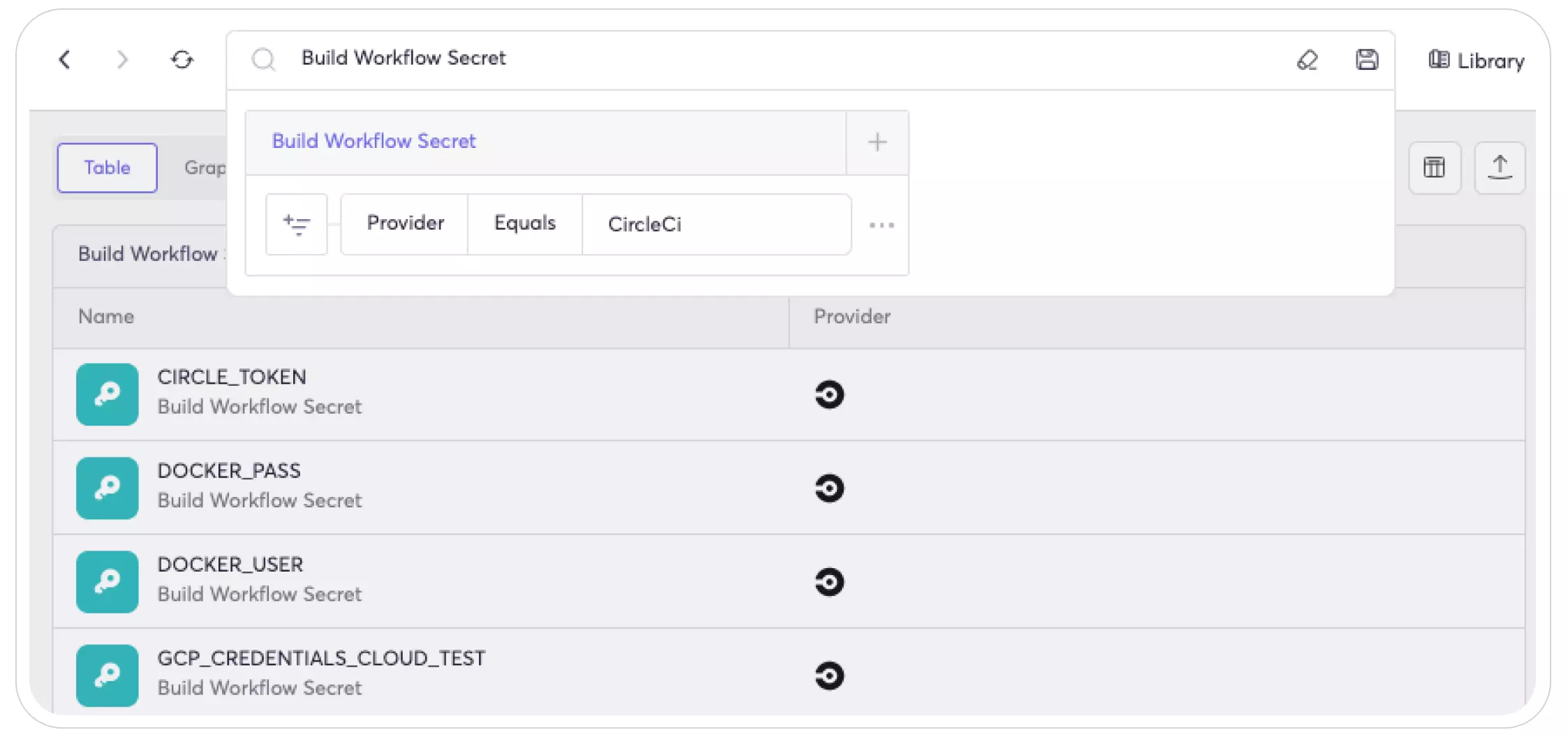
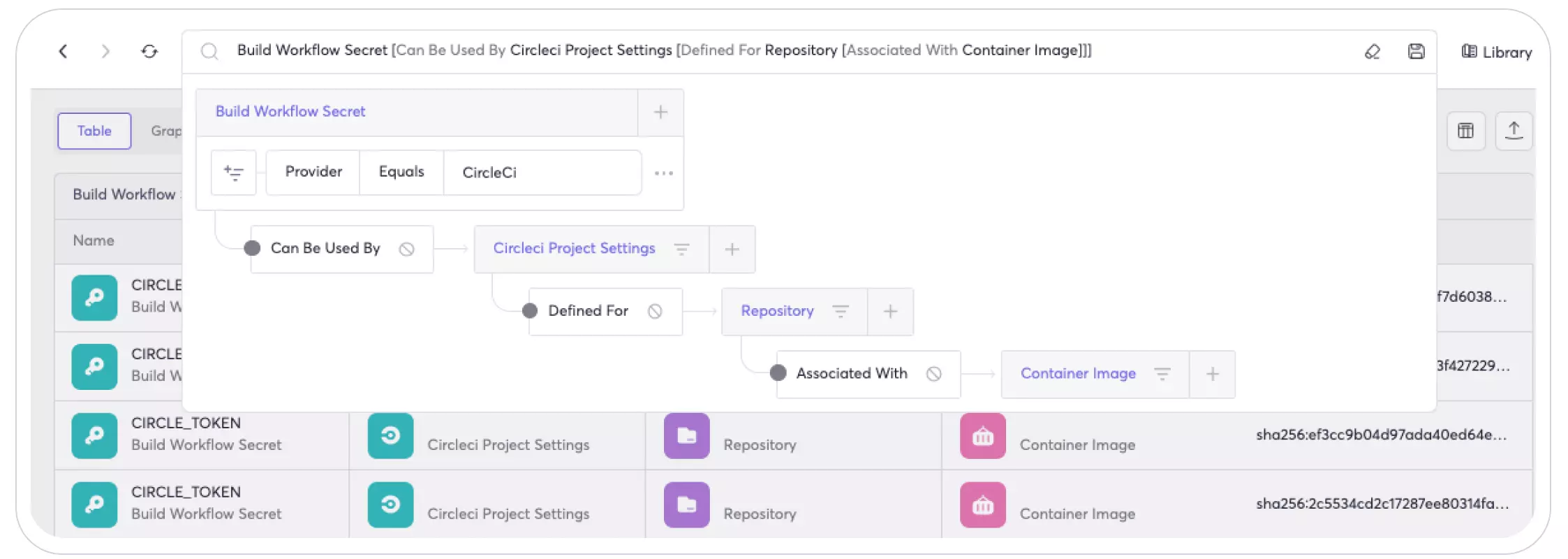
- You can then assess the risk of each secret by understanding how it relates to your SCM repositories, container registries, and production workloads:
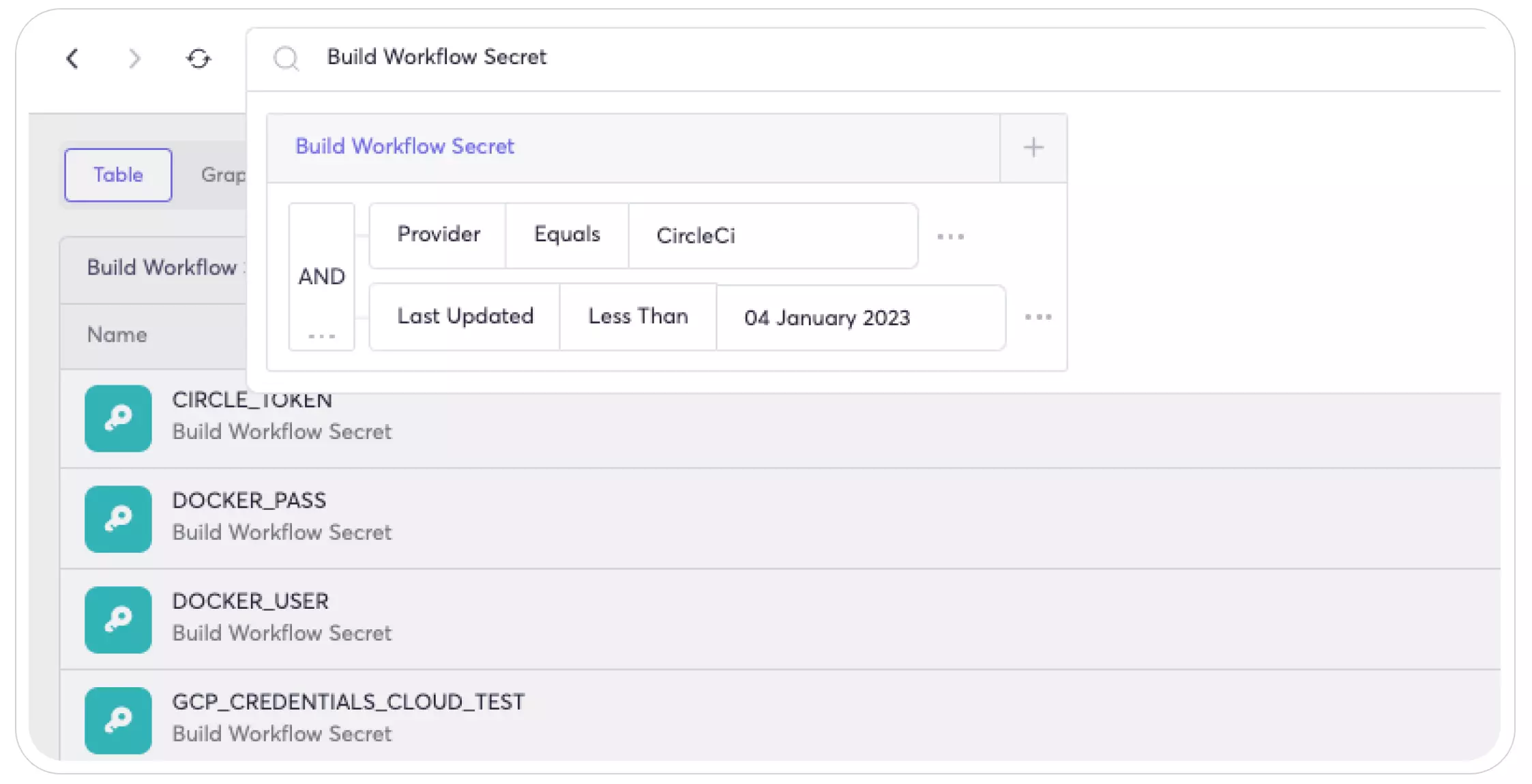
- After rotating the secrets, you can use Cycode to detect secrets that were not rotated after January 4, 2023 to ensure no secrets were missed:
