Secrets Detection and Scanning
by Cycode
Continuously scan, detect and remediate every hidden secret across your
SDLC and developer productivity tools
{ visibility }
Scan Code & Beyond to
Find All Your Exposed Secrets
Secrets hide in a lot of places that aren’t just source code. Make sure you find and fix them all.
AI powered secrets detection
Extend secrets detection across ticketing, documentation, and messaging tools
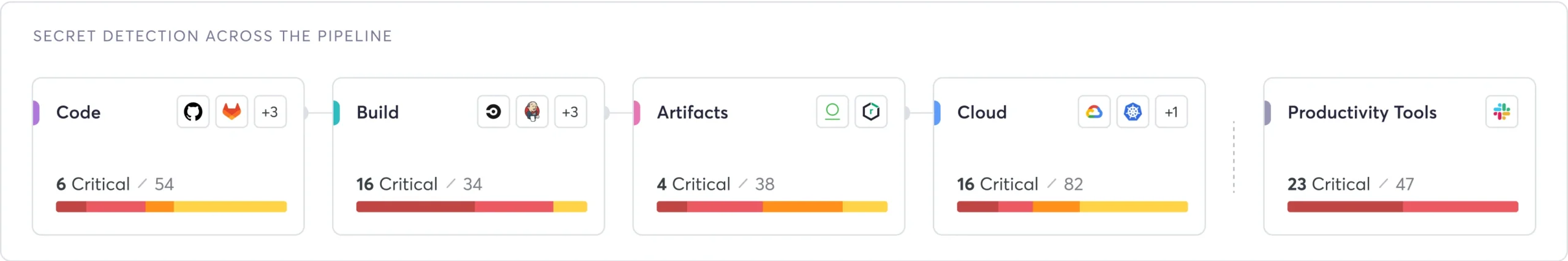
Identify secrets across the SDLC
Pre-defined rules to detect secrets for both known and proprietary services
{ Prioritization }
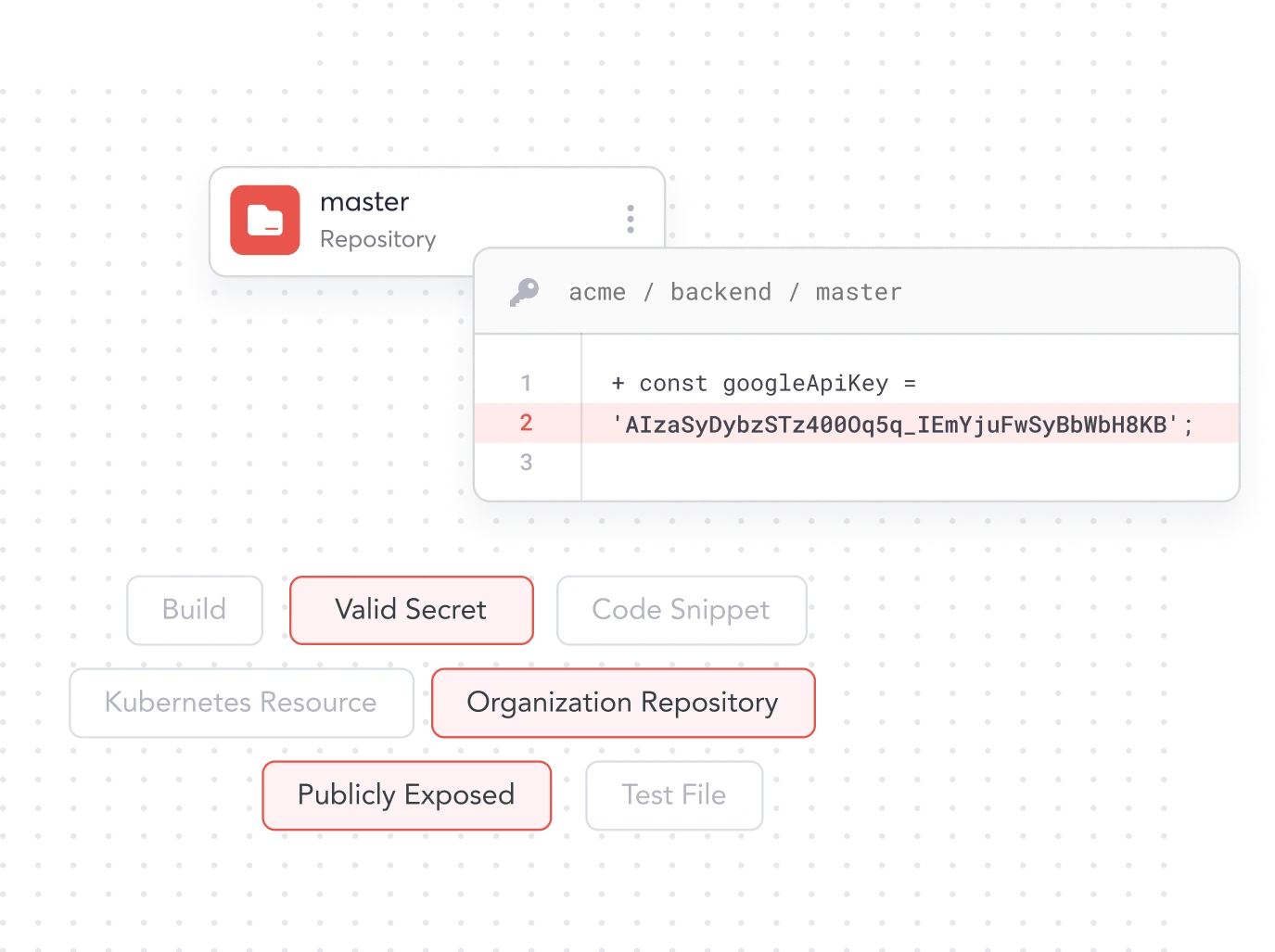
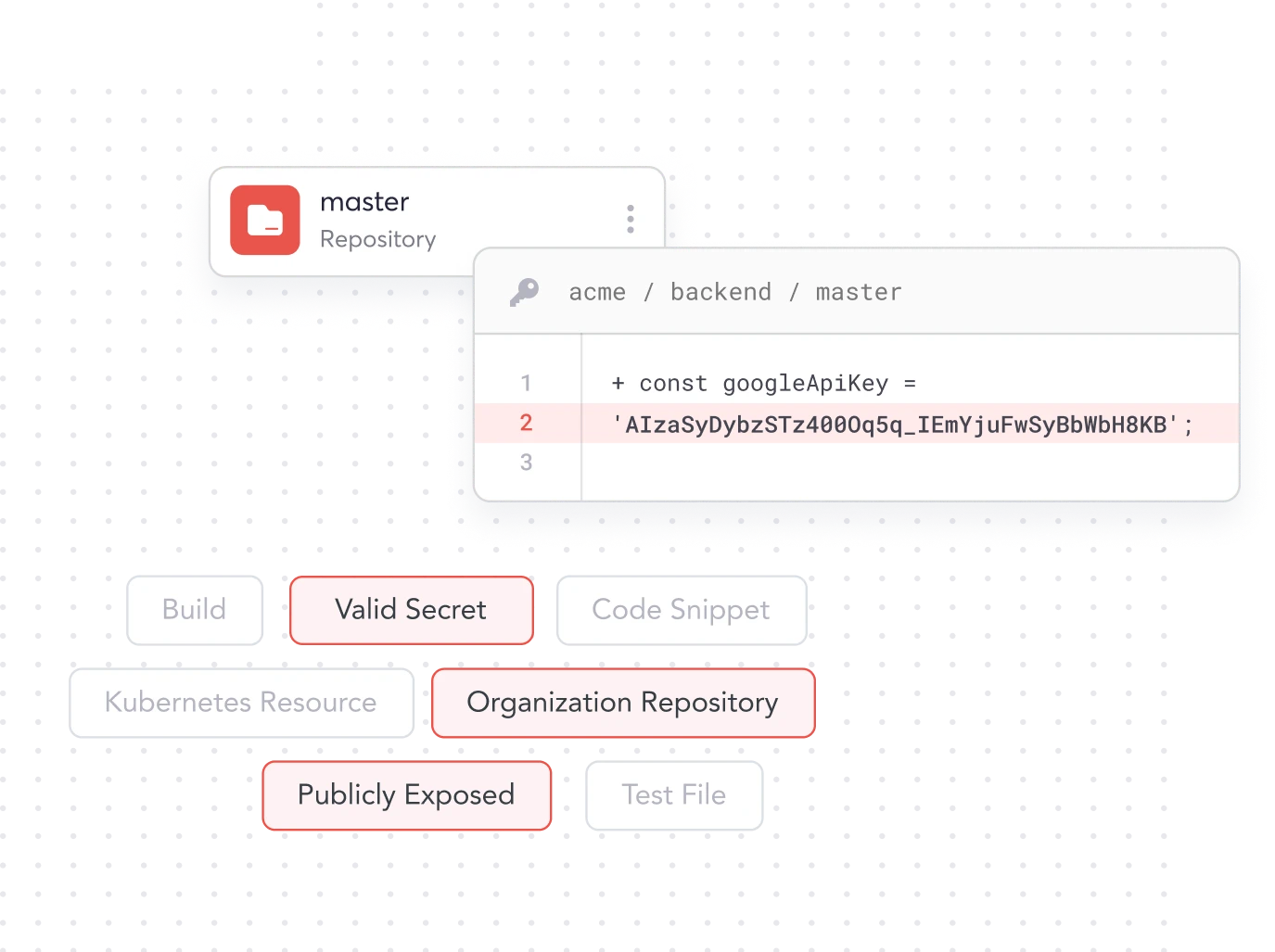
Not All Secrets
Are Created Equal
Prioritize your riskiest secrets so you can fix your biggest threats first.
