The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program serving as a framework for security assessment, authorization, and continuous monitoring for cloud products and services. FedRAMP compliance provides security guidance to federal agencies and organizations accountable to federal standards, helping protect national information.
What is FedRAMP Compliance?
The FedRAMP guidance unlocks modern cloud technologies and helps accelerate national agencies’ adoption of secure cloud solutions by providing a standardized approach to security assessment, authorization, and continuous monitoring.
FedRAMP uses the National Institute of Standards and Technology’s (NIST) 800-53 guidelines and procedures to provide standardized security requirements for cloud services. Implementing FedRAMP yields several benefits:
- Reduces duplicative efforts, misconfigurations, and inefficiencies throughout the SDLC.
- Accelerates the adoption of cloud computing by creating transparent standards and processes for security authorizations.
- Empowers agencies to leverage security authorizations on a government-wide scale.
- Promotes innovation and the advancement of more secure information technologies through public-private partnerships.
Private sector cloud service providers may also choose to adhere to FedRAMP standards. This implements federally mandated best practices and unlocks a new distribution channel. Cloud service providers achieving FedRAMP compliance may earn a spot on the FedRAMP Marketplace.
All cloud service providers must meet the FedRAMP security requirements to have the U.S. Government as a customer. These requirements include the FedRAMP Security Assessment Framework.
FedRAMP Security Assessment Framework
The FedRAMP Security Assessment Framework creates four process areas based on the baseline controls introduced in NIST SP 800-53. However, these categories contain additional controls designed to enhance security requirements. These controls may be detailed within the FedRAMP Security Controls Baseline–click here to download them.
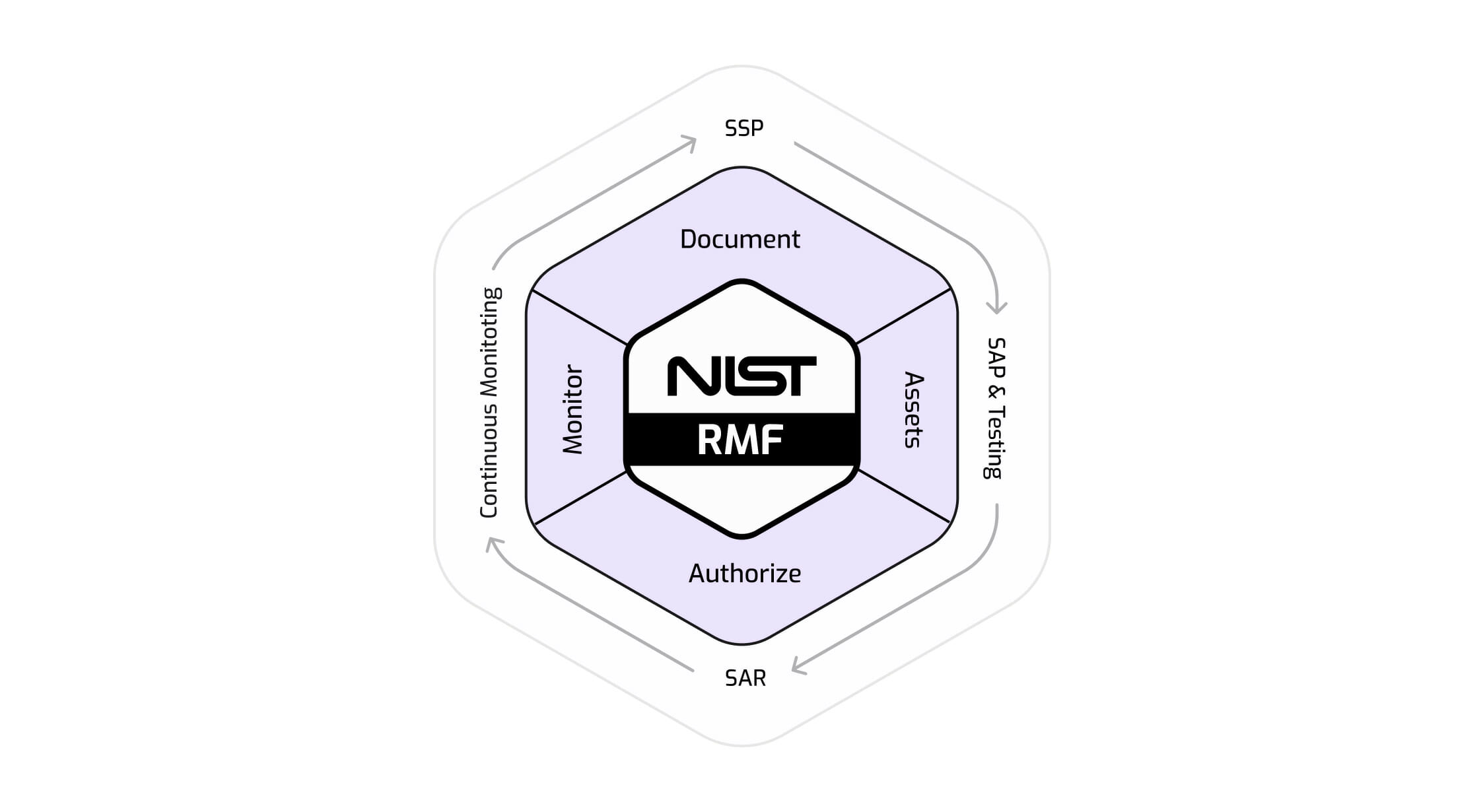 Document
Document
Documenting within the context of the FedRAMP Security Assessment Framework entails categorizing the information system, selecting security controls based on the categorization, and implementing the controls while recording the system design decisions to create a System Security Plan (SSP). The SSP helps inform stakeholders and future users how the system is architected, what the system boundaries are, and how the supporting infrastructure for the system looks. Interested cloud service providers may find templates for creating an SSP on the FedRAMP website.
Cloud service providers must select a FedRAMP security controls baseline corresponding to the FIPS PUB 199. FedRAMP requires each cloud provider to submit a package of supporting documents along with their SSP to ensure compliance with these baseline security controls.
Assess