- Finally, Cycode can help you harden the configuration of your CircleCI instance to better secure stored secrets, for example, identify secrets that are passed to forked pull requests. This enables developers with low privileges to create a fork of a repository and then steal the secrets through a PR in the forked repository. Using Cycode, you can detect this issue and disable this configuration if not necessary:
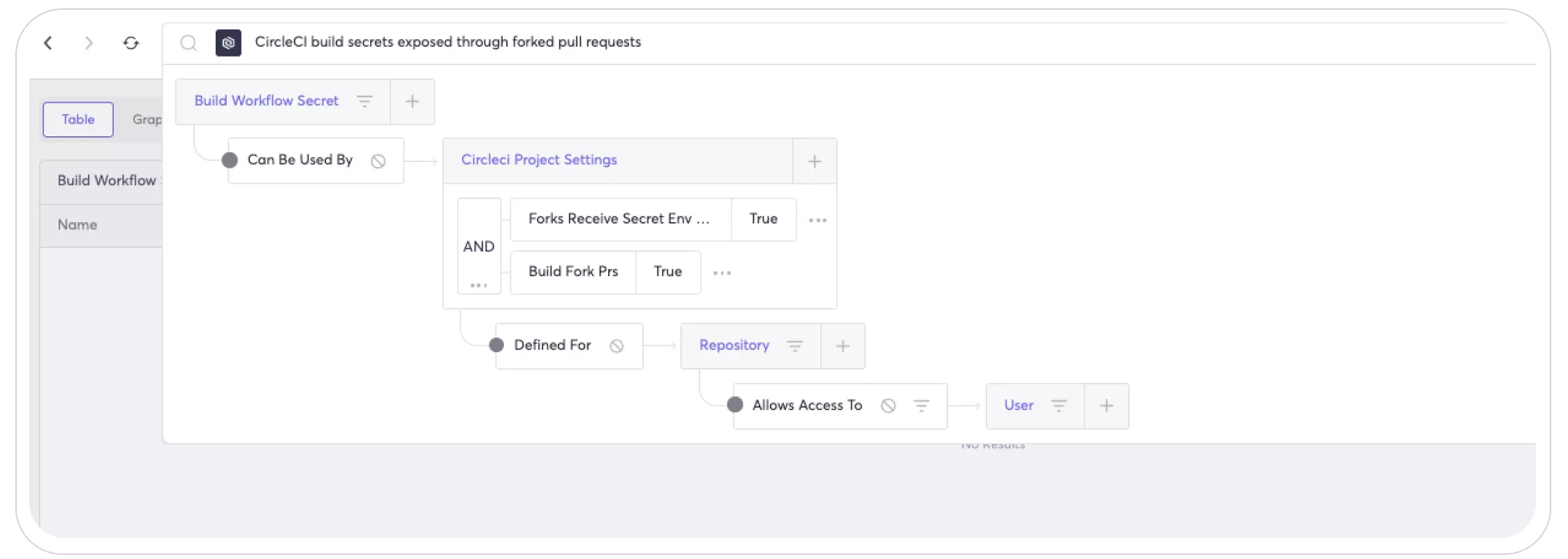
You can read more about this threat in our previous blog “All Roads Lead to Build Secrets” where we detail some of the threats around build tools secrets such as Github Actions and CircleCI.
As we adopt new technologies that improve our development speed and agility, it is important to understand the risks associated with these tools.
If you need support securing your software supply chain tools and infrastructure, we are here to help. For more help, schedule a demo today.


