GitLab, a popular web-based Git repository management tool, has recently patched a critical vulnerability that allows attackers to attach malicious runners to any project on the instance. This vulnerability is caused by a flaw in a GraphQL endpoint and can be exploited by any GitLab user account under certain conditions. Once attached, the malicious runner can compromise the build process, allowing the attacker to gain access to sensitive data, environment variables, as well as inject malicious code.
In this paper, we provide a short analysis of the vulnerability, its impact, and the recommended steps for GitLab users to secure their systems.
Understanding GitLab Runners
GitLab runners are responsible for executing continuous integration (CI) and continuous delivery (CD) tasks. GitLab has three types of runners – project runners, shared runners, and group runners. Each type of runner has a purpose and scope:
- Project runners are specific to a single project and are registered by a project maintainer or owner. They are used to run jobs only for the project that registered them.
- Shared runners are available to any project in the GitLab instance and can be used by anyone with access to the GitLab instance. Shared runners are registered by an administrator and are used by multiple projects.
- Group runners are used to run jobs for all projects in a group. They are registered by a group owner or maintainer and are available for any project within the group.
Regardless of the type of runner, each GitLab runner has the same goal – to run a CI process that executes commands based on triggers and events. The runner may hold secrets and API access tokens necessary to complete the build process. For example, GitLab Runner can test the source code for vulnerable dependencies, build a docker image, and deploy it to an AWS EKS cluster.
What is GraphQL?
GraphQL is a query language for APIs developed by Facebook in 2012. In a GraphQL API, the client sends a request to a single GraphQL entry point that accepts queries or mutations.
The server-side implementation of GraphQL involves defining a schema that describes the available data and operations as well as a resolver that maps the client’s query to the actual data source. GraphQL also enables clients to get multiple resources in a single request, reducing the number of requests needed to fetch data.
The vulnerability
Under certain conditions, an attacker can use a GraphQL endpoint to attach a malicious runner to an instance. Once attached, the build process will run under the malicious runner. This may allow attackers to gain access to sensitive data such as DB access keys, container registry tokens, and more. It also allows attackers to inject malicious code into the build process, compromising the integrity and security of the entire system.
Affected Versions
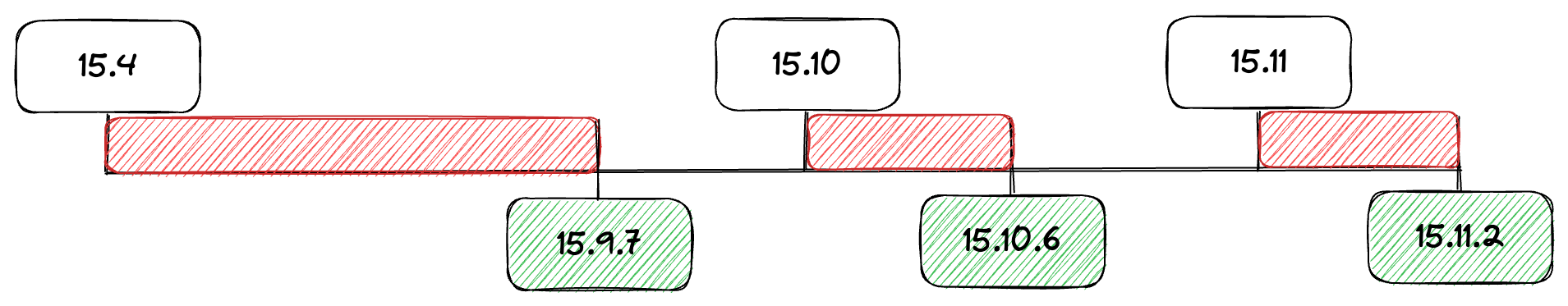
The versioning system used by GitLab is Semantic Versioning and is represented as(Major).(Minor).(Patch). Versions starting from 15.4 before 15.9.7, 15.10 before 15.10.6, and 15.11 before 15.11.2 are affected by this vulnerability. Both the Commercial Edition and Enterprise Edition are vulnerable. The patched version has already been implemented on GitLab.com.
Recommendations for GitLab Users
Users of GitLab Commercial or Enterprise are strongly advised to update the patched versions as soon as possible. GitLab has released patches for this vulnerability at versions 15.9.7, 15.10.6, and 15.11.2.
It’s important to note that GitLab makes vulnerabilities public on their issue tracking page 30 days after the patch. Unpatched versions of GitLab will remain vulnerable to this attack and will be public to everyone to test and exploit on unpatched instances.
How Cycode Can Help
These recently disclosed critical vulnerabilities pose a significant risk to organizations. With Cycode’s AppSec platform, you can detect and remediate known vulnerabilities such as these. The Cycode platform makes AppSec tools better through its Knowledge Graph, which provides a complete context of the SDLC to improve accuracy and reduce mean-time-to-remediation (MTTR).
Want to learn more about how Cycode provides visibility, security, and integrity across all phases of the SDLC? Book a demo now.