Cloud service providers must demonstrate that security controls are implemented as described in the SSP. An independent assessor must perform this certification to avoid “the fox watches the henhouse” situations. Ideally, the assessing party will be a FedRAMP accredited 3rd-party assessment organization; however, this requires proof of the independent assessor’s independence, qualifications, and thoroughness.
When evaluating a cloud system, the FedRAMP compliance assessment must utilize the FedRAMP baseline security test cases. These cases include security testing of the system, as outlined in a Security Assessment Plan developed by the assessing organization.
Authorize
Once the assessment phase is complete, individual agencies may make integration authorization decisions based on identified capabilities and risks of the cloud system. These results may be presented in a Security Assessment Report using the available FedRAMP template; federal agencies will use this to determine the security posture of the cloud service provider’s system.
Once the Security Assessment Report is delivered, the cloud service provider shall develop a plan to identify specific vulnerabilities. This Plan of Action and Milestones document, based on the respective FedRAMP template, serves as a tracking system containing a backlog of scheduled improvements.
One of the primary benefits of FedRAMP is the ability for Agencies to reuse authorization packages and leverage cloud service providers that have earned FedRAMP compliance certification. Suppose a cloud service provider’s risk posture is acceptable to an agency. In that case, they may use the service once an “authority to operate” letter has been distributed to all stakeholders–NIST’s efforts to create a standard vocabulary have undoubtedly made an impact in accelerating this evaluation process.
Cloud service providers are required to implement continuous monitoring, continue to meet the FedRAMP requirements, and maintain an appropriate risk level to support authorization. If the cloud service providers do not meet these requirements, they risk losing their clearance to work with all FedRAMP-bound clients.
Monitor
Once a cloud service provider receives FedRAMP authorization (either from the Joint Authorization Board or Federal Agency), it must implement continuous monitoring to ensure the service provider continues adhering to baseline security controls. Continuous monitoring also helps ensure transparency in the security posture of the cloud system, provides enhanced change control, and supports the implementation of contingency plans:
- Operational Visibility – cloud service providers are required to periodically submit control artifacts and perform annual reassessments.
- Change Control – cloud service providers must report significant changes that may affect the risk posture of the system and must update and submit documentation.
- Incident Response – cloud service providers must prepare incident response plans for all FedRAMP compliant systems and report incidents to affected agencies according to the system’s documented Incident Response Plan.
