Secure Your Infrastructure
in Each Phase of the SDLC

Development
Harden your source control management systems (SCM),
find secrets, leaks and prevent code tampering

CI/CD
Scan your CI/CD settings and Infrastructure-as-Code (IaC)
for security misconfiguration

Cloud
Identify drift between production systems IaC configurations and prevent source code tampering
One Platform For SDLC Security,
Governance & Integrity
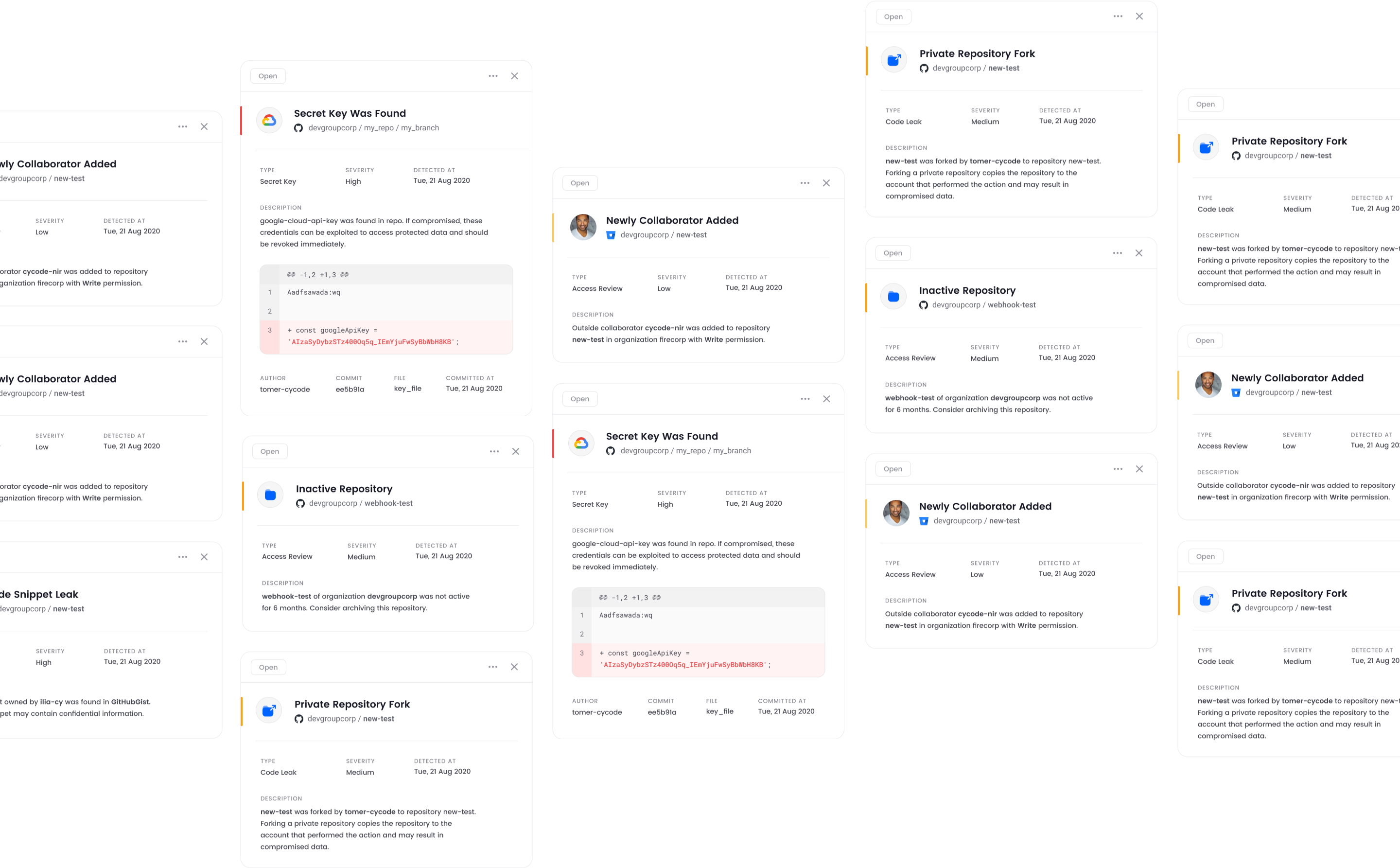
Code leak
Prevent Theft & Leakage of Your
Most Valuable Asset: Code
Stop developers from inadvertently exposing proprietary code in public repositories, fingerprint code assets and proactively identify exposure on public sites.