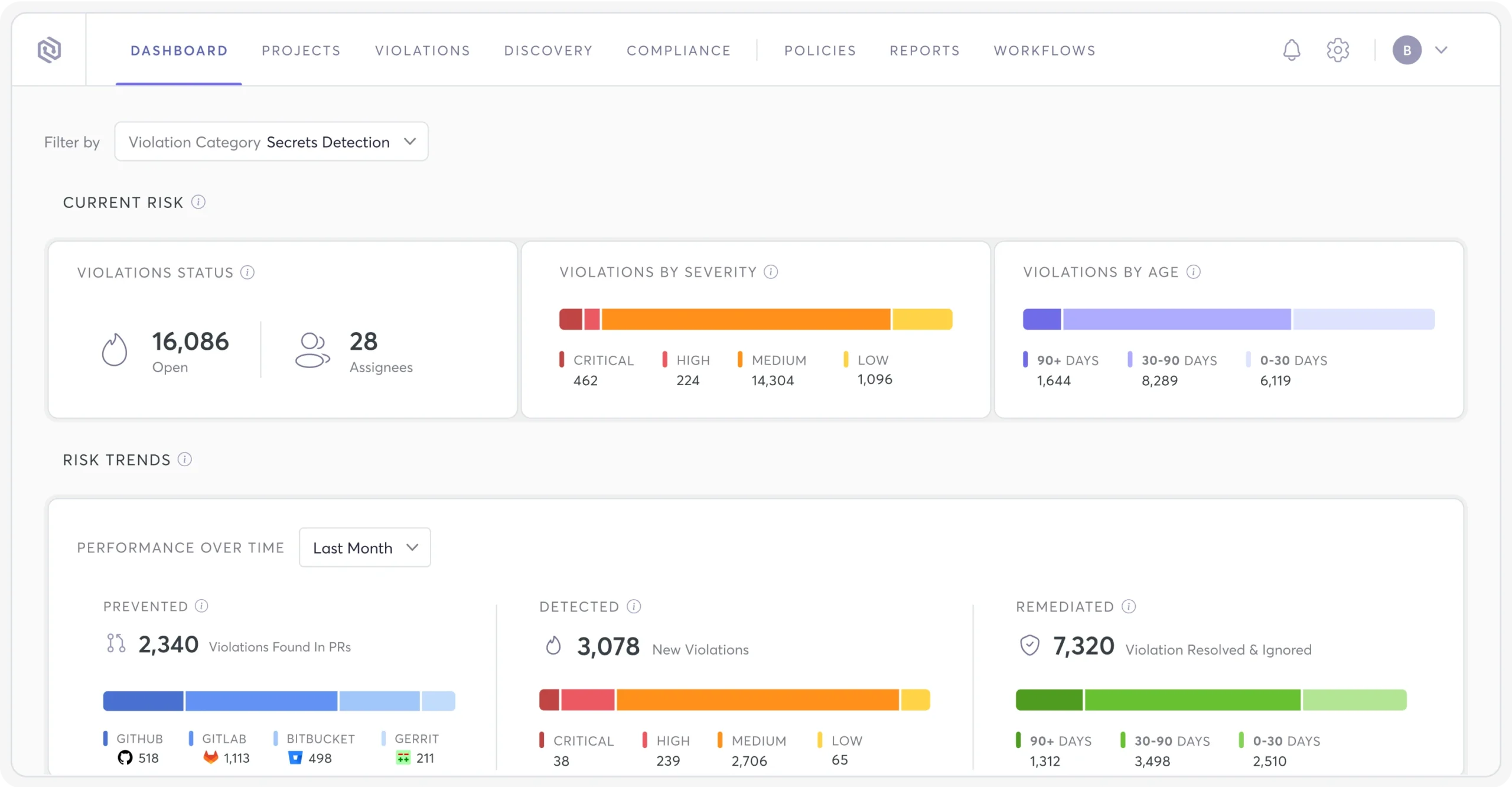
Validate the status of your secrets activity
Secrets risk scoring based on potential impact and exposure
Leverage code context to reduce any false detections
Monitor secrets exposure in private or public repos
{ Remediation }
Prevent Secrets Exposure with
Developer Friendly Workflows
Enable your developers to detect and remove hardcoded secrets directly within their existing tools, enhancing security without disrupting workflow.