Continuous monitoring provides information that helps all parties make informed risk management decisions within the context of cloud services.
FedRAMP Baseline Security Controls
The FebRAMP Joint Authorization Board uses NIST SP 800-53 to create the FedRAMP required security controls. These controls contain certain modifications to address the unique risks inherent to cloud computing environments; such changes include visibility, responsibility, shared resource pooling, trust, and partitioning. These baseline security controls are as follows:
Access Control
Formalize procedures to facilitate the implementation of access control policies.
Awareness and Training
Focus attention on security and produce relevant and needed security skills and competency training.
Audit and Accountability
Ensure there are sufficient controls in place to provide auditable evidence for system transactions and that key records are available for a sufficient amount of time.
Security Assessment and Authorization
Evaluate the management, operational and technical controls of the application and system to ensure that the security controls are adequate, configured properly, and satisfy the NIST standards.
Configuration Management
Cloud service providers can execute the management and control of configurations for an information system to ensure all IT Assets are documented with their known interdependencies and relationships so that change management, impact analysis, and compliance activities are possible.
Contingency Planning
Creating and maintaining a plan for disaster response, backup operations, and post-disaster recovery to ensure the availability of critical resources and to facilitate the continuity of operations in an emergency.
Identification and Authentication
The ability to uniquely identify a user or application within a cloud service system is the core of identity. The ability to prove that a user or application is who they claim to be is the role of authentication within a cloud service provider’s system.
Incident Response
Documenting a predetermined set of instructions or procedures to detect, respond to, and limit consequences of malicious cyber attacks against an organization’s information systems.
Maintenance
Any single or routine act that prevents the failure or malfunction of equipment or restores its operating capacity may be considered maintenance. Maintenance includes security updates, physical repair, and similar remediating actions taken on the physical or virtual components of the system.
Media Protection
The security of media storage, including who can access the stored content, how cloud service providers control the transportation of storage media, and the safe use of storage devices, falls within media protection.
Physical and Environmental Protection
Includes measures taken to protect systems, buildings, and related supporting infrastructure against threats, both human and of nature, associated with their physical environment.
System Security Planning
A formal document that provides an overview of the security requirements for an information system and describes the security controls in place or planned for meeting those requirements.
Personnel Security
Personnel security involves assessing individuals’ conduct, integrity, judgment, loyalty, reliability, and stability for duties and responsibilities requiring trustworthiness.
Risk Assessment
Risk assessment entails the process of identifying risks to organizational operations, organizational assets, individuals, other organizations, and the nation resulting from the operation of a system.
System and Services Acquisition
Includes all stages of acquiring product or service, beginning with the process for determining the need for the product or service and ending with contract completion and closeout.
System and Communications Protection
Communications protection entails controlling the flow of information and protecting the flow of information to protect against tampering, exfiltration, and other threats.
System and Information Integrity
System and information integrity are made possible through security best practices concerning system configuration, safety, and error handling.
The Key to FedRAMP Compliance
Cloud service providers can achieve FedRAMP compliance through adequate planning, assessment, and monitoring. As part of their compliance efforts, organizations must take inventory of all the assets within their SDLC, ensure compliance with each component, and impose strong governance over all these assets to adhere to FedRAMP requirements.
How Cycode Can Help Cloud Service Providers with FedRAMP Compliance
The Cycode platform offers a suite of capabilities that help organizations enforce security controls as outlined in NIST 800-53 on their source, container registries, IaC configurations, cloud systems, and more. In addition, Cycode helps enforce best practices, enables audit of configurations, and ensures consistent enforcement of compliance controls across the SDLC.
Cycode includes workflows that can help ensure adherence to best practices, such as the principle of least privilege. As described in my prior blog post, workflows can be used to send alerts, create tickets, and automatically remediate cases where the configurations violate security controls as outlined in FedRAMP. For example, workflows may prescribe remediating action when Cycode detects stale admin privileges within a repository.
Schedule a demo or visit our website to learn how Cycode can help secure your software supply chains.
Further Reading:
NIST Special Publication 800-53: https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final
FedRAMP Baseline Security Controls: https://www.nist.gov/blogs/cybersecurity-insights/next-generation-security-and-privacy-controls-protecting-nations