Access & Authorization
A Single Source of Truth for
DevOps Pipeline Governance
Inventory assets, enforce security policies, and easily demonstrate compliance across all your DevOps tools and infrastructure, both in the cloud and on-premises.
IaC Scanning
Secure Infrastructure-as-Code (IaC)
Configurations & Production Systems
Scan IaC for security misconfigurations and ensure compliance between defined IaC configurations and production infrastructure.
SECRETS
Prevent Developers from
Writing Secrets into Code
Scan every commit or pull/merge request for hard-coded secrets and prevent them from reaching
the master branch across all SCMs and programming languages.
Free Code Repo
Risk Assessment
- Search public repos for your proprietary source code
- Find hard-coded secrets such as tokens, keys & credentials
- Audit access & governance policies to demonstrate compliance
- Identify redundant access & stale accounts
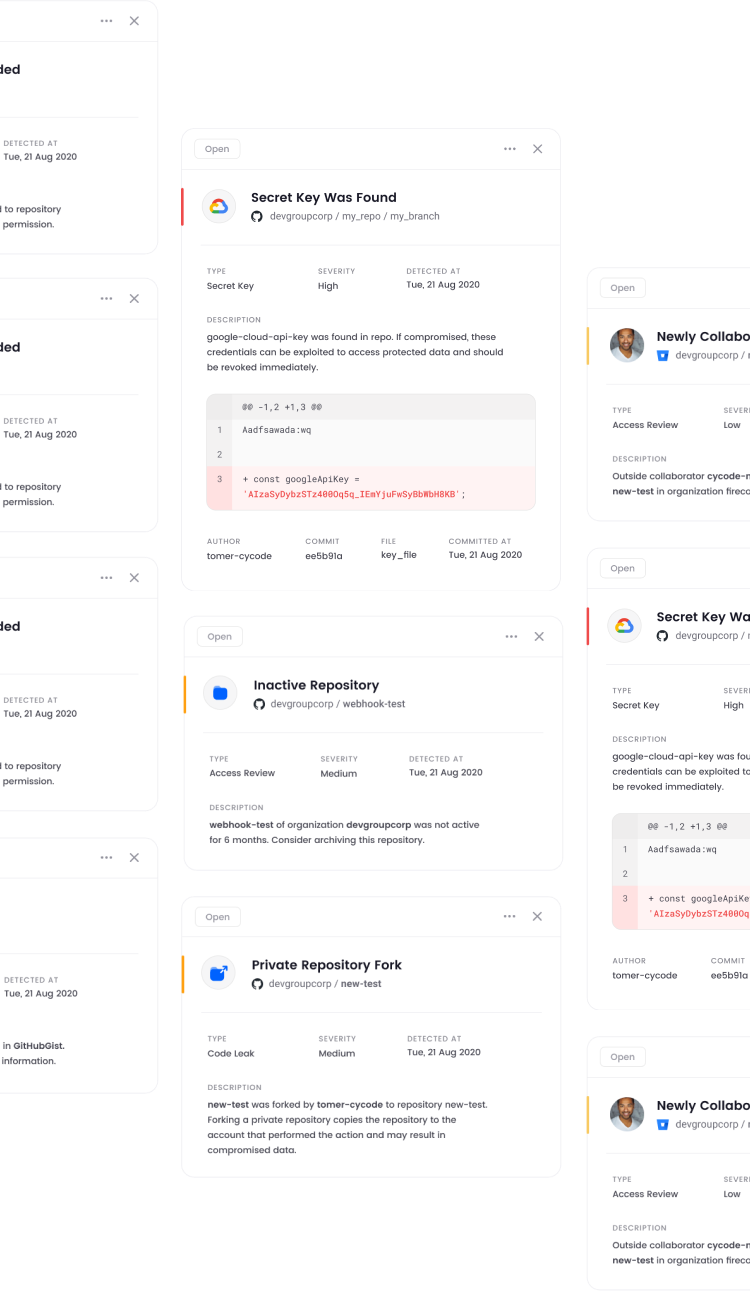
Uncover Contextual Insights
By correlating events across the SDLC Cycode’s knowledge graph identifies code tampering, prioritizes remediation, and reduces false positives.