Detect and remediate right within the IDE
Streamline remediation workflows through ticketing tool integrations
Auto-resolve remediated secrets
Connect into the CI/CD workflow with Cycode CLI
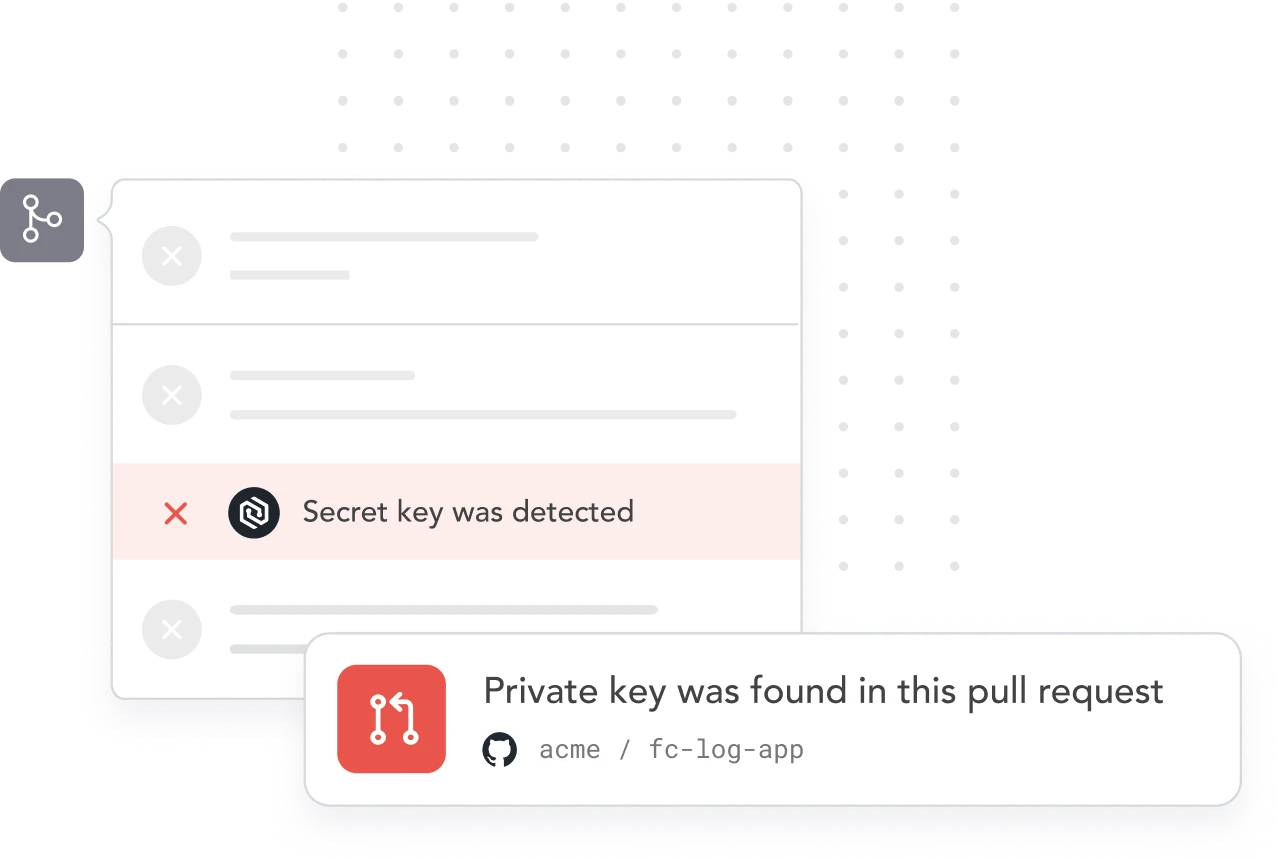
Detect, block, and monitor secrets in the PR