Manage continuously
to secure at the speed of DevOps
Total visibility for all your development infrastructure without slowing down feature release velocity.
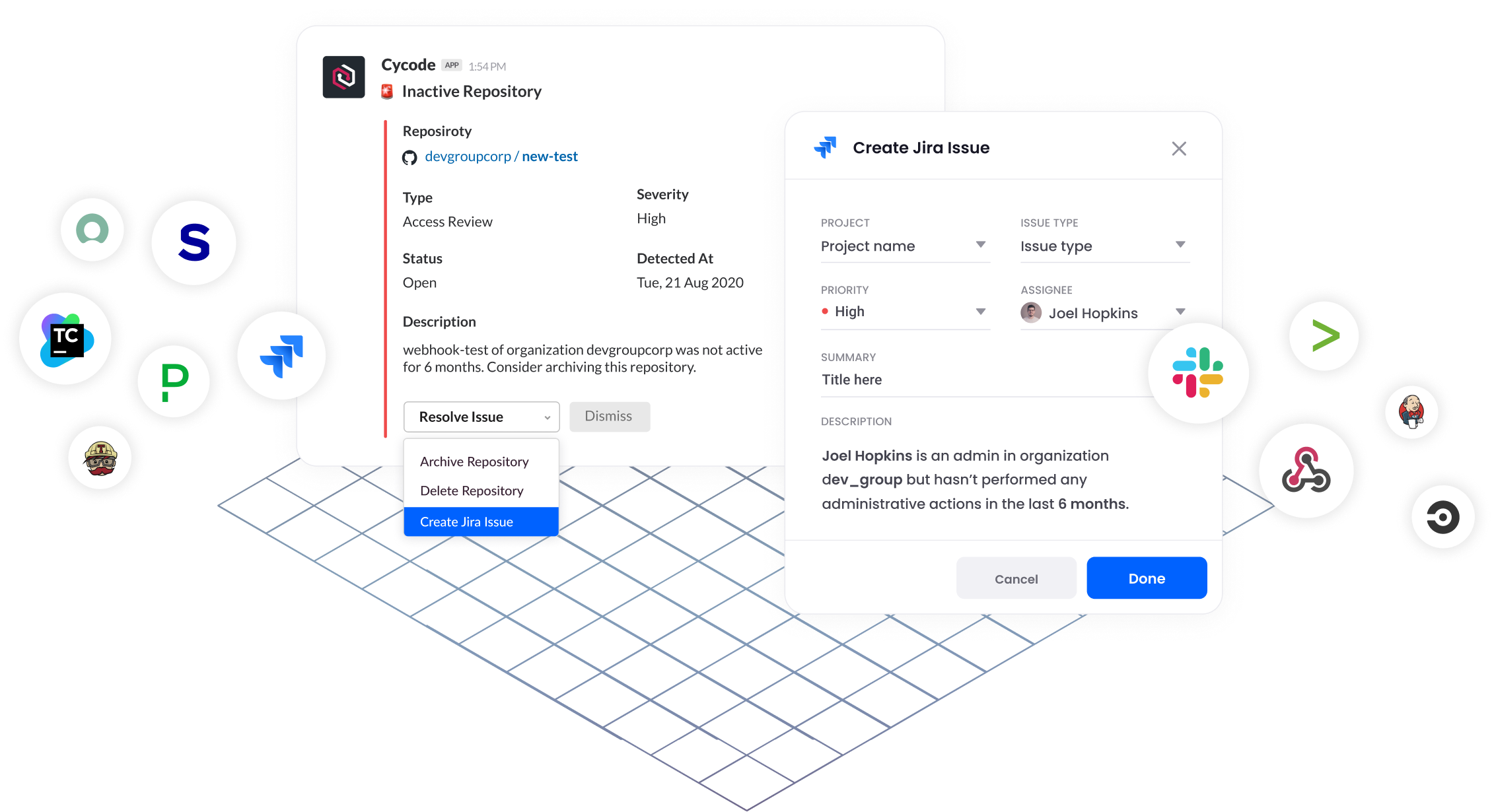
Pre-Built Integrations
for Seamless Workflows
Cycode integrates with all major issue tracking, ticketing, SIEM and alerting tools to seamlessly integrate with pre-existing developer workflows across all of your SCMs, IaC and production systems, regardless of programming language.
Get started with Cycode today